October 28th, 2024 - Extended dimensions of Threat Profile customization, JA4 fingerprinting, GTI score matching and more
Detection Highlights. Mandiant is enhancing Google Threat Intelligence's detection capabilities by integrating Yara rules and malware configuration extraction. Our configuration extraction team currently supports 400+ malware families and is constantly expanding this support to include new families discovered through Mandiant investigations (IR, underground monitoring, OSINT exploration, etc.). These families surface as malware profiles and IoC associations in product. In September, the team added support for BASTA, PALEBEAM, HAVOCDEMON, and XMRIG, and updated plugins for BOLDBADGER, DONUT, and TOUGHROW. We will continue to keep you informed as we roll out new configuration extractors and Yara rule integrations.
Google Threat Intelligence score searches and YARA matching. Google Threat Intelligence is an opinionated solution, we produce a maliciousness verdict, threat severity score and human readable assessment for every IoC that we see. This opinion brings together multiple proprietary systems into a single determination: the GAVS Google Antivirus engine that acts on systems such as Drive or GMail, Google Safe Browsing, Google Web Risk, Gemini Code Insight, VirusTotal metadata, threat actor/malware/campaign associations, Mandiant analyst investigations, etc. We've made the GTI score searchable and it can now be combined with the myriad of facets that allow you to go from property to IoCs sharing it, example: type:docx AND behaviour:powershell AND gti_score:30+. Similarly, the GTI score is now exposed in Livehunt for matching with YARA rules:
