March 31st, 2025 - Live interaction with sandboxed URLs, Tor/.onion support in Private Scanning, Phishing typosquatting identification with YARA and more
Malware detection highlights. In our ongoing effort to enhance malware detection capabilities in Google Threat Intelligence, we've significantly expanded coverage this quarter. We've introduced and updated detection for over 80 key malware families with automated configuration extraction and added YARA rules for over 250 new malware families, dramatically improving the identification of existing and emerging threats. This update prioritizes malware families actively observed in Mandiant incident response engagements, SecOps customer environments, and top GTI search trends.
For example, recent Mandiant investigations led to enhanced detections for:
- CHAINVERB, a downloader that hides its download URL within a digital certificate that deploys a remote access tool on infected systems.
- ODORDAHLIA, a sophisticated backdoor used to target several industries including healthcare and construction & engineering.
- SWITCHBLADE, an evasive dropper that deploys popular backdoors and credential stealers.
We've also updated detections for prevalent threats like CobaltStrike's BEACON implant, NJRAT, and XWORM, ensuring continued effectiveness against these widely used tools. To learn how to leverage these detection capabilities for proactive threat hunting, be sure to read our recent blog post on threat hunting with malware configurations.
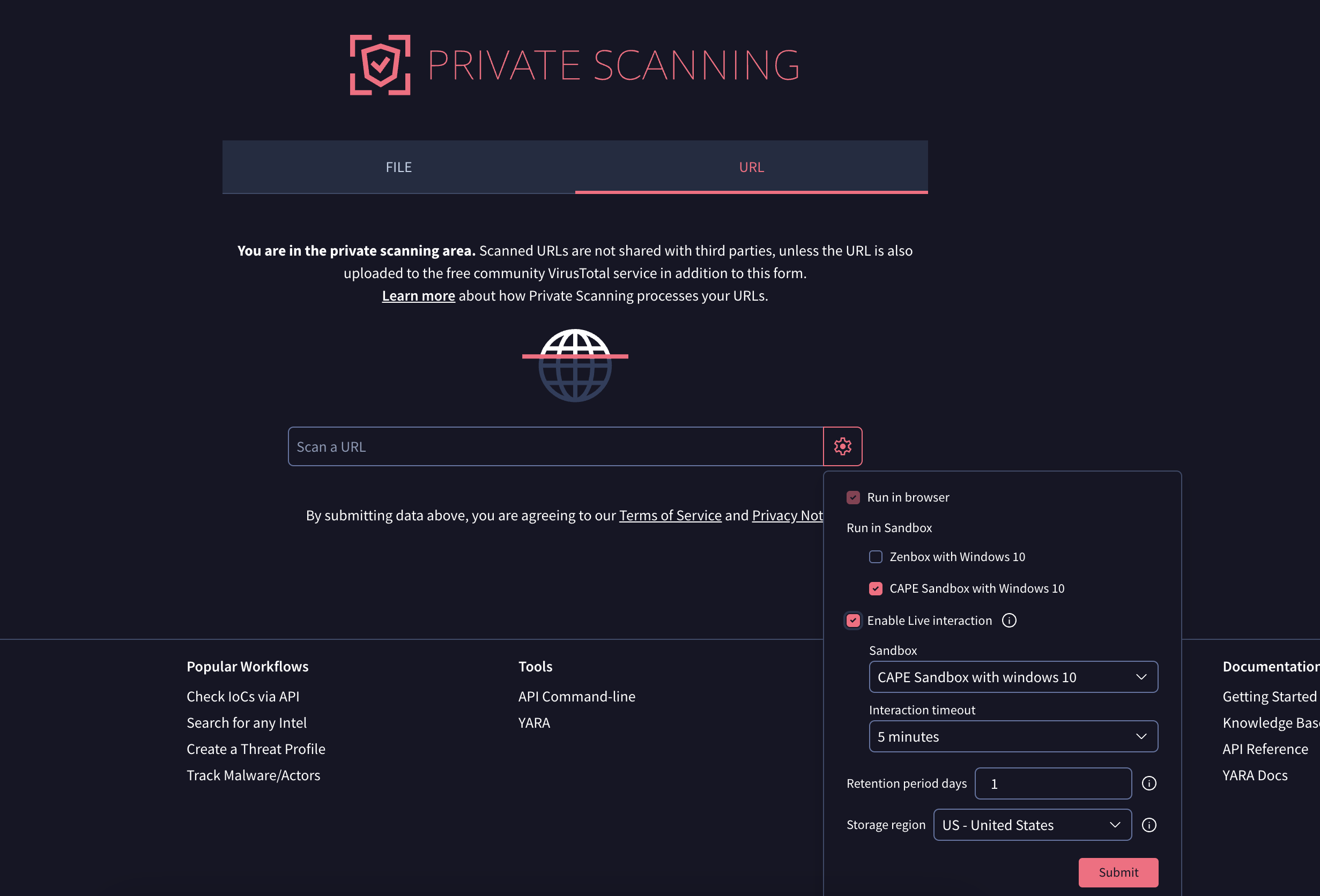
Live interaction with URLs in Private Scanning (sandbox detonation). Private Scanning allows its users to analyze URLs and files in a non-shareable fashion, including dynamic analysis in sandboxes and vetting with {YARA, Sigma, IDS} rules. We have extended this capability to allow for live interaction with URLs during sandbox detonation. This new feature builds upon the existing interactive malware analysis capabilities and enables analysts to directly interact with web pages within the sandbox environment. This allows for a more comprehensive analysis of dynamic web content, including navigating multi-step processes, solving captchas, submitting forms, and observing behavior triggered by user interaction, which may be missed by automated analysis. Similarly, it also allows analysts to visit potentially harmful content in a safe manner, without having to install local virtual machines or an analysis lab.
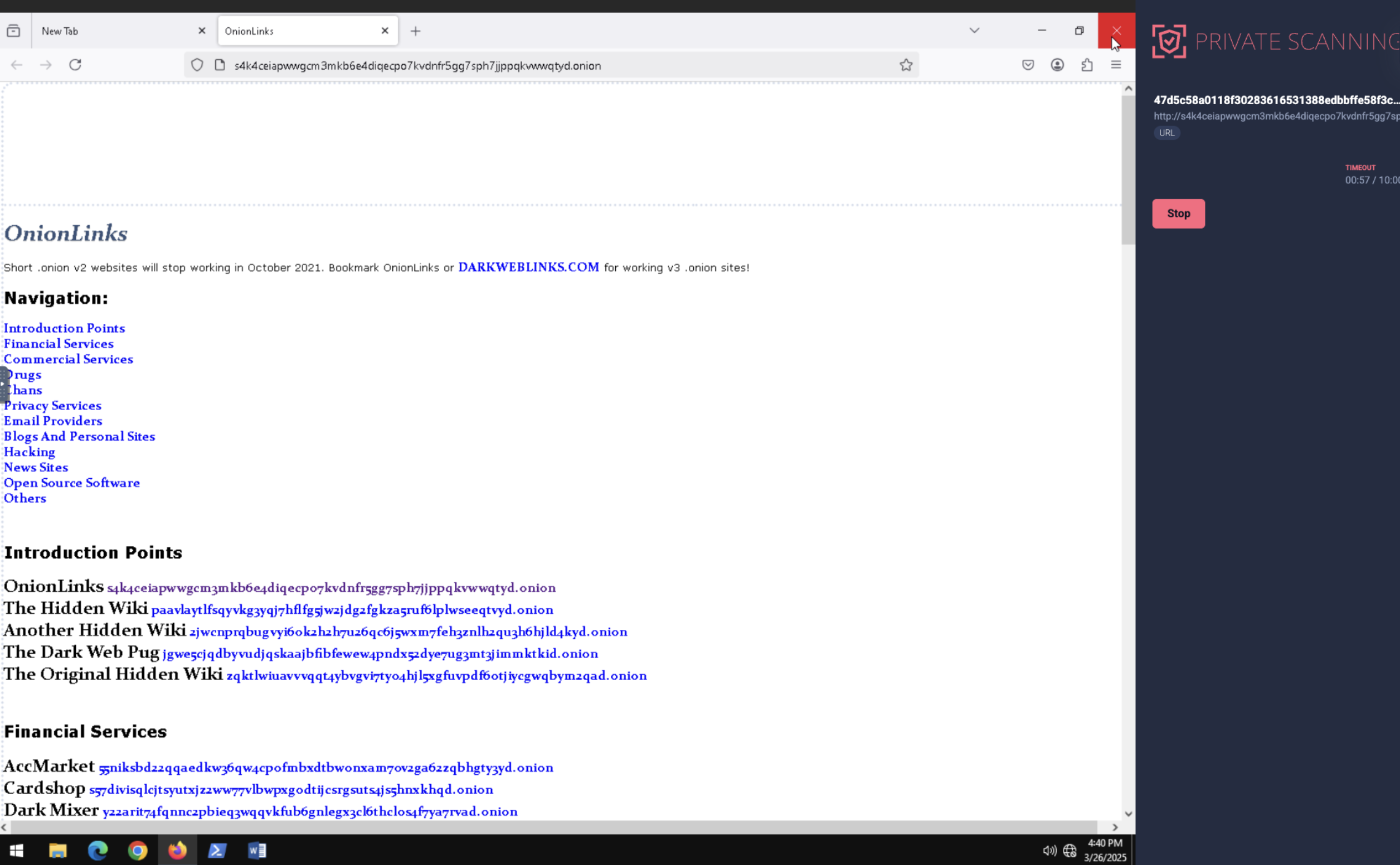
Support for .onion domains in Private URL scanning. Private URL scanning enables users to submit websites for analysis, identifying redirection chains, web trackers, downloaded files, and other dynamic properties. We have now extended this functionality to specifically include support for .onion domains within the live interaction URL scanning feature. This enhancement allows users