Threat Intelligence Report Types
Google Threat Intelligence provides continuously updated reports and analysis on threat actors, campaigns, vulnerabilities, malware, tools, and more. You can access these reports by navigating to the Reports & Analysis.
For easy reference, each report is tagged with its type, which is automatically extracted from the content.
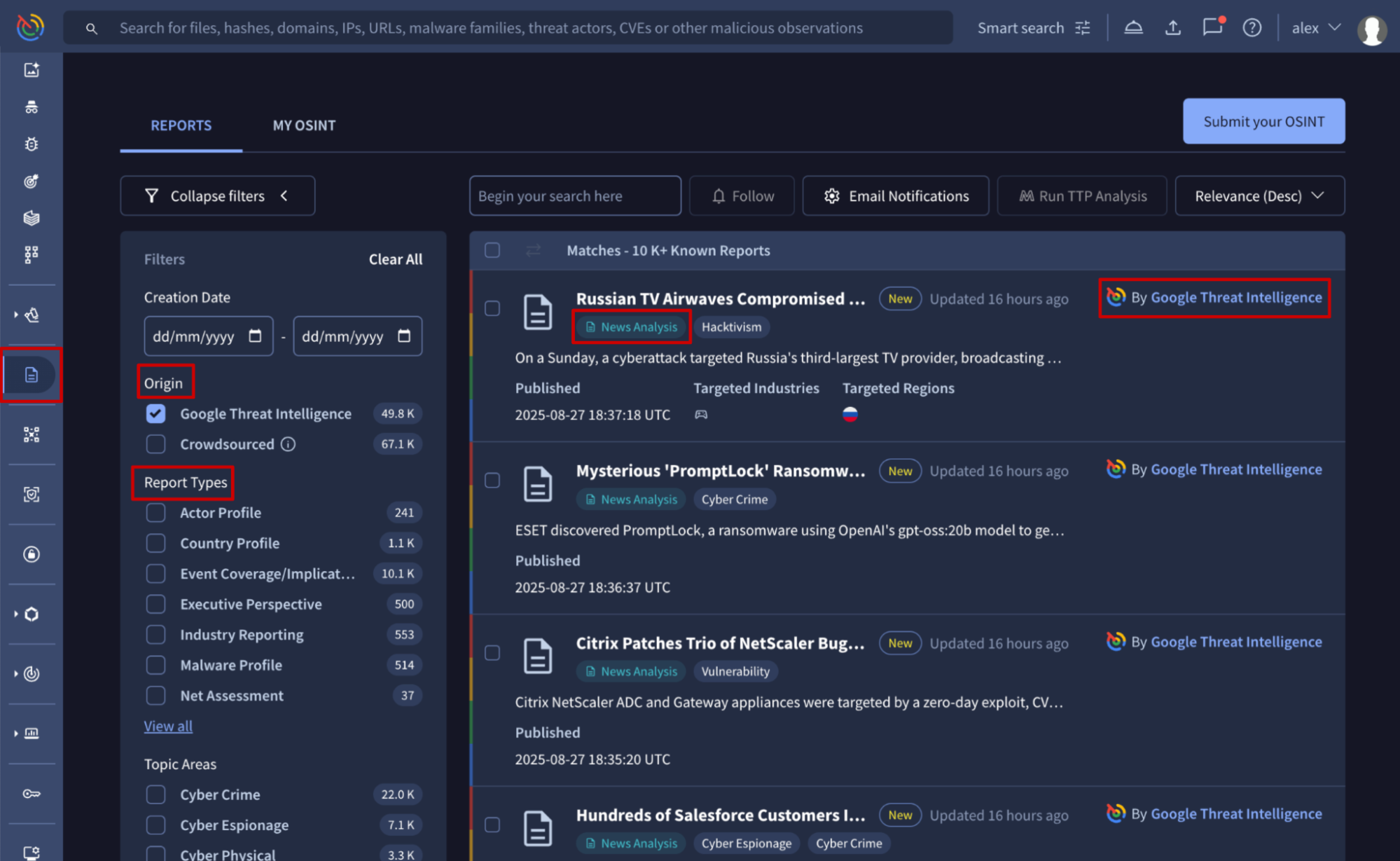
Current Reports types
The following table provides an overview of our current curated Threat Intelligence reports and the unique crowdsourced report type, OSINT Article.