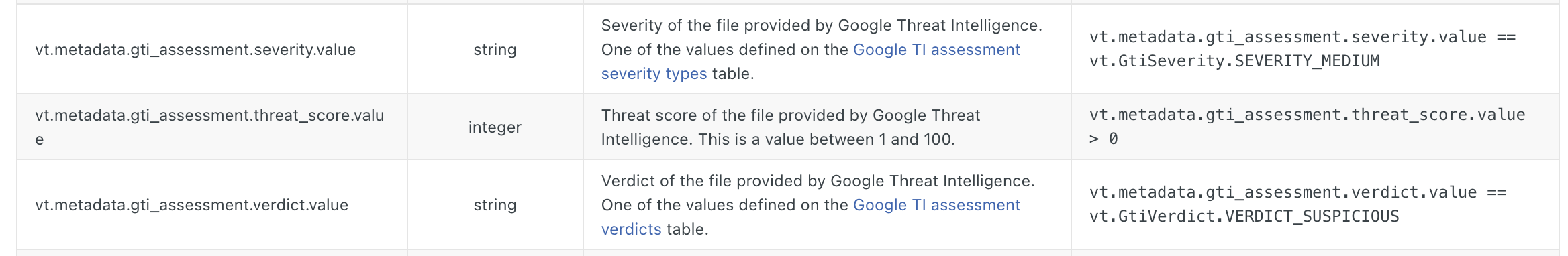
This effectively allows users to create tailored custom IoC threat feeds based on Google's curated threat data, for instance, high scores will be indicative of associations to threat actors as assessed by Mandiant / the Google Threat Intelligence Group.
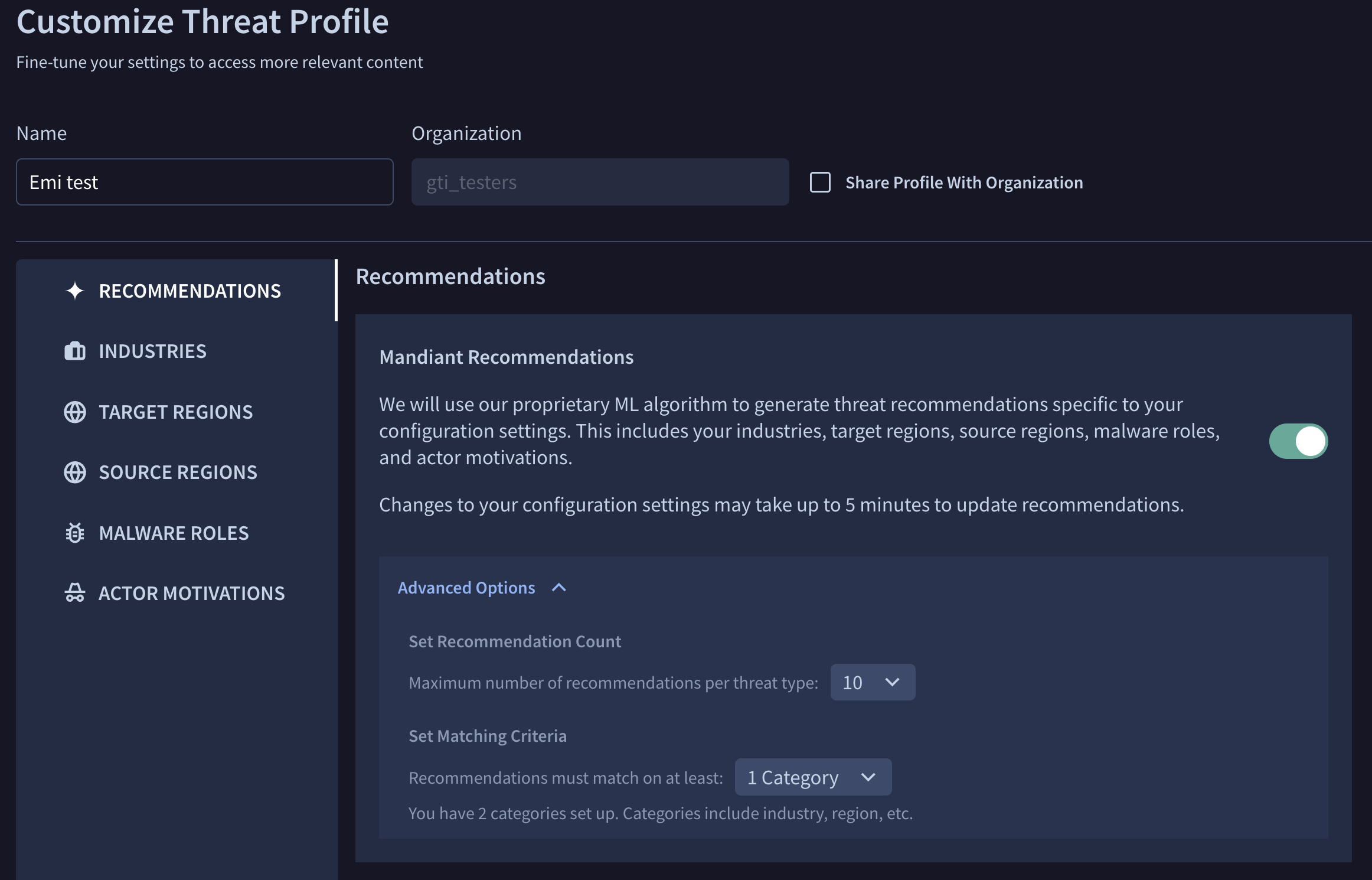
Threat Profile recommendation and customization enhancements. Threat Profile allows Google Threat Intelligence users to customize what matters most to them and focus on relevant threat actors, malware, campaigns, vulnerabilities, etc. We are now giving customers more deterministic levers to surface threats that matter to them.
- Customize the categories that must match within your Threat Profile. Default is that there must be an interest match within at least one category. A narrower view would be configuring to "must match at least 2 categories". Categories historically included industry and target region – stay tuned for new customization options soon, hint in the screenshot!
- Enhanced expectation setting during Threat Profile customization, such as showing the customer where there will be limited results and offering an opt-in option to broaden the scope.
- Finally, we have better aligned the logic to customer expectations, surfacing "up to" a maximum number of threats in the Threat Profile view.
