October 20th, 2025 - Threat Profiles GA, Agentic Public Preview, Crowdsourced AI and new sandbox capabilities
Google TI Mondays. We are publishing concise product knowledge pills on our social channels every Monday. These are practitioner tips and product adoption boosters, check out our latest content and don't forget to follow us:
- Dynamic analysis with Google Threat Intelligence.
- Threat Profile in Google Threat Intelligence.
- Advanced search modifiers cheat sheet.
- YARA in action.
- Scale your file hunts with YARA.
Detection Highlights. The FLARE team and Google Threat Intelligence Group consistently update Google TI's YARA rules and malware configuration extractors. Over Q3, we've released YARA rules covering 345 newly tracked malware families, and expanded our configuration extraction platform to cover 15 new malware families. This update prioritizes malware families actively observed in Mandiant incident response engagements, Google SecOps customer environments, and top Google TI search trends.
As we track new malware families found during Mandiant investigations, we build and release detection signatures. Some recent examples include:
- HAMMERDROP: This malware is used to drop Windows drivers to bypass endpoint security solutions and has been found in ransomware investigations.
- SELFDRIVE: This Node.js malware has been observed being distributed with trojanized software installers and downloads and executes additional Javascript files.
- TOOLSHELL: This webshell has been observed being installed onto on-premise servers that were exploited by an attacker.
In addition to providing detection rules for new and emerging threats, we continue to update our detection systems for threats like QUASARRAT, WARZONE, and SHADOWLADDER. These updates ensure you have the latest indicators that were extracted by our configuration extraction systems.