| Report Type | Description | Benefits |
|---|---|---|
| Actor Profile | These curated reports provide an in-depth look into a specific threat actor's tactics, techniques, and procedures. | Proactive defense, improved detection rates, faster incident response, optimized security investments. |
| Event Coverage/Implication | These curated reports generally contain analysis on the implications of a recent event or campaign conducted by a threat actor. This report type also includes first glance reports, which offer preliminary information on an incident while the analysis of related malware or other campaign aspects is still in progress. | Reduced exposure to breaking threats, improved crisis management, agile defense adjustments, minimized impact. |
| Executive Perspective | These curated reports provide brief analysis about cyber threats relevant to events or business circumstances, geared toward a strategic leadership audience. This report type also includes Intelligence at a Glance reports, which provide a weekly snapshot into newly produced reports, blogs, webinars, as well as some insight into customer interests based on top search terms and most read reports. | Alignment of security with business goals, improved cyber resilience. |
| Malware Profile | These curated reports contain technical analysis of a representative sample of a code family. This report type typically includes file characteristics, host- and network-based indicators, configuration information, and details of code execution. | Enhanced malware detection, proactive IoC sweeping, technical malware capabilities understanding. |
| Net Assessment | These curated reports provide an overview of the top threats that Google Threat Intelligence reported on or observed throughout the past quarter. | Holistic threat understanding, informed long-term planning. |
| News Analysis | These curated reports provide brief, daily intelligence insights into cyber security topics discussed in the news. | Informed perspective, improved communication. |
| Threat Activity Alert | These curated reports relay immediate observations of notable activities within the cyber threat environment. Activities continue to be monitored and may result in additional alerts or reports if anything significant occurs, or the issue warrants further analysis. | Rapid risk mitigation, minimized damage. |
| Threat Activity Report | These curated reports relay historical and recent activities observed within the cyber threat environment whose relevance has become elevated by current circumstances. Activities continue to be monitored and may result in additional alerts or reports if anything significant occurs, or the issue warrants further analysis. | Proactive response to evolving threats, enhanced detection capabilities, deeper understanding of threat actor lifecycles. |
| Trends and Forecasting | These curated reports provide analysis into threat actor tactics, trends, or types of threat activity, which may include review over a specified time frame and/or predictions based on identified trends. | Understand evolution of threats, future-proofing security. |
| TTP Deep Dive | These curated reports provide an in-depth look into a threat actor and the tactics, techniques, and procedures (TTPs) they use to achieve specific goals. | Deeper understanding of attacker methodology, improved detection of sophisticated attacks, targeted mitigation. |
| Weekly Vulnerability Exploitation Report | These curated reports summarize important developments concerning vulnerabilities that may pose a critical or high risk to enterprises that have been observed by Google Threat Intelligence on a weekly basis. This report is intended as a resource for decision makers on out-of-cycle patching decisions. | Significant reduction in attack surface, actionable and timely intelligence. |
| OSINT Article | These crowdsourced reports are automatically ingested from the community, but users can also request the ingestion of not yet included articles. They cover a wide range of cybersecurity topics. | Rapid and broader threat coverage. |
Decommissioned curated Reports types or series
Decommissioned series or types of curated Threat Intelligence Reports are no longer being generated. Despite some exceptions indicated in the following table, the new information that would have been used to generate new Reports of those types or series, is now integrated into other reports or objects.
To avoid confusion, decommissioned report types are no longer in the initial filter menu since we don't produce them anymore. However, all historical reports are still available on the platform and can be found using advanced or free text searches.
The table below outlines the decommissioned Threat Intelligence Reports types or series, detailing alternative search methods for historical Reports and where new information is being integrated.
