May 12th, 2025 - Threat Profile 2.0 preview, GTI integration widget, advanced network controls for Private URL scanning and more
Threat Profiles 2.0 Preview. Threat Profiles allows users to focus on the threats that matter most to them based on varying dimensions like customer’s industry, location of operation, source regions, targeted regions, etc. We have been hard at work moving Threat Profile to the new single unified UX surface, as part of that, Threat Profile is receiving major improvements:
- Complete visibility: gain comprehensive insights with automated recommendations across all GTI content, including Mandiant, partner and community intelligence.
- Enhanced collaboration: share threat profiles with your team members as editors and viewers, fostering a collaborative environment for focusing on priority threats.
- Automated operationalization: automatically generate custom IOC feeds for swift actionability, enabling focused threat hunting and detection in your environment.
- Deeper customization: tailor threat profiles with expanded dimensions such as actor motivation, source country, and malware categories, aligning with your unique threat model.
- Actionable insights: utilize the MITRE TTP analysis tool to understand tactics, techniques, and procedures (TTPs) and analyze relevant reports from Mandiant and other trusted sources.
- Workflow automation: leverage API accessibility to create, manage, and set up alerts for changes to your threat profiles.
- Unlimited profiles: Google TI Enterprise and Enterprise+ tiers now enjoy unlimited threat profiles.
The new threat profile is accesible here, we are early in the journey and are looking for for feedback to continue shaping the evolution of GTI's relevance driving engine.
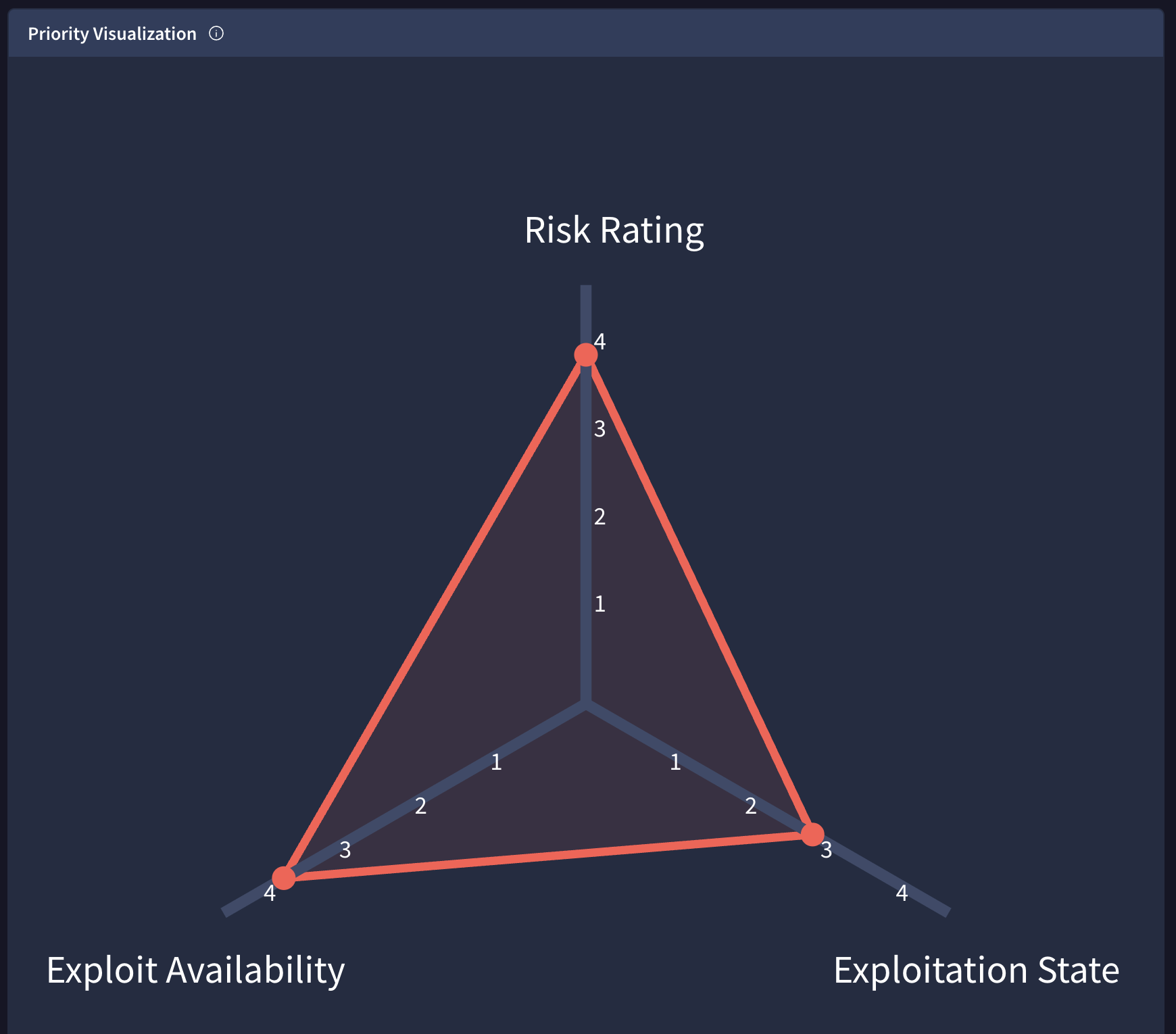
New prioritization visualization in Vulnerability Intelligence cards. GTI is a holistic threat intelligence suite that covers all use cases and data types. Its Vulnerability Intelligence modules allows users to implement smart patching programs by focusing their resources on addressing vulnerabilities that are actively being weaponized or exploited in-the-wild. Vulnerability