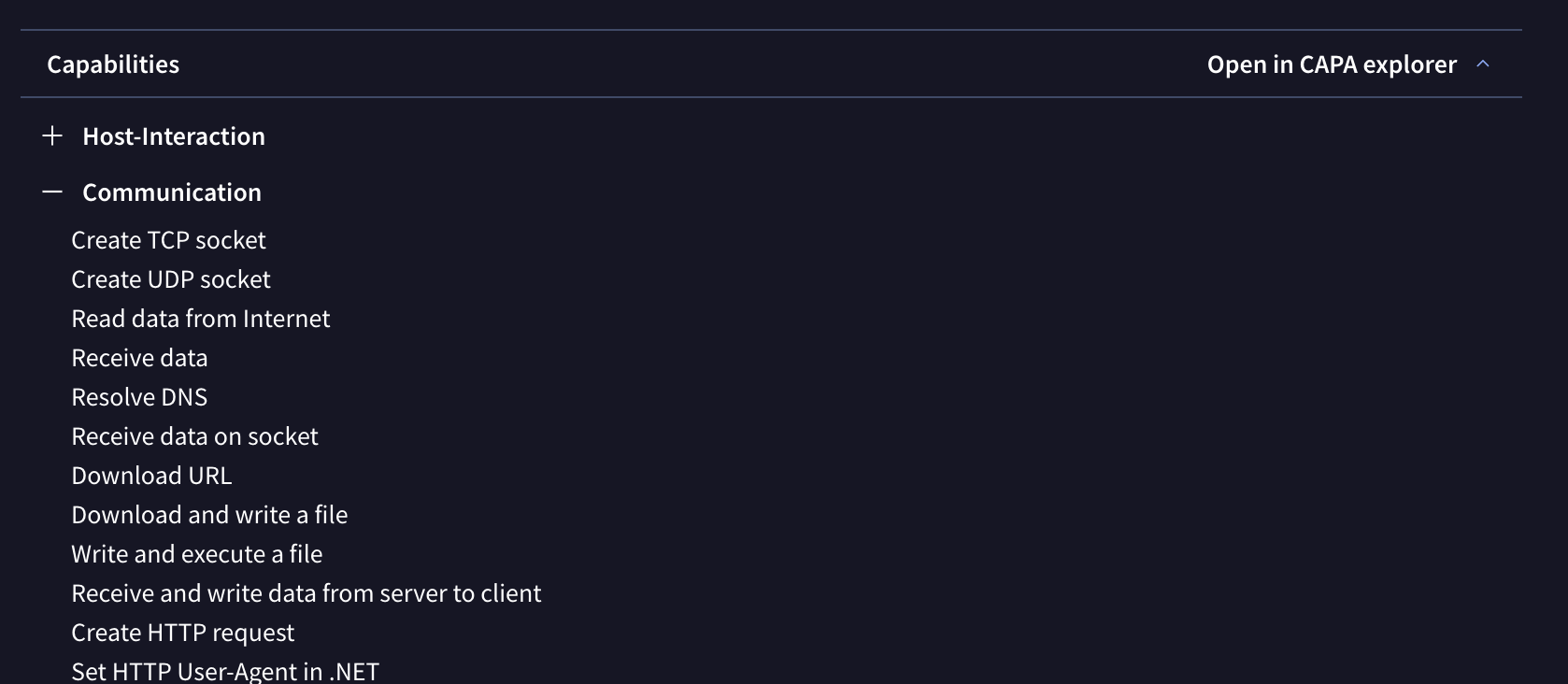
Capa Explorer. Google Threat Intelligence not only analyzes files, domains, IP addresses and URLs with multiple antivirus vendors and blocklists, we also run a myriad of home-grown, open source and 3rd-party tools on these artifacts, including dynamic analysis sandboxes. One such analysis system is Mandiant capa, which provides a framework for the community to encode, recognize, and share behaviors that have been seen in malware to figure out what a program does. The FLARE team recently rolled out capa Explorer Web, a browser-based tool to display the capabilities found by capa. The capa Explorer Web UI provides an intuitive and interactive way to visualize the capa analysis results. We've integrated capa Explorer in Google Threat Intelligence and now users can directly jump into capa Explorer by following a link in the Capabilities header of file dynamic analysis behavior reports (example).
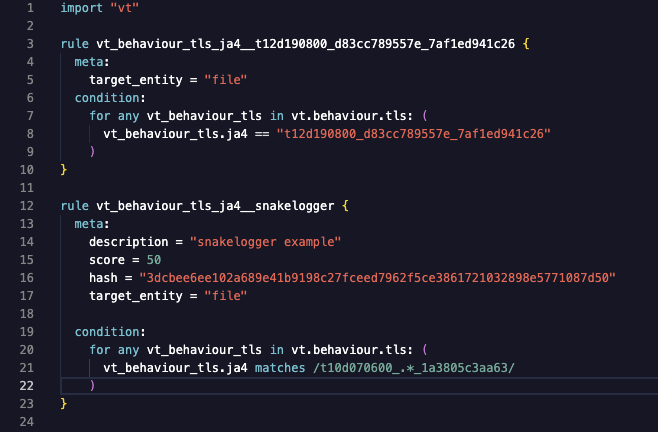
JA4 fingerprinting and reverse IoC searches over the entire threat dataset. JA4 is a suite of network fingerprinting methods that include both human and machine readable to facilitate more effective threat-hunting and analysis. The use-cases for these fingerprints include scanning for threat actors, malware detection, session hijacking prevention, compliance automation, location tracking, DDoS detection, grouping of threat actors, reverse shell detection, and many more. An increasing number of vendors such as Cloudflare or AWS are starting to offer JA4 fingerprinting and allowing their users to block on them. Google Threat Intelligence has started to produce JA4 fingerprints for TLS communications seen in the detonation of processed files in dynamic analysis sandboxes.