to leverage the interactive sandbox environment to analyze websites hosted on the Tor network, providing visibility into potentially malicious content or infrastructure that is otherwise difficult to access and analyze. This support is exclusive to the interactive scanning mode, enhancing the depth of analysis for these often obfuscated resources.
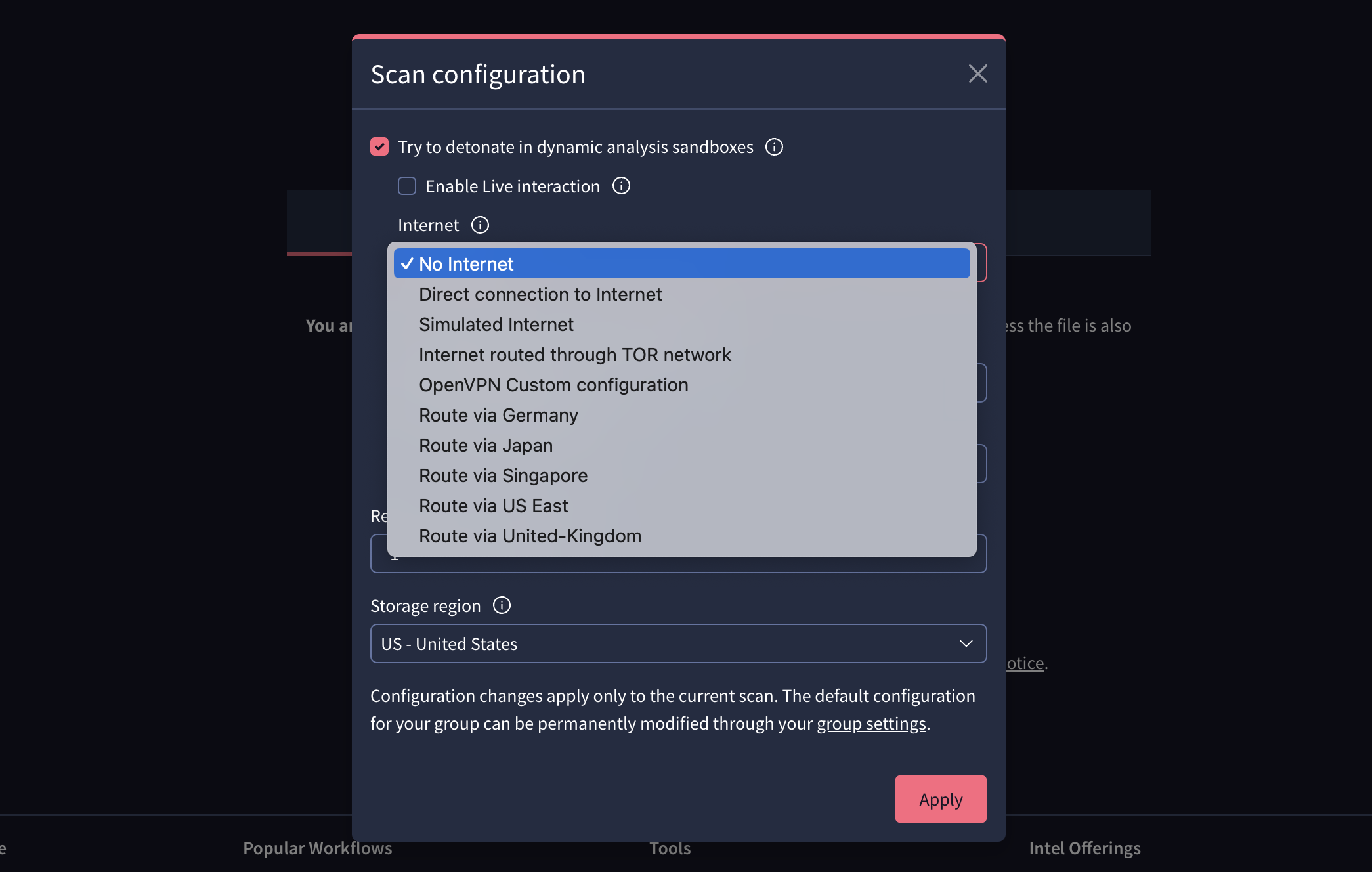
Enhanced network environment control in Private Scanning. As previously described, Private Scanning empowers users to conduct in-depth analysis of files and URLs within isolated static + dynamic sandbox environments. Building upon this dynamic analysis capability, we are introducing advanced Internet connection options during file sandbox detonation. This new functionality provides granular control over the network connectivity of the sandbox, allowing analysts to simulate various network conditions and observe how threats react. The available options include:
- No Internet: completely isolates the sandbox from the internet.
- Direct connection to Internet: provides a standard internet connection for the sandbox.
- Interception of HTTPS/TLS connections: enables the capture and analysis of encrypted network traffic, e.g. to identify HTTPS URLs used for CnC purposes or to download additional malicious payloads.
- Internet routed through Tor network: allows analysis of malware behavior when communicating through the Tor anonymity network.
- OpenVPN custom configuration: supports the use of custom OpenVPN configurations to simulate specific network environments. Documentation on self hosted and 3rd party VPN connectivity.
- Traffic routing through {Germany, Japan, Singapore, US East, United Kingdom}: enables the routing of sandbox network traffic through geographically diverse exit nodes to circumvent cloaking/evasion techniques or to understand region-specific malware customizations.
This enhancement is accessible within the Private Scanning interactive malware analysis capabilities.
Netblocks support in YARA Livehunt. YARA is de-facto pattern matching tool for threat intel analysts and malware researchers. As previously described, Google Threat Intelligence extends YARA beyond file content matching to be able to match incoming URLs, domains and IPs. We are adding support for matching against netblocks within our "vt" YARA module. This new feature allows users to create YARA rules that can identify network traffic or indicators associated with specific IP address ranges or CIDR blocks. This enhancement can be valuable for threat hunting and identifying activity originating from or communicating with known malicious infrastructure or threat actor-associated netblocks. See examples:
import "vt"
rule ip_in_some_IPv4_range {
condition:
vt.net.ip.in_range("192.168.1.0/24")
}import "vt"
rule ip_in_some_IPv6_range {
condition:
vt.net.ip.in_range("2001:db8::1/32")
}