knowledge cards now include a clear visualization communicating the risk rating. This rating is derived from factors such as in-the-wild exploitation status, exploit availability, and overall exploitation state, empowering users to make smarter, threat-driven prioritization decisions.
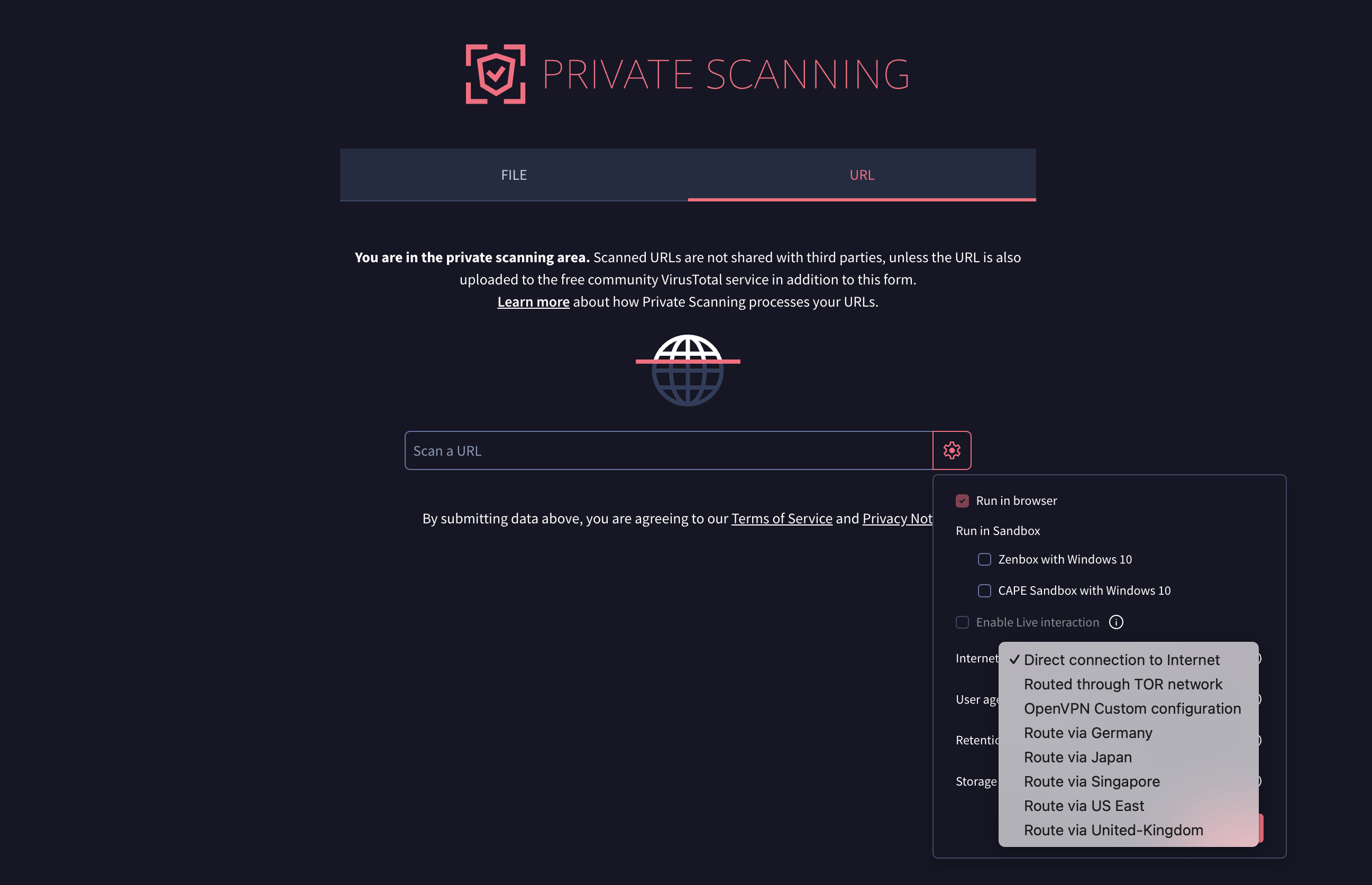
Advanced network configuration options for URL analysis. Similar to the enhanced network environment control introduced for file sandbox detonation, users can now leverage advanced Internet connection options during URL analysis in the interactive sandbox environment. This provides granular control to simulate various network conditions for comprehensive analysis and to prevent cloaking.
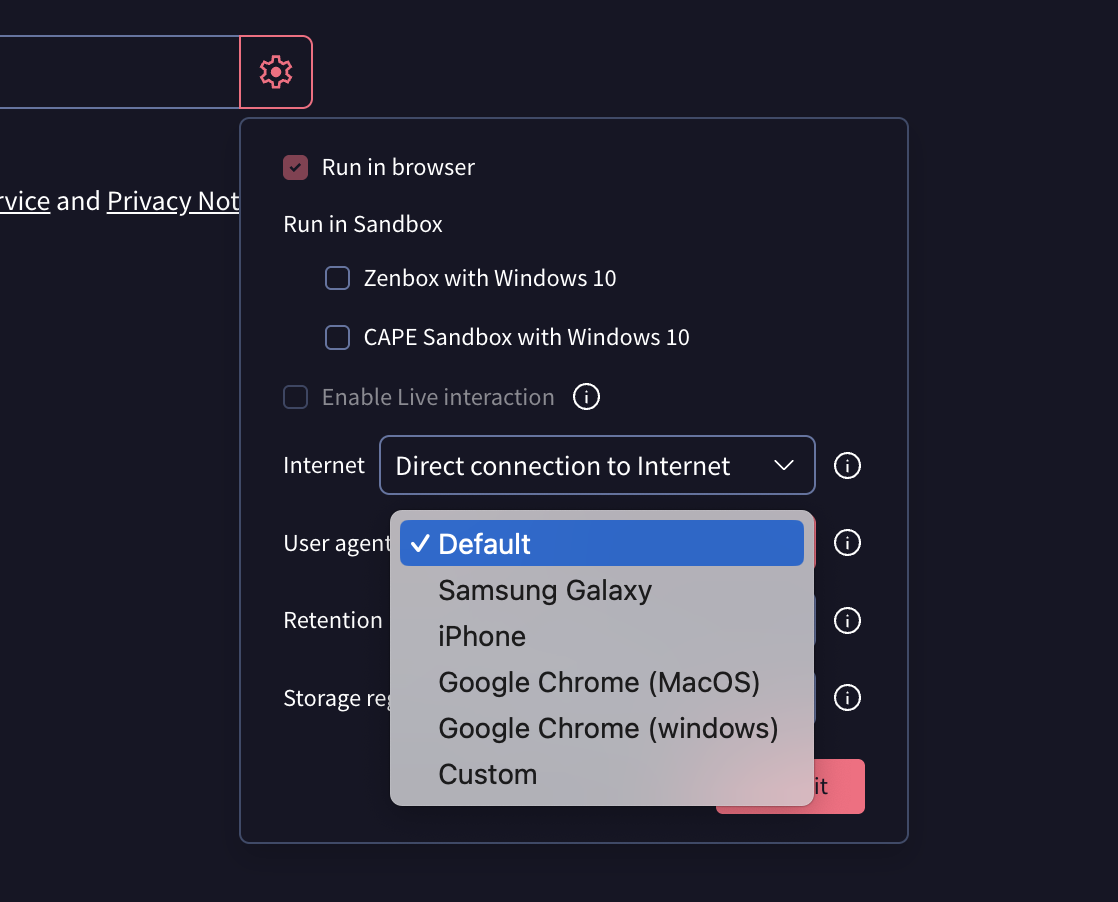
User agent selection in Private Scanning. Malicious websites or servers often present different content or behaviors to a user based on their browser "user agent" string. To overcome this common cloaking technique users can now choose among a set of user agents or provide their own custom string:
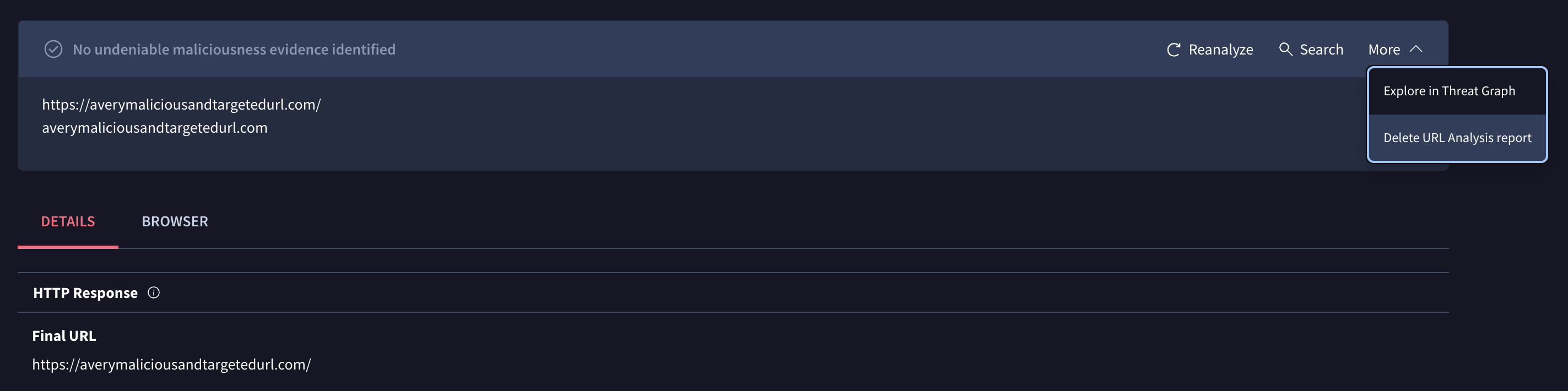
URL analysis report deletion in Private Scanning. Private Scanning allows its users to analyze URLs and files in a non-shareable fashion, including reputational analysis, static analysis, dynamic analysis in sandboxes and vetting with {YARA, Sigma, IDS} rules. User's have always been able to delete both scanned files and their associated reports at any point in time, including before their TTL specified at upload time. Users can now also delete submitted URLs at any time post-submission.
Google Threat Intelligence MCP Server for Google Unified Security. At RSA 2025 we announced the open-sourcing of MCP servers for Google Unified Security. As part of such announcement we released runnable Python MCP server examples for Google Threat Intelligence, providing standardized AI access to Google's frontline threat intelligence on indicators of compromise, threat actors, and campaigns. You can find the GitHub repository here, it includes the Google Threat Intelligence MCP server. It was never easier to build workflows leveraging our vast intelligence.