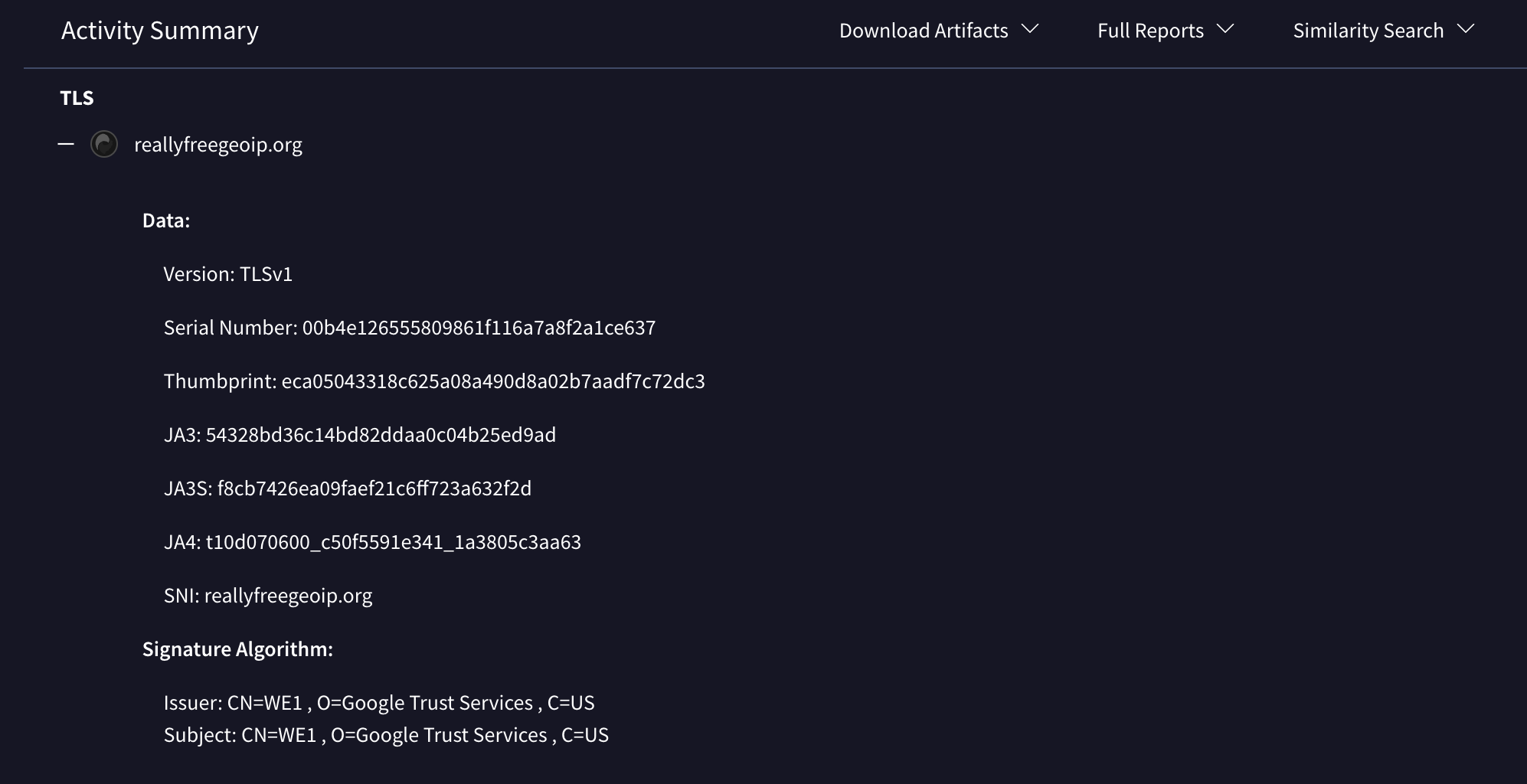
Users can also pivot over these fingerprints in order to to track and identify malicious files based on the unique characteristics of their TLS client communications, example -behaviour_network:t10d070600_c50f5591e341_1a3805c3aa63. This pivoting can power multiple use cases, for instance, getting more context in terms of the tooling and actors behind anomalous patterns seen in your network perimeter as portrayed by tools such as the aforementioned Cloudflare capability.
Our home-grown "vt" YARA module now also supports JA4 matching: