Reports search modifiers
Special privileges requiredThis feature is only available to users with the Enterprise or Enterprise Plus module. Google Threat Intelligence allows you to perform advanced searches over the historical set of Reports & Analysis. These searches can act on basically all the metadata that we generate for collections: name, threat actor, references, urls, malware role, tags, etc.
Advanced searches can be placed in the UI in two places:
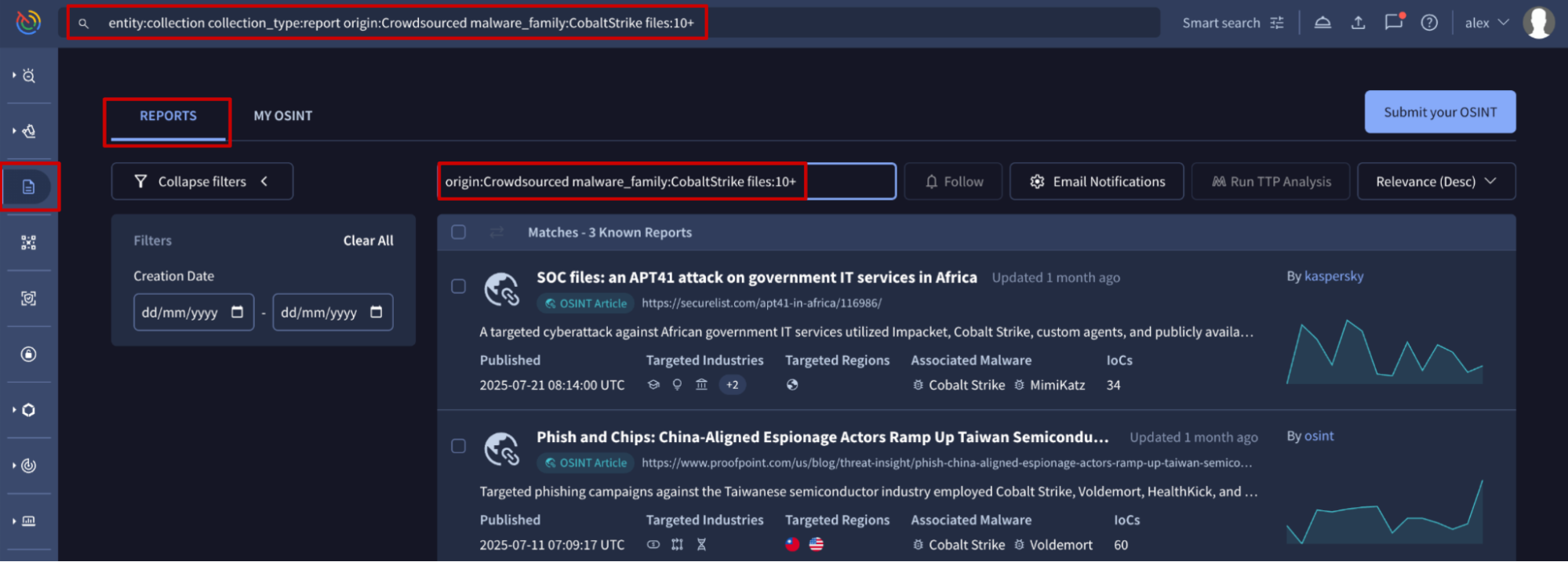
- The Reports search bar, found on the Reports & Analysis list view, allows users to perform advanced searches by using report-specific search modifiers. It is not required to specify the object type to look for, which streamlines the search process.
- The top search bar or home search bar, which is available from almost all locations in the UI, requires to specify both the search logic and the object type to look for. For reports, you would need to enter
entity:collection collection_type:reportfollowed by the rest of conditions.
The following table outlines all advanced search modifiers for reports:
| Search modifier | Description |
|---|---|
| Open free text | Text without modifiers matching against object's name or description |
name | Searches for words within the report's title. E.g.: name:lolbin |
description | Searches for words within the report's description. E.g.: description:ransomware |
creation_date | Searches for reports based on their creation date. E.g.: creation_date:2025-01-01+ AND creation_date:2025-03-01- |
last_modification_date | Searches for reports based on their creation date. E.g.: last_modification_date:3d+ (modified in the last 3 days) |
origin | Searches for reports based on their origin. E.g.: origin:"Google Threat Intelligence" or origin:Crowdsourced |
publisher | Searches for OSINT/Crowdsourced reports based on the name of the publisher. In the UI, this is displayed on the report card as "By publisher_name". If the publisher's name isn't available, the owner's name will be displayed in the UI instead. E.g.: publisher:osint |
owner | Searches for reports based on the username of the user that has created the object. If the publisher's name isn't available, the owner's name will be displayed in the UI instead. E.g.: owner:vt_reference_scraper |
report_type | Searches for reports based on their types. See available options here. E.g.: report_type:"Industry Reporting" |
source_region | Searches for reports based on the region where the threat described in the report was initiated. See available options here. E.g.: source_region:Europe, source_region:KP |
targeted_region | Searches for reports based on the region targeted by the threat described in the report. See available options here. E.g.: targeted_region:USA |
targeted_industry | Searches for reports based on the specific industry affected by the threat. See available options here. E.g.: targeted_industry:"Academia - University" |
targeted_industry_group | Searches for reports based on the specific group of industries affected by the threat. See available options here. E.g.: targeted_industry_group:Education |
operating_system | Searches for reports based on the operating system affected by the described threat. See available options here. E.g.: operating_system:windows |
malware_role | Searches for reports based on the associated malware role. See available options here. E.g.: malware_role:stealer |
motivation | Searches for reports based on the motivation of the threat. See available options here. E.g.: motivation:Espionage or motivation:Hacktivism |
threat_actor | Searches for reports based on the associated Threat Actor name (case-sensitive). E.g.: threat_actor:APT41 |
malware_family | Searches for reports based on the associated Malware Family name (case-sensitive). E.g.: malware_family:CobaltStrike |
software_toolkit | Searches for reports based on the associated Software or Toolkit name (case-sensitive). E.g.: software_toolkit:COBALTSTRIKE |
files | Searches for reports based on the number of files linked to them. E.g.: files:5+ or files:10- |
urls | Searches for reports based on the number of URLs linked to them. E.g.: urls:3+ or urls:8- |
domains | Searches for reports based on the number of domains linked to them. E.g.: domains:9+ or domains:15- |
ip_addresses | Searches for reports based on the number of IP addresses linked to them. E.g.: ip_addresses:1 |
Updated 4 months ago
