Google Threat Intelligence API key
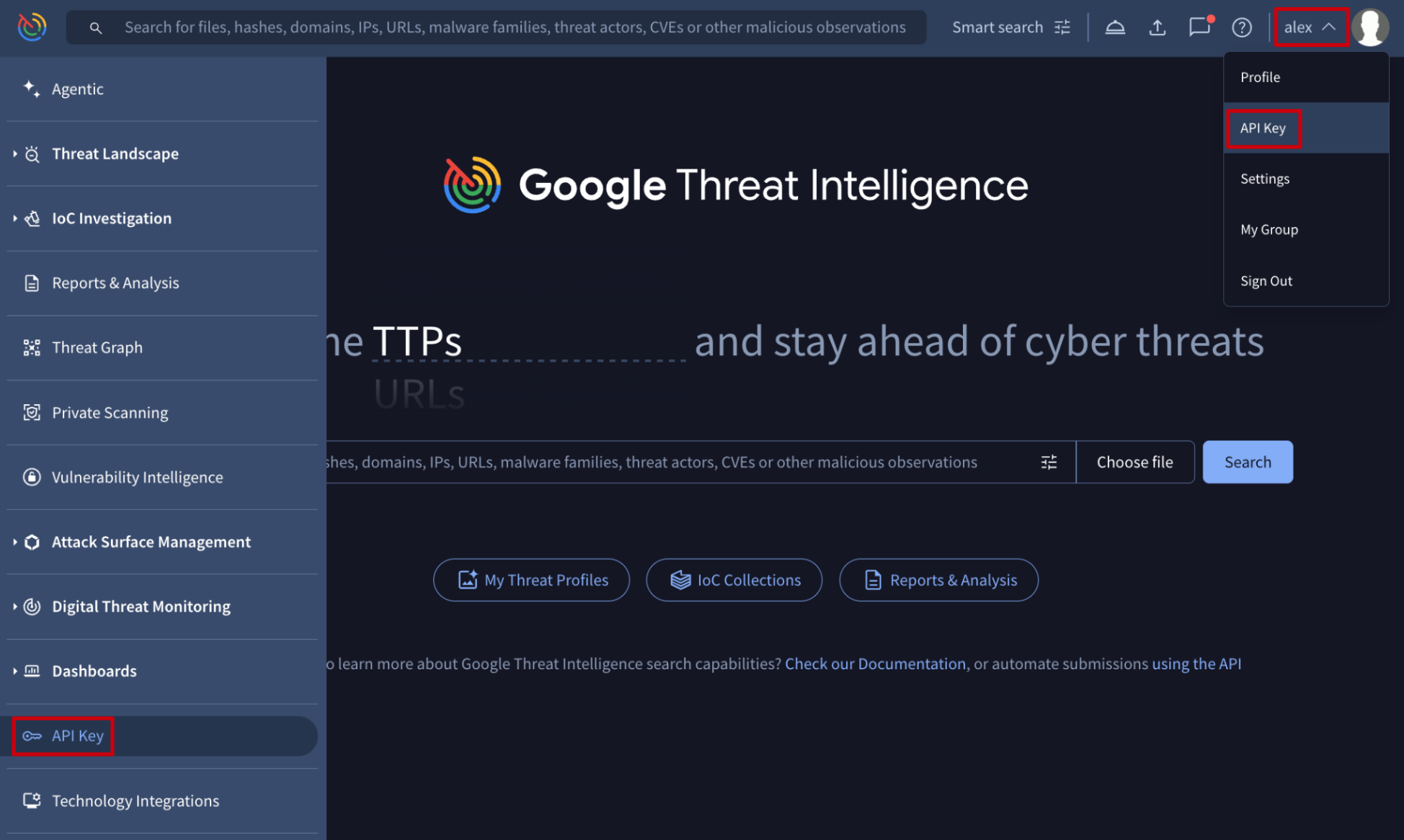
All Google Threat Intelligence users can access their API key by logging into the platform and selecting the API Key option found either in the top-right corner or via the left-hand menu or by simply accessing this link.
Your personal key will be listed in the section labeled GOOGLE THREAT INTELLIGENCE API KEY.
For integrations, Google TI group administrators can create Service Accounts and utilize their API keys instead. These are ideal because they are not tied to a specific individual and do not require email addresses or the completion of invitation forms.
Legacy Mandiant API keys
Customers using legacy Mandiant Threat Intelligence integrations must replace their existing basic authentication configuration with a Google Threat Intelligence API key. Following the migration guide, update your credentials as follows:
- API Secret (
api_secret): Replace your Mandiant API Secret with your new Google TI Service Account API key. - API Key ID (
api_key): Replace your Mandiant API Key ID with the stringgti-user.
Updated 9 days ago