Google TI Score enhancements. We have significantly enhanced the Google Threat Intelligence (GTI) Score to improve your threat prioritization and triage efficiency. The updated score now incorporates new contextual factors like threat actor motivation and malware family roles for all IoC types (files, URLs, domains and IP addresses). Furthermore, network IoCs benefit from more granular threat categories based on crowdsourced insights, and URL severity is boosted by detailed data from Google Webrisk. This refinement, including more granular severity levels for suspicious indicators, ensures you can prioritize potential threats more efficiently.
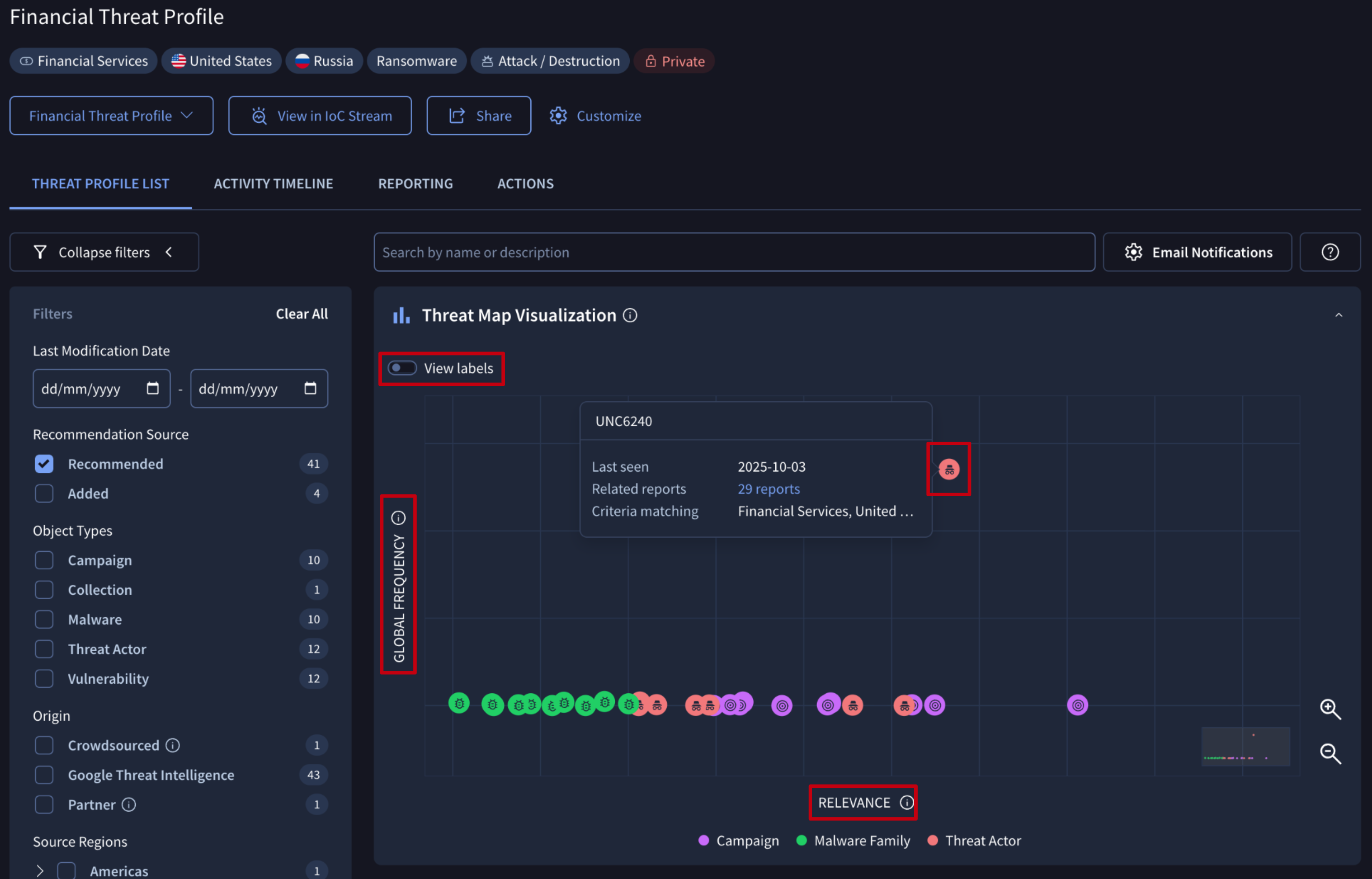
Threat Profiles now generally available (GA). All Threat Profiles in legacy experience migrated to the new look and feel. Includes automatic and holistic visibility of relevant threats, flexible curation to tune and incorporate your own threat intelligence artifacts, enhanced collaboration and sharing, and tactical actionability via out of the box detections and tailored + recent IOC feeds. Now they also provide quick access to an overview explanation of each threat and a scatter plot designed to help you prioritize threats by instantly showing a threat's global prevalence versus its specific relevance within the confines of the dimensions of a given threat profile. Learn more in this webinar.
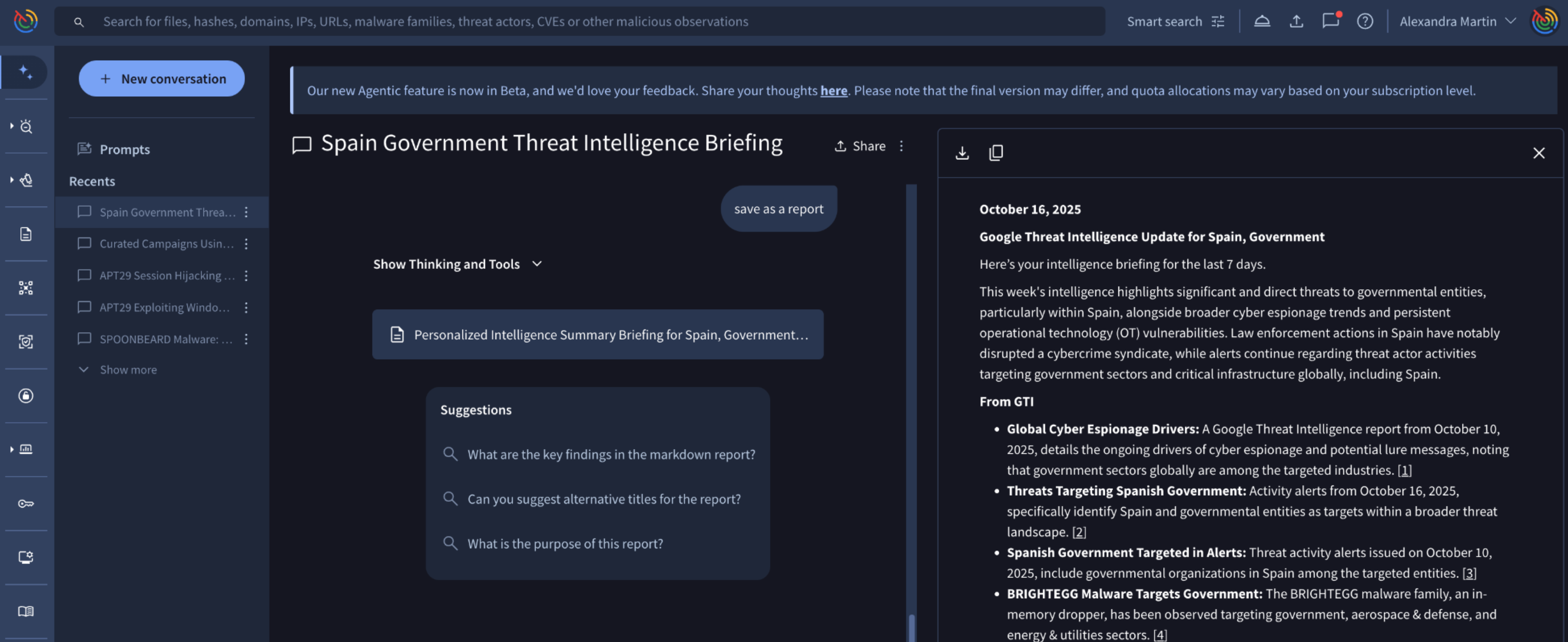
Google TI Agentic public preview. Built on Large Language Models (LLMs) and grounded in Google Threat Intelligence's comprehensive security dataset, the Agentic Platform simplifies and democratizes threat intelligence. This conversational interface lets you interact directly with specialized AI agents to quickly analyze threats, accelerate security investigations, and receive immediate, precise answers. It was released as a public preview to Enterprise and Enterprise+ customers.