Google Threat Intelligence integration widget for third-party products / interfaces (Preview). Inspired by VirusTotal's VT AUGMENT widget, the GTI widget is an official, compliant, and recommended way to integrate VirusTotal data into third-party applications. Essentially, it's a tool that allows developers and security vendors to embed the rich threat intelligence and analysis capabilities of Google Threat Intelligence directly into their own platforms, security products, or dashboards. Forget about engineering heavy lifting to enrich indicators of compromise (IPs, URLs, domains, files / hashes), GTI seamlessly serves a UI component that is ready to be integrated in 3rd-party interfaces, this component can be custom styled to match your own interface.
Access a demo of the GTI widget here.
Generating the GTI widget is exclusively available to GTI customers. The process involves two steps: first, an ephemeral URL must be generated, and second, this URL is then used within your user interface.
GET https://www.virustotal.com/api/v3/gtiwidget?query=630325cac09ac3fab908f903e3b00d0dadd5fdaa0875ed8496fcbb97a558d0daWhere the query can be a sha256 file hash, a domain, an IPv4 address or an url. This step is usually done in the 3rd-party product backend and it requires a GTI API key to call the endpoint. Response example:
{
"data": {
"id": "630325cac09ac3fab908f903e3b00d0dadd5fdaa0875ed8496fcbb97a558d0da",
"type": "file",
"url": "https://www.virustotal.com/gtiwidget/ABMXx8NjMwMzI1Y2FjMDlhYzNmYWI5MDhmOTAzZTNiMDBkMGRhZGQ1ZmRhYTA4NzVlZDg0OTZmY2JiOTdhNTU4ZDBkYXx8ZmlsZXx8djN8fDE3NDI5ODAzMjF8fDY5ZjZlYjI4ODNiNDdiOTc0ZjJkZGExMjU0OGJhNjkyMzdjODY1NTA1NzM0NDA1ZmJhZTdhNDAwNTRjMTY1OWU"
}
}This URL is valid for 24 hours and does not require any kind of authentication to call it.
The second call involves embedding the widget in your own interface via an iframe:
For optimal display of the widget, a width of 900px is recommended. The widget includes both dark and light themes. The dark theme is the default. To use the light theme, include the query parameter theme=light in the API call. Similarly, the widget allows advanced style customization. Please reach out to us should you want to dive deeper into the GTI widget during this preview phase.
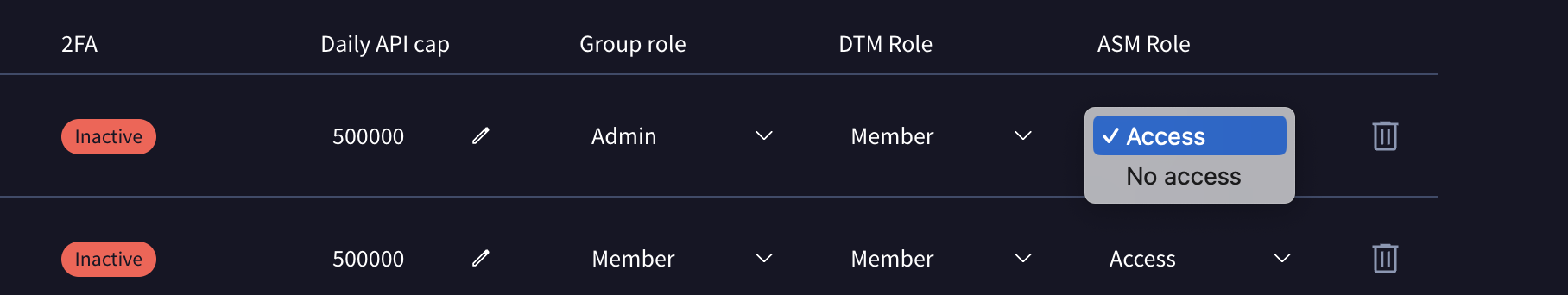
RBAC controls: ASM NO ACCESS GTI is a vast suite addressing all threat intelligence use cases, including Digital Risk Protection and Attack Surface Management. Indeed, Attack Surface Management is eventually the module that allows us to understand your Internet exposed assets and identify which threats should matter the most based on this understanding. We do acknowledge that attack surface management is not always a responsibility of CTI teams and may often identify sensitive information such as exploitable assets. To adhere to strong security practices and enforce the principle of least privilege, we are rolling out a new RBAC control to restrict access to ASM.