Google Threat Intelligence for MSFT Sentinel
Configuration and use guide
Overview
Google Threat Intelligence for Sentinel integrates Google Threat Intelligence (Google TI) to enrich your security investigations with valuable context and threat information. It achieves this by deploying playbooks designed to automatically gather intelligence on indicators like IPs, file hashes and URLs from Google's extensive threat database.
Installation
Prerrequisites
This integration depends on a custom connector, this can be deployed by using the template located at Raw Json or Github
If deploy button does not work, you should deploy the custom connector by using Template Specs in Sentinel.
- Download
azuredeploy.jsonof the Custom Connector. - Open Template Specs in Sentinel.
- Select Import Template and select
azuredeploy.json.

- Fill in the fields and click on Review + Create.

- Click on Deploy.
Installing Playbooks
To install the Google Threat Intelligence playbooks, use the Content Hub and the provided templates.

- Navigate to the Content Hub.
- In the search bar, type and select Google Threat Intelligence.
- Click Install.
Now you have Google Threat Intelligence playbook templates ready to use it.
Creating and Configuring Playbooks
Creating Playbooks
- Navigate to the Automation Dashboard, which you can access from the Sentinel side panel.
- Click the Playbook Templates tab.
- Search for Google Threat Intelligence in the search bar.
- Click the playbook you want to use and click Create Playbook.

- Follow the steps to create a playbook.

- And click on Create Playbook.
Now the playbook is created, but we need to configure it.
Configuring a Playbook
Important: Configuring Sentinel Connections in GTI-ThreatList
You must specifically configure the connection for any actions that require interaction with Microsoft Sentinel, such as the "Threat Intelligence - Upload Indicators of Compromise (V2) (Preview)" action in the GTI-ThreatList playbook. Failing to do so will result in a 401 Unauthorized error during execution.
Follow these steps to resolve the issue:
- Open the "GTI-ThreatList" Logic App playbook in the Azure portal and switch to the Designer view.
- Navigate to the final action step: "Threat Intelligence - Upload Indicators of Compromise (V2) (Preview)".
- Select the step, then click Change connection > Add new.
- When the sign-in window appears, ensure the authentication type is set to "OAuth" and click Sign in.
- Re-authenticate using your Azure credentials (not your Google TI API key).
- Save the playbook.
Connections
- Navigate to the Active Playbooks tab and select the one you want to configure.
- Click on it and select Edit. You will see all the nodes of the playbook.

- Nodes with warnings/invalids should be configured, click on each one and configure the connection to the Google TI API.


- Click Change Connection.
- Create a new connection.

- Fill in the fields and click Create New.
You will need a Google Threat Intelligence API key.
- Use this new connection for the rest of the nodes in the playbook that have an Invalid Google TI API connection.
Sentinel Permissions
The created playbook needs Sentinel Contributor permissions to be able to edit incidents.
To install and authorize playbooks in Microsoft Sentinel, you need specific resource group permissions. While the Microsoft Sentinel Contributor and Logic App Contributor roles provide access to Sentinel features, they don't provide the necessary resource group-level permissions.
Microsoft recommends using managed identity for playbook authorization. This method requires the user performing the installation to have either the Owner role or the Role Based Access Control Administrator role for the resource group. This approach increases security by allowing playbooks to run without relying on user credentials.
- In the Log Analysis workspace of your instance.
- Navigate to Access Control (IAM).
- Add > Add Role Assignment.

- Select the Microsoft Sentinel Contributor role.
- Select your playbook as member (Search by playbook name).

- Review + Assign.
Now your playbook has the permissions for the resource group.
Using playbooks
Google Threat Intelligence playbooks can be divided in:
-
Enrichment
- Entity triggered
- Alert triggered
- Incident Triggered
-
Threat Intelligence Ingestion
- Threat Lists
- IoC Stream
Threat Intelligence Ingestion Playbooks
These playbooks add Google Threat Intelligence to your Sentinel instance. Use the Sentinel Threat Intelligence panel to view the threats.
Threat Lists
The Threat Lists playbook ingests specific categories of threat intelligence from Google Threat Intelligence into your Microsoft Sentinel instance. To use this playbook:
- Configure Categories: When setting up the playbook, you will need to specify which threat list categories you want to ingest. This allows you to tailor the intelligence feed to your specific needs.
- Enable Automation: Once configured and enabled, the playbook will automatically trigger every hour. It will fetch the latest threat intelligence from the selected categories.
- View Ingested Threats: The ingested threat intelligence data can be viewed and analyzed within the Microsoft Sentinel Threat Intelligence panel. This provides a centralized location to see the threats that have been imported from Google Threat Intelligence.
For more detailed information on available threat list categories and their specifics, please refer to the Threat Lists Documentation.