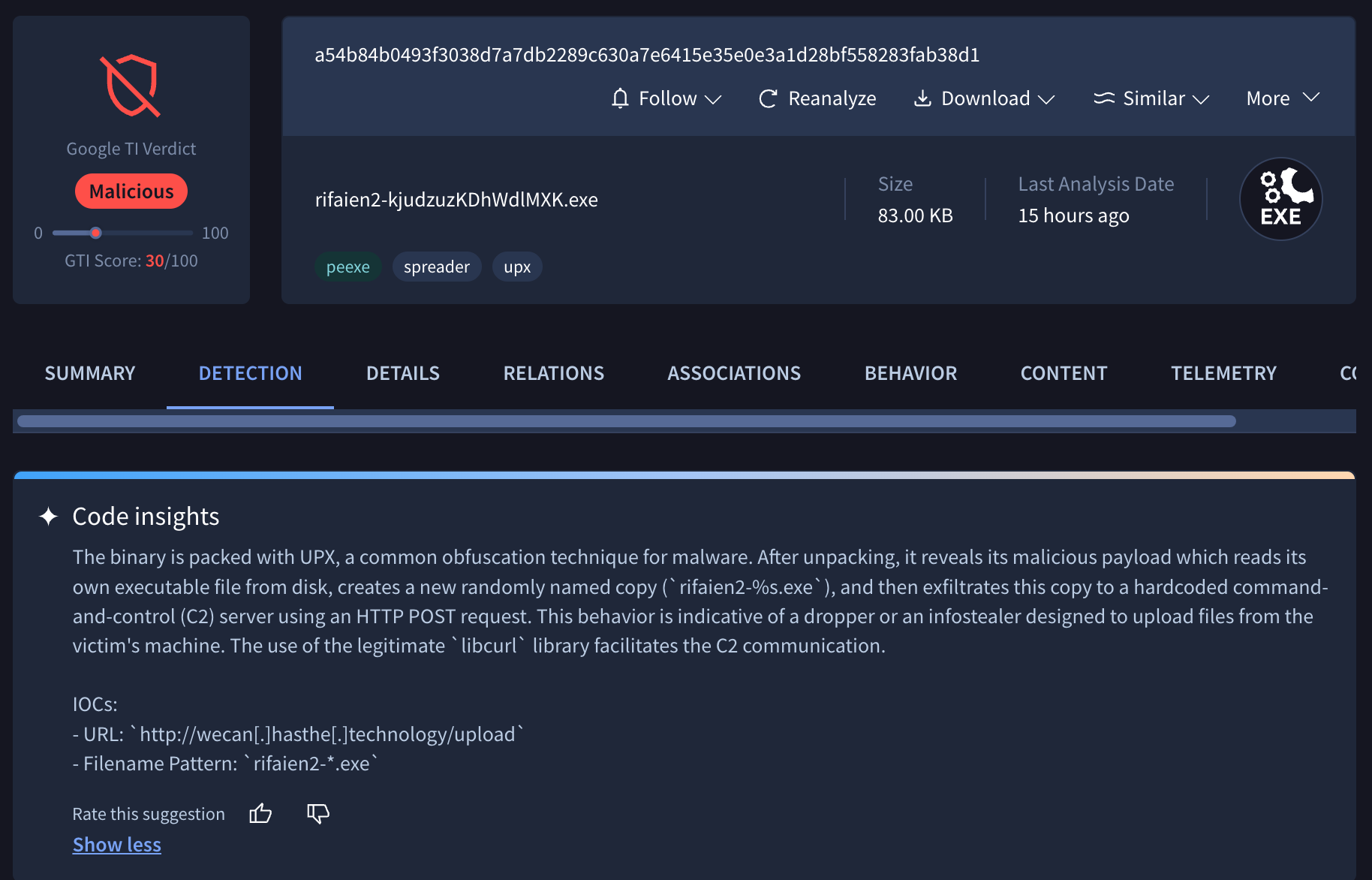
Code Insight now supports SWF and SVG file types. Code Insight is an advanced, Gemini AI-driven capability that serves as an automated assistant for malware analysts and reverse engineers. It uses artificial intelligence to generate natural language summaries that clearly describe a file's intent and overall functionality. We've extended it to support more file formats such as SWF and SVG.
Code Insight experimentation with executables. We continue experimentation with Windows Executables, Linux Executables and OS X Executables and are now ramping up the volume of files processed. Examples:
- Windows Executable
- OS X Executable
- Linux Executable
- Search for terms within Code Insight: type:peexe codeinsight:infostealer p:5+
