Single Sign On Authentication
Google Threat Intelligence currently supports SSO authentication with the following services:
- GitHub
- Microsoft
This means, if you have an account in any of those services, you can use it at Google Threat Intelligence too!
Login to an existing account using SSO
If you already have a Google Threat Intelligence account whose email address is also associated with an account at any of our supported SSO providers, you can login with that provider at Google Threat Intelligence too.
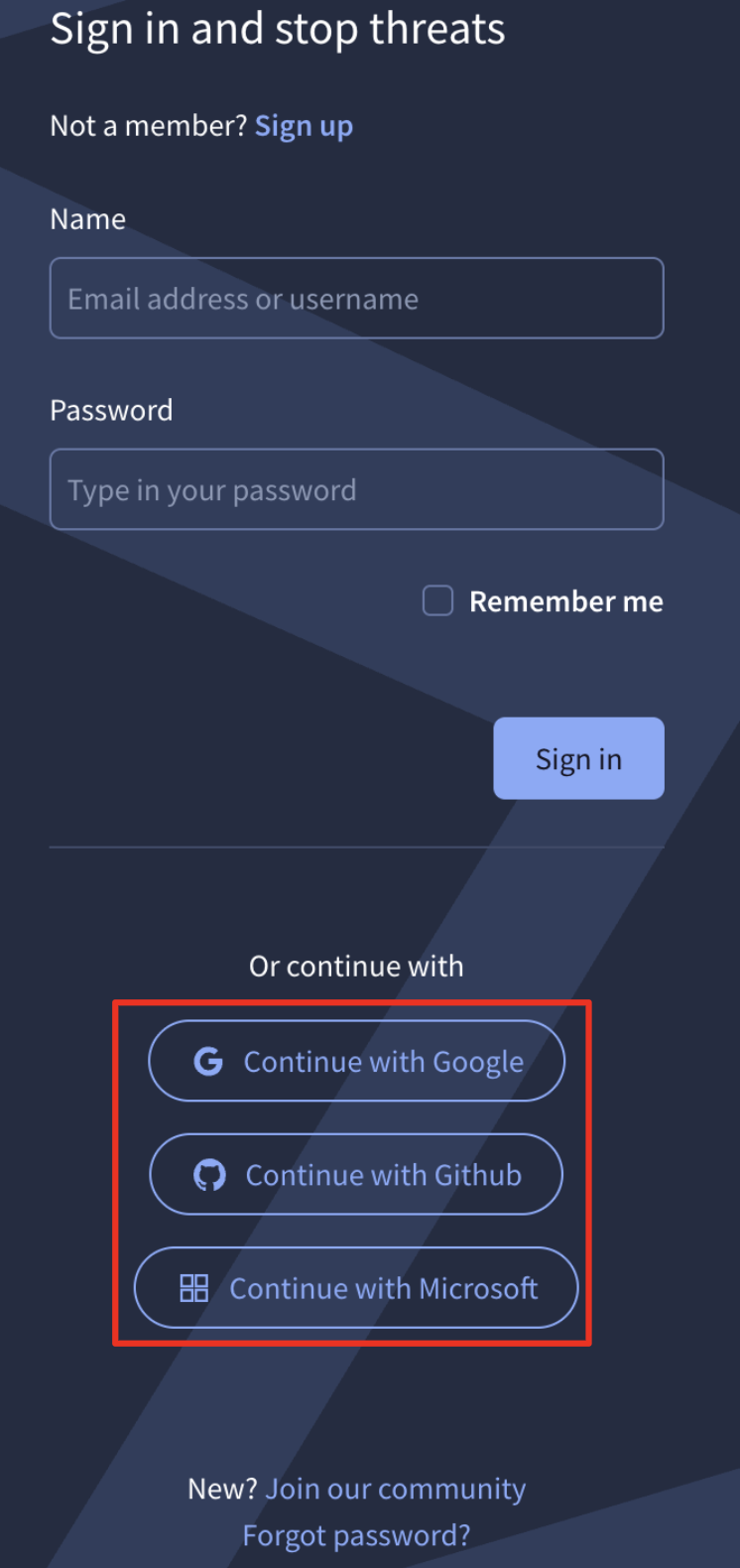
When login using SSO, no 2FA is necessary. If the login at the SSO provider is successful you’ll be automatically redirected to Google Threat Intelligence’s main page.