IoC Stream
The IoC Stream playbook continuously ingests Indicators of Compromise (IoCs) from Google Threat Intelligence into your Microsoft Sentinel Threat Intelligence. Due to the continuous nature and potential volume of data, this playbook has specific prerequisites and configuration considerations.
Prerequisites:
- Azure Storage Account: You must have an Azure Storage Account prepared.
- Purpose: This storage account is used by the playbook to save the timestamp of its last execution. This ensures that in subsequent runs, it only fetches new IoCs since the last successful ingestion, preventing duplication and data gaps.
- Table Name: The playbook will store this timestamp in a table named
GoogleThreatIntelligencewithin the specified storage account.
- Storage Table Data Contributor This playbook will need this role to read/write in Table Storage
Playbook Configuration:
IMPORTANT: User-Specific ConfigurationThe API key used for the connection is user-specific. The IoC Stream is tied to a particular user's subscriptions in Google Threat Intelligence (such as collections, threat actors, and hunting rulesets).
When configuring this playbook, you must use the API key belonging to the user account that has the desired IoC Stream subscriptions. The playbook will only ingest IoCs from that specific user's stream. This integration does not support group-level API keys or subscriptions.
-
Storage Account Configuration:
- During the playbook setup, you will need to provide the name of your Azure Storage Account.
- The playbook is designed to automatically create the
GoogleThreatIntelligencetable within that storage account if it doesn't already exist.
-
Recurrence Interval (Recurrence Node):
- The playbook includes a "Recurrence" node that determines how frequently it runs to fetch new IoCs. This can be configured to suit your needs.
- Important Consideration for High-Volume Streams: If you are ingesting IoC streams known for high data volume, it is crucial not to set a very wide interval between playbook runs (e.g., once every 24 hours for a very active stream).
- Reasoning: A long interval for a high-volume stream can result in the playbook attempting to fetch an extremely large dataset in a single request. This may lead to timeouts, request failures, or potential loss of IoC information due to the sheer volume. Shorter, more frequent intervals are recommended for such streams to ensure reliable ingestion.

