📢 Google TI Mondays. Quick reminder to Follow the Google TI Mondays series across our social platforms every week for quick, actionable practitioner tips and product adoption advice designed to enhance your efficiency. These actionable tips are essential. #GoogleTIMondays
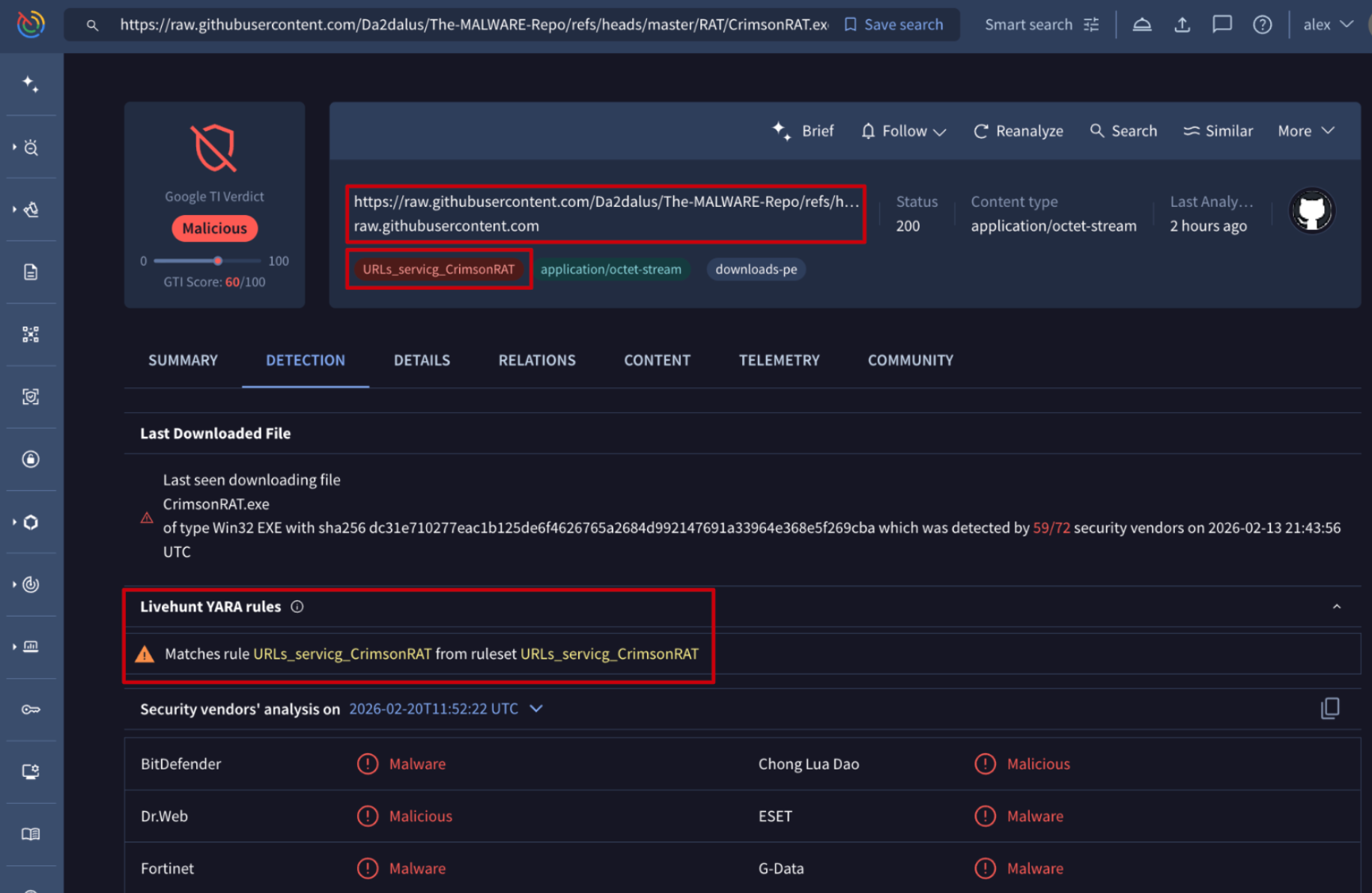
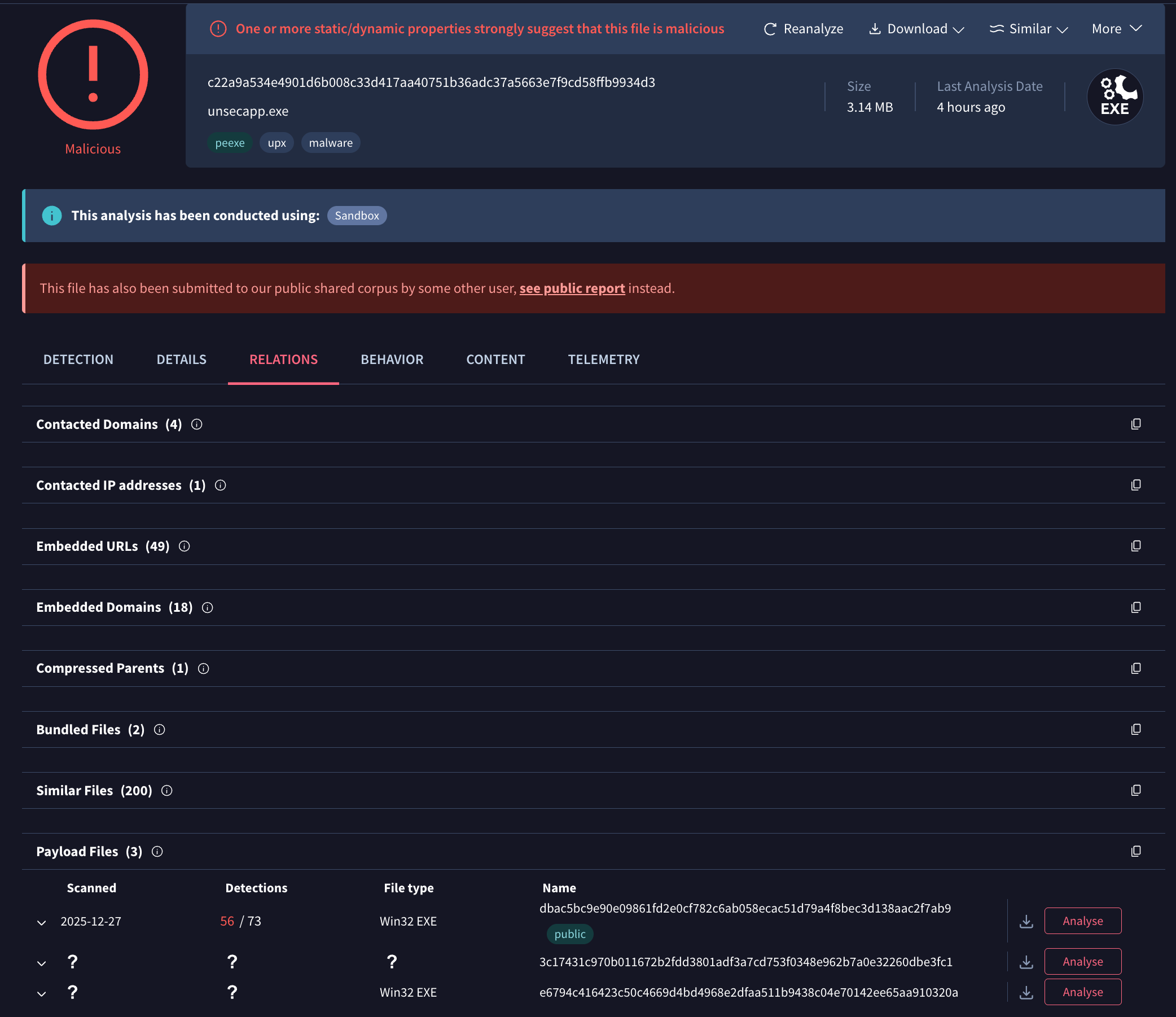
💪 Detection Highlights. The Google Threat Intelligence Group and FLARE team continuously enhance Google TI's detection capabilities through new YARA rules and updated malware configuration extractors. This week, we've released YARA rules covering 15 newly tracked malware families and updated detection content for 53 existing families, including one with an updated configuration extractor. Our prioritization focuses on malware families actively observed in Mandiant incident response engagements, Google SecOps customer environments, and top GTI search trends.
As we track new malware families found through our research, we build and release detection signatures. Some recent examples include:
- POTATOWALL: a backdoor written in Rust that uses Telegram for command and control. POTATOWALL leverages the Rust libraries Tokio for asynchronous runtime and Teloxide for Telegram functionality. POTATOWALL contains a hard-coded Telegram bot token, which it uses to periodically poll for new command messages. POTATOWALL supports commands to change its working directory, execute a command using Windows cmd.exe, and execute a command using PowerShell. See its curated YARA detection rules.
- BINDCOUPE: a lightweight backdoor written in C++ that communicates to hard-coded command-and-control (C2 or C&C) servers using raw TCP sockets. It is capable of collecting basic system information, downloading files, taking screenshots, and executing arbitrary shell commands. See its curated YARA detection rules.