Group SSO settings
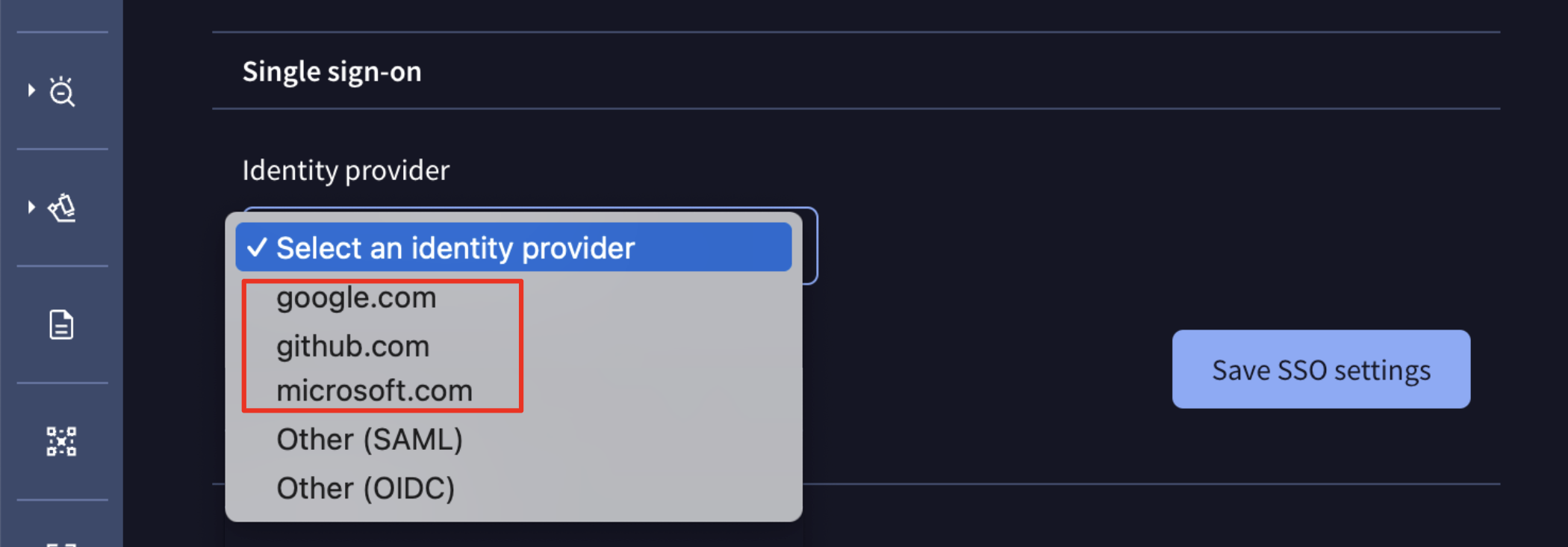
In the group settings page, a group administrator can choose among a set of already configured SSO identity providers: google.com, github.com and microsoft.com.
When any of these 3 providers is enabled for the group, all group users will be forced to authenticate exclusively through that provider. If no specific provider is enabled, users have the flexibility to sign in using either basic authentication (username and password) or SSO method if their account is linked to any of the listed services.