Note that the information from our objects is used to populate the Gemini summary when performing a semantic search on the topic, specifically on the top search bar. This provides another way to find the same data listed below.
| Legacy Report | Description | New Information Location | Alternative Search for Historical Legacy Reports |
|---|---|---|---|
| Actor Overview | These reports provide a brief overview of a threat actor. | This type of information is now included in the curated Threat Actors cards, which are accessible from the Threat Landscape menu option of the platform. | Alternatively, find legacy Reports by using the following advanced search in the Reports search bar of the platform: report_type:"Actor Overview" |
| FireEye Labs Research | These reports provide an in-depth look into a threat actor, malware, or tactics used by threat actors to achieve specific goals. | This type of information is now included in the TTP Deep Dive report type. | Alternatively, find legacy Reports by using the following advanced search in the Reports search bar of the platform: report_type:"FireEye Labs Research" |
| Futures Scenario | These reports provide analysis into threat actor tactics, trends, or types of threat activity, which may include review over a specified time frame and/or predictions based on identified trends. | This type of information is now included in the Trends and Forecasting report type. | Alternatively, find legacy Reports by using the following advanced search in the Reports search bar of the platform: report_type:"Futures Scenario" |
| Horizons | These reports provide analysis into threat actor tactics, trends, or types of threat activity, which may include review over a specified time frame and/or predictions based on identified trends. | This type of information is now included in the Trends and Forecasting report type. | Alternatively, find legacy Reports by using the following advanced search in the Reports search bar of the platform: report_type:"Horizons" |
| Indicator Report | This report series contains malicious indicators associated with the respective malware family. | Indicators are now directly associated with Malware & Tools, through the IOCS tab. They are accessible from the Threat Landscape menu option of the platform. Additionally, indicators are searchable over the platform through advanced search modifiers. | Alternatively, find legacy Reports by using the following advanced search in the Reports search bar of the platform: report_type:"Event Coverage/Implication" name:"Indicator Report" |
| Industry Intelligence Quarterly | These reports provide a high-level summary of threats to an industry vertical, across adversary motivations, on a quarterly basis. | This type of information is now included in the Industry Snapshot reports of the Industry Reporting report type. | Alternatively, find old legacy Reports by using the following advanced search in the Reports search bar of the platform: report_type:"Industry Intelligence Quarterly" |
| Malware Overview | These reports provide a brief overview of a malware family. | This type of information is now included in the Malware & Tools cards, accessible from the Threat Landscape menu option of the platform. | Alternatively, find legacy Reports by using the following advanced search in the Reports search bar of the platform: report_type:"Malware Overview" |
| Network Activity Reports | These reports analyze network flow data against industrial TCP/UDP ports using third-party intelligence, leveraging Google's Indicator Confidence Score to identify and prioritize potential threats to industrial environments. | This type of information is not included in new objects. Get similar data by: (1) checking IP addresses conducting port scanning from the SANS Internet Storm Center, (2) checking IP addresses threat context and assessment in Google Threat Intelligence. | Alternatively, find legacy Reports by using the following advanced search in the Reports search bar of the platform: report_type:"Network Activity Reports" |
| Operational Net Assessment | This report series provides an overview of the top threats that Google Threat Intelligence reported on or observed throughout the past quarter. | This type of information is now included in the Net Assessment report type. | Alternatively, find legacy Reports by using the following advanced search in the Reports search bar of the platform: report_type:"Event Coverage/Implication" name:"Operational Net Assessment" |
| Potential Targeted Malware Infection Lures | This report series highlights potential malware lures that threat actors may exploit or use in social engineering attempts based on previously observed operational patterns, specific subjects, events, and topics. | This type of information is now included in the Trends and Forecasting report type. | Find legacy Reports by using the following advanced search in the Reports search bar of the platform: report_type:"Event Coverage/Implication" name:"Potential Targeted Malware Infection Lures". Alternatively, this information can be retrieved via semantic searches using the term "lures". |
| Patch Report | This report summarizes the vulnerabilities addressed in a specific patch to help customers better consider and prioritize their patching efforts holistically across an entire patch instead of as individual vulnerabilities. | This type of information is now included in the Vulnerability Intelligence cards, accessible from the platform menu options. To find vulnerability summaries for a specific vendor, use the following advanced search in the search bar: vulnerable_vendor:"Microsoft"; or a more generic search "Oracle". Additionally set the Creation Date filter to the day or month of the advisories publication. | Alternatively, find legacy Reports by using the following advanced search in the Reports search bar of the platform: report_type:"Patch Report" |