- DARKFLIP: a backdoor written in C++. DARKFLIP parses an external configuration file for its C2. DARKFLIP supports several commands including: update sleep value, re-register victim with C2, run Windows shell command, run PowerShell command, download file to victim, and delete file. DARKFLIP leverages AES-GCM to decrypt its configuration and for C2 communications. See its curated YARA detection rules.
- DRIVECLEAN: a disruptive payload written in C that is executed as a Windows Native Application masquerading as a system updater. DRIVECLEAN is responsible for enumerating all mapped drives (A-Z) and overwriting the content of files in those drives with NULL bytes. See its curated YARA detection rules.
In addition to providing detection rules for new and emerging threats, we continue to update our detection systems for threats we commonly see. This week, we updated SOGU, ICEFOG, and BRICKSTORM.
These updates ensure you have the latest indicators and enhanced detection capabilities, with configuration extraction systems updated where applicable.
See latest malware family profiles added to the knowledge base and the complete list of curated YARA rules in our database.
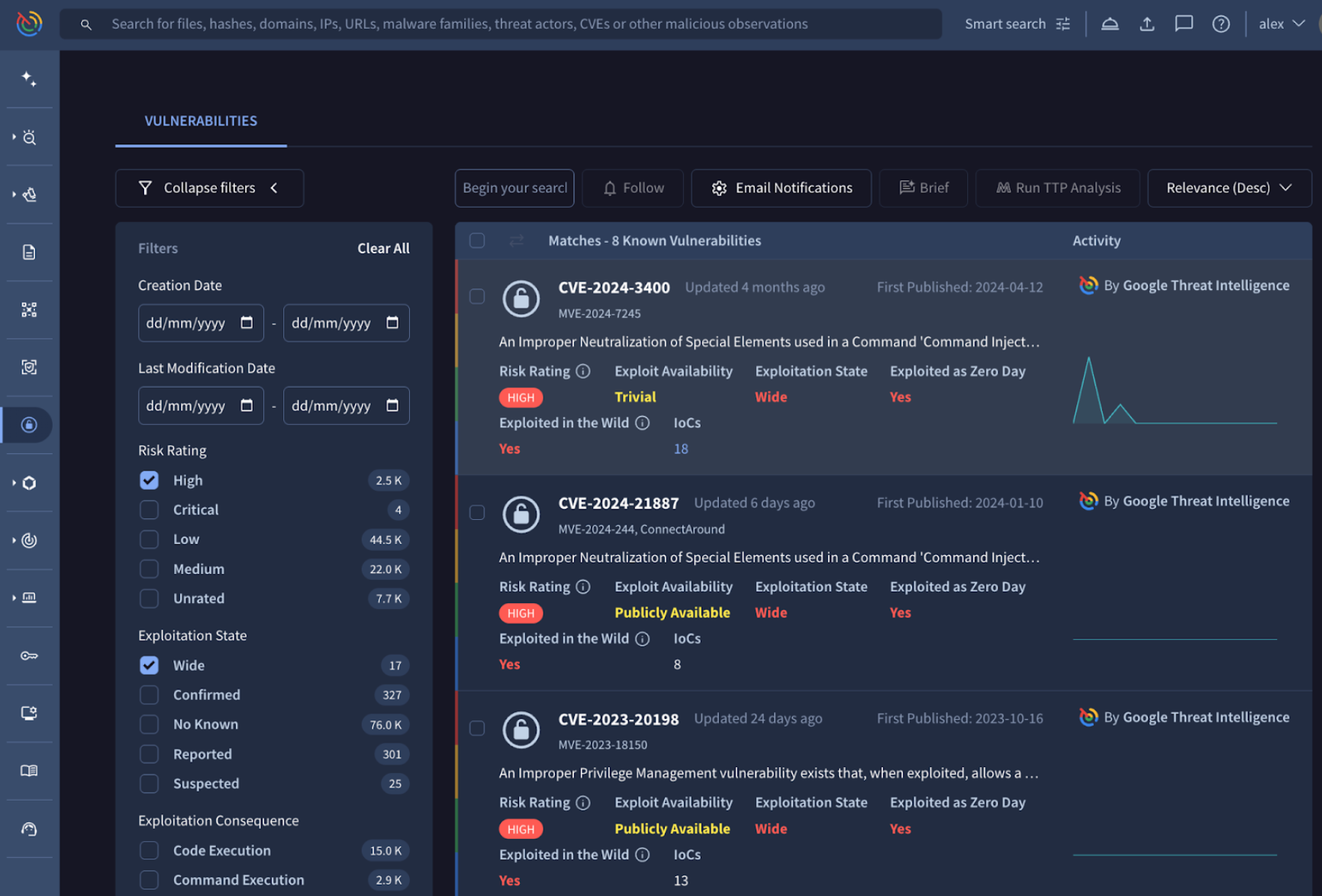
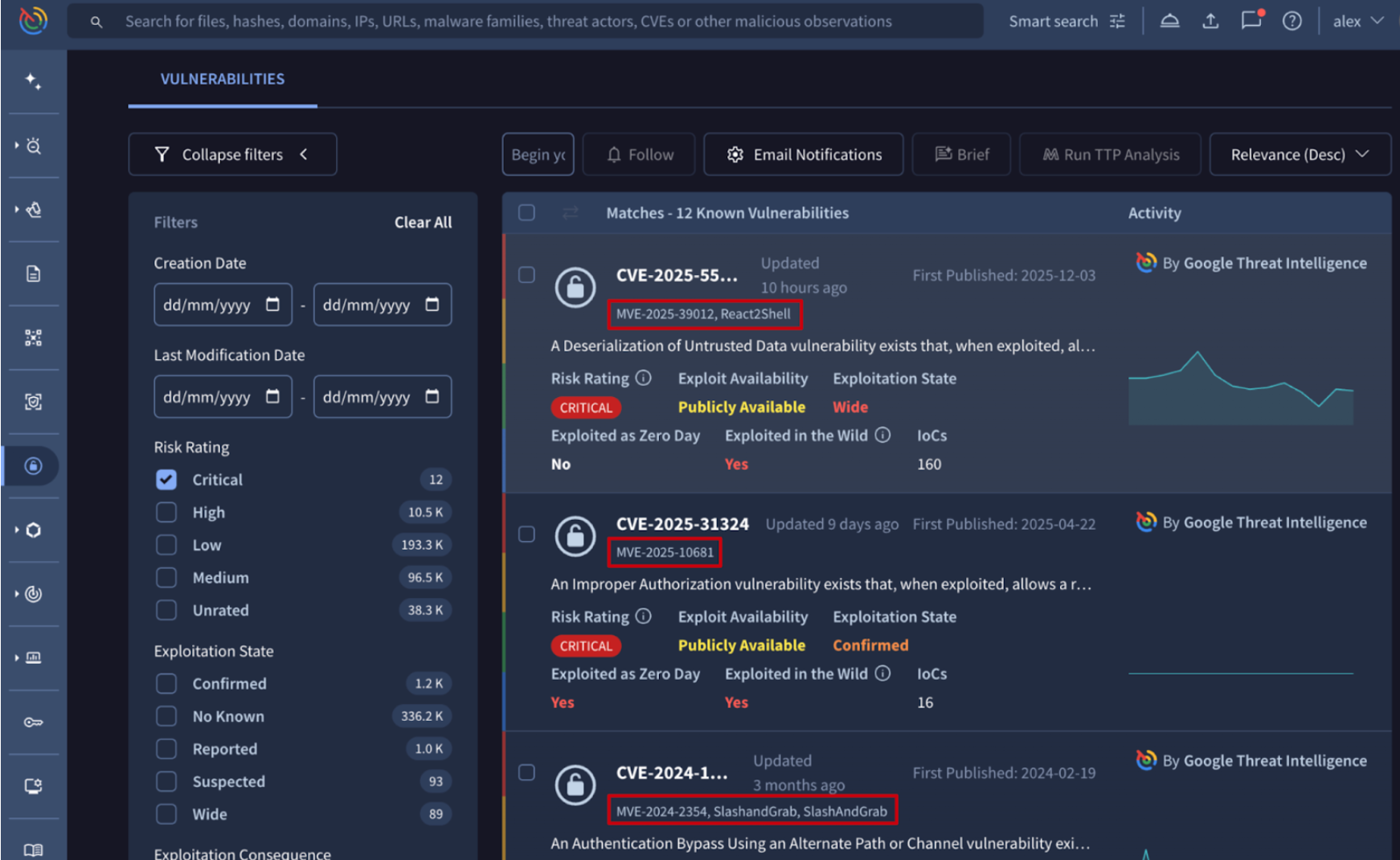
📢 Vulnerability Intelligence for Standard Licenses. The Vulnerability Intelligence module is a specialized component of Google Threat Intelligence designed to move security teams beyond static CVSS scores. It provides a centralized hub to search, filter, and prioritize vulnerabilities (CVEs) enriched with internally calculated risk ratings and real-world visibility into exploitation in the wild. Previously exclusive to Enterprise and Enterprise Plus tiers, the Vulnerability Intelligence module is now available to Standard licensed customers as well. This update empowers a broader range of security teams to implement smarter, threat-driven patching programs.