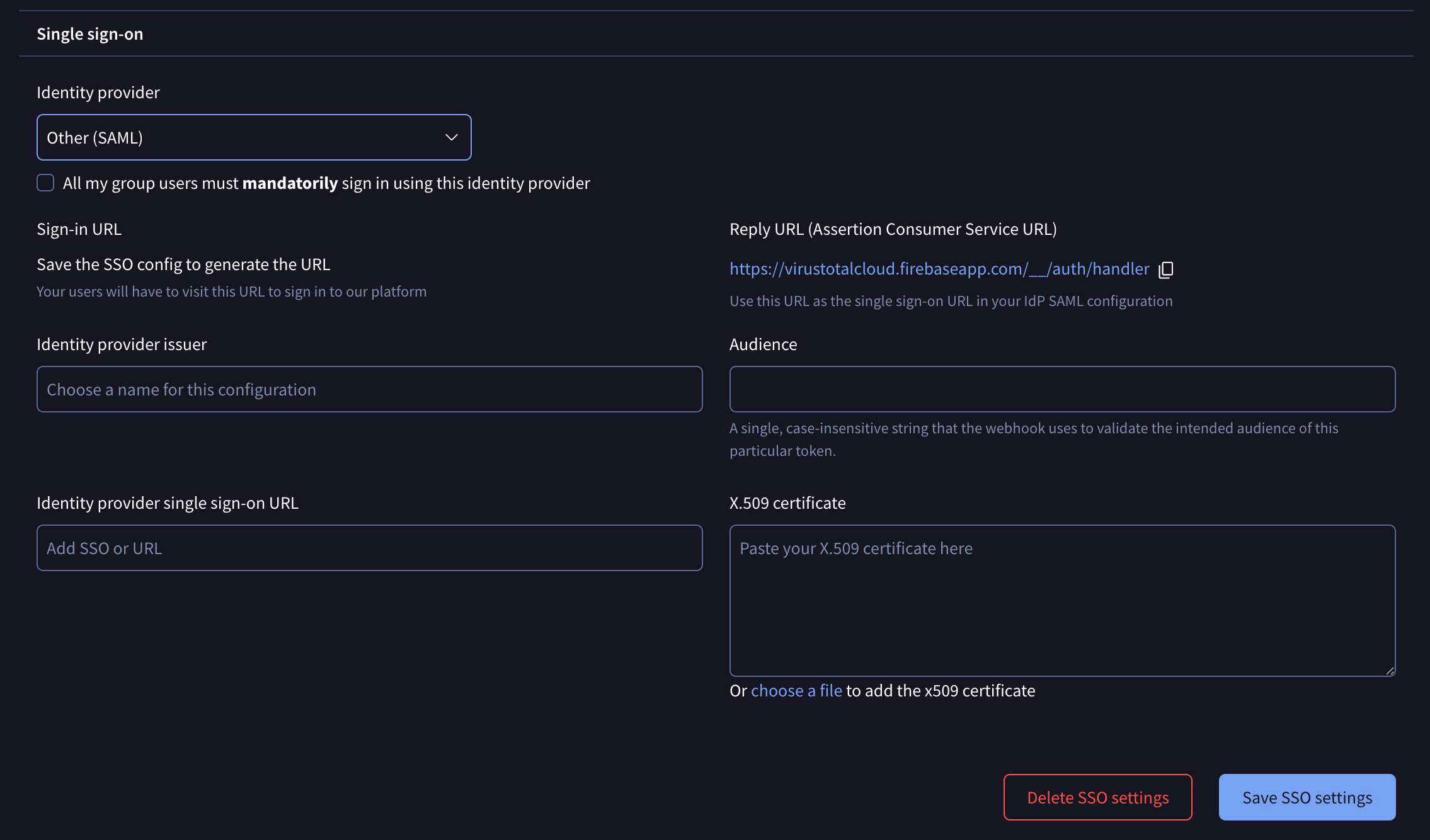
SAML
Clients with different identity providers can enable SAML for SSO by selecting that option in the drop-down menu and filling out the required details in the displayed form to complete the setup.
Please note that for forcing users to only authenticate via SAML, a checkbox is provided. If this checkbox is not selected, users can use both methods of authentication: SAML and common credentials.
We have articles with examples of how to configure SAML with Okta, configure SAML with Ping or configure SAML with EntraID
Please note that you must update rotated certificates manually in the SAML settings on the platform or via API.