| Vulnerability Report | This report captures information that Google Threat Intelligence knows about a given vulnerability and the risk and threat it poses to customer organizations. The information provided includes, Risk Rating, Exploitation State, known exploits, a list of vulnerable products and technologies, and many other technical details. | This type of information is now included in the Vulnerability Intelligence cards, accessible from the platform menu options. To find vulnerability summaries for a specific vendor, use the following advanced search in the search bar: vulnerable_vendor:"Microsoft"; or a more generic search "Oracle". Additionally, vulnerability objects can be filtered by Risk Rating, Exploitation State, Has Exploits and more. | There's no workaround to get legacy reports, all of them were merged into Vulnerability cards. |
| Cyber Physical Security Roundup | This report series refers to the protection of systems that bridge the digital world and the physical world. | This type of information is now included in the News Analysis report type. | Alternatively, find legacy Reports by using the following advanced search in the Reports search bar of the platform: report_type:"ICS Security Roundup" name:"Cyber Physical Security Roundup" |
| Distribution Threat Cluster Update | This weekly report series identifies the most significant current threats and detailed the specific methods they were using to spread and infect systems. | This type of information is now included in the Campaigns cards accessible from the Threat Landscape menu option of the platform. | Alternatively, find legacy Reports by using the following advanced search in the Reports search bar of the platform: report_type:"Event Coverage/Implication" name:"Distribution Threat Cluster Update" |
| Operational Technology Phishing Roundup | This report series reviews malicious phishing email attachments, which are uploaded to public file-scanning services. Our experts select the samples in this report by matching content and header strings to a series of OT-related keywords. | This type of information is not included in new objects, and there's no workaround to get similar data. | Find legacy Reports by using the following advanced search in the Reports search bar of the platform: name:"Operational Technology Phishing Roundup" (report_type:"Trends and Forecasting" OR report_type:"Event Coverage/Implication") |
| Actor update | This report series highlights new insights we have released during the past week on actors we track. | This type of information is now included in the curated Threat Actors cards, which are accessible from the Threat Landscape menu option of the platform. | Alternatively, find legacy Reports by using the following advanced search in the Reports search bar of the platform: report_type:"Event Coverage/Implication" name:"Actor update" |
| Malware update | This report series highlights new insights we have released during the past week on malware families we track. | This type of information is now included in the Malware & Tools cards accessible from the Threat Landscape menu option of the platform. | Alternatively, find legacy Reports by using the following advanced search in the Reports search bar of the platform: report_type:"Event Coverage/Implication" name:"Malware update" |
| Alleged Extortion Victims | This report series summarizes data leaks from various ransomware groups observed on dark web blogs, detailing the victims of their extortion and data exfiltration campaigns. | This type of information is now included in the Ransomware Data Leaks dashboard accessible from the Dashboards menu option of the platform. | Alternatively, find legacy Reports by using the following advanced search in the Reports search bar of the platform: report_type:"Threat Activity Report" name:"Alleged Extortion Victims" |
| OT Vulnerability Exploitation Roundup | This report series highlights new exploits and exploitation activity associated with operational technology (OT) and industrial control systems (ICS) vulnerabilities. | This type of information is now consolidated into the existing Weekly Vulnerability Exploitation Report (WVER). | Alternatively, find legacy Reports by using the following advanced search in the Reports search bar of the platform: report_type:"Event Coverage/Implication" name:"OT Vulnerability Exploitation Roundup" |
| Industrial Control Systems and Medical Vulnerability Advisories Reported by CISA | This report series is a summary of vulnerabilities disclosed by CISA in a month affecting ICS and Medical systems. | This type of information is now consolidated into the existing Weekly Vulnerability Exploitation Report (WVER). | Alternatively, find legacy Reports by using the following advanced search in the Reports search bar of the platform: report_type:"Trends and Forecasting" name:"Industrial Control Systems and Medical Vulnerability Advisories Reported by CISA" |
| Cloud Vulnerabilities | This report series highlights important software vulnerabilities we believe could have an impact on patch management and prioritization decisions for cloud services. | This type of information is now consolidated into the existing Weekly Vulnerability Exploitation Report (WVER). | Alternatively, find legacy Reports by using the following advanced search in the Reports search bar of the platform: report_type:"Trends and Forecasting" name:"Cloud Vulnerabilities" |
Updated about 2 months ago