Once all connections are validated and the necessary configurations (like the Storage Account name and appropriate recurrence) are set, and the playbook is enabled, it will begin ingesting IoCs. These will then be available in the Microsoft Sentinel Threat Intelligence panel.
Filtering the IoC Stream
You can customize the IoC Stream playbook to ingest only specific types of IoCs by using the filter parameter. This is useful for tailoring the threat intelligence feed to your specific monitoring needs, reducing noise, and focusing on the most relevant threats. The filter is configured within the playbook's logic, specifically in the "Get IoC Stream lists" action.
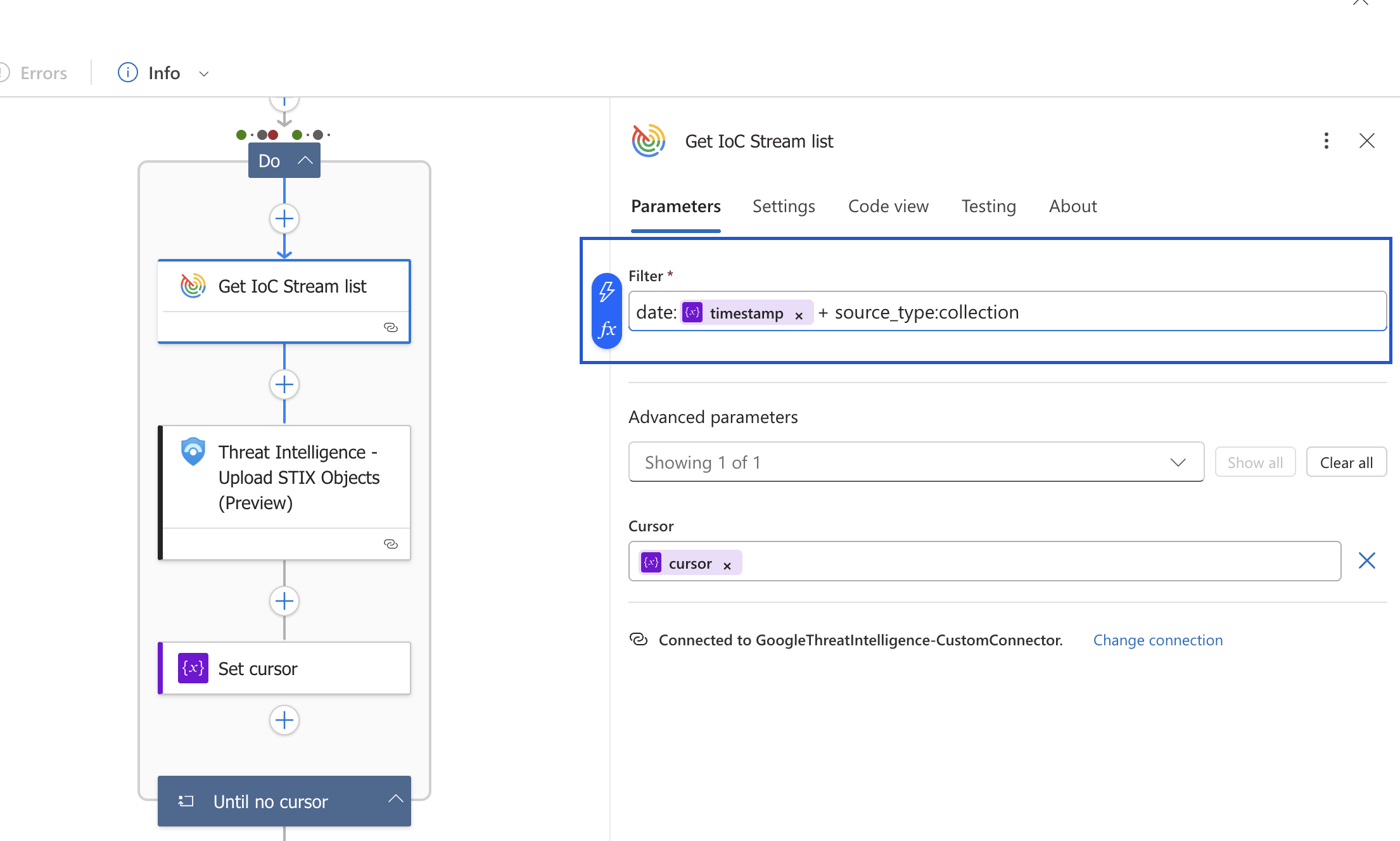
As shown in the image, the filter field is a string where you can add your query. By default, the playbook includes a date filter that is dynamically updated to fetch only new IoCs since the last successful run. You can append additional filters to this query to further refine the data you ingest.
Available Filters:
- date:2023-02-07T10:00:00+: Returns objects from notifications generated after the specified UTC timestamp.
- date:2023-02-07-: Returns objects from notifications generated before the specified UTC timestamp.
- origin:hunting: Returns objects from notifications coming from Livehunt. Allowed values: hunting, subscriptions.
- entity_id:objectId: Returns objects whose ID is objectId.
- entity_type:file: Returns only a specific entity type. Allowed values: file, domain, url, ip_address.
- source_type:hunting_ruleset: Filters by the type of source object that triggered the notification. Allowed values: hunting_ruleset, retrohunt_job, collection, threat_profile.
- source_id:objectId: Filters by the ID of the source object that triggered the notification (e.g., a specific hunting ruleset ID).
- notification_tag:ruleName: Filters notifications by their tags. For Livehunt notifications, this can include the rule name or the username of the ruleset's owner.
Filters can be concatenated using AND/OR keywords.
Example:
(source_type:collection or source_id:objectId) and date:2023-02-07+Enrichment Playbooks
These playbooks add comments to incidents with information about the IoCs. All enrichment comments are added to the incident comments section.
Incident triggered
- In the Incidents panel, select the incident you want to enrich.
- Click Actions > Run Playbook.

Here you will see all the entity triggered playbooks that you have deployed.
- Select the playbook you want to use and click the Run button.

Alert triggered
Cannot be triggered manually, only for automation.
Entity triggered
If you only want to enrich 1 IoC:
- In the Incident dashboard, select the incident that contains the IoC you want to enrich.
- Click View All in the Entities panel.
- Select the IoC you want to enrich.

- Click Run Playbook.
Automation
Incident Trigger and Alert Trigger playbooks can be used in an automation process.
An automation process can be found [here] (https://learn.microsoft.com/en-us/azure/sentinel/automation/run-playbooks?tabs=after-onboarding%2Cincidents%2Cazure%2Cincident-details-new).
Automation Example
Creating an Automation Rule
- Create an automation rule in the Automation Dashboard.
 This rule will be triggered when an incident is created and the GTI-IOCEnrichmentIncident playbook is run.
This rule will be triggered when an incident is created and the GTI-IOCEnrichmentIncident playbook is run.
- Configure the rule with the desired behavior.
- Click Apply.
Analytic query rule
- In the Analytics dashboard, choose Create > Scheduled Query Rule.

- Enter the rule name and the severity of incidents generated by this rule.

- In Set rule logic we will write a KQL query with our desired logic, in this example our query will match all rows in the IngestIoc_CL table.
- In the Alert Enhancement section, we define the mapping between Sentinel entities and the columns in our table.

- In Query Scheduling you can select the frequency of this rule and the date of the data included in the query.
- Once you have configured all the incident settings, in the Automated Response tab you will see the automation rules that you have created and that will be triggered by this rule.

- Once selected, simply click Review + Create.
Release Notes
Version 3.0.0
- Added Custom Connector to connect to Google TI API.
- Added enrichment playbooks to add comments to the incidents with IoC information.
Support
Copyright (c) 2025 Google. All rights reserved.
Updated about 1 month ago