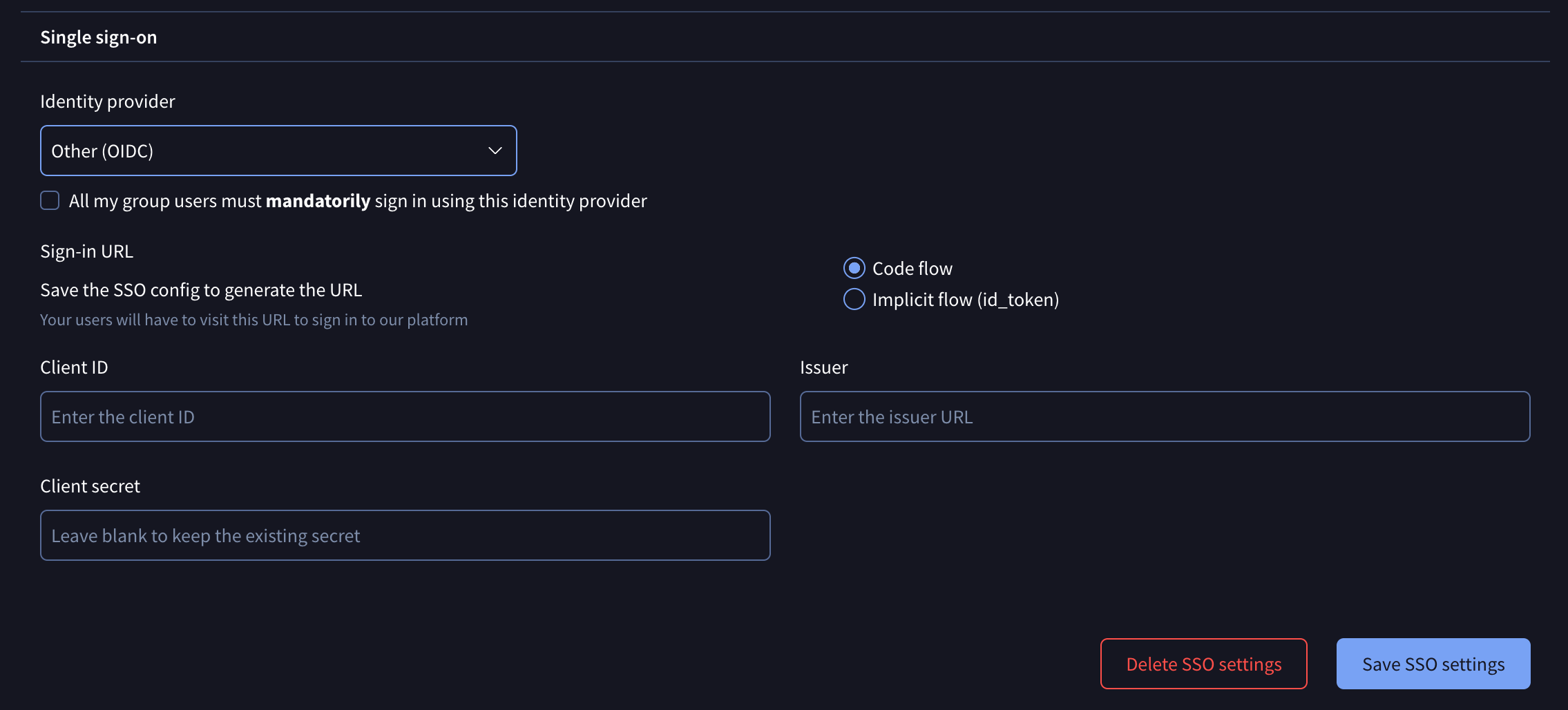
OIDC
Clients with other identity providers that prefer OIDC for SSO, can select that option in the drop-down menu and fill out the required data in the displayed form to complete the setup.
Again note that for forcing users to only authenticate via OIDC, a checkbox is provided. If this checkbox is not selected, users can use both methods of authentication: OIDC and common user/password credentials.
Updated 5 months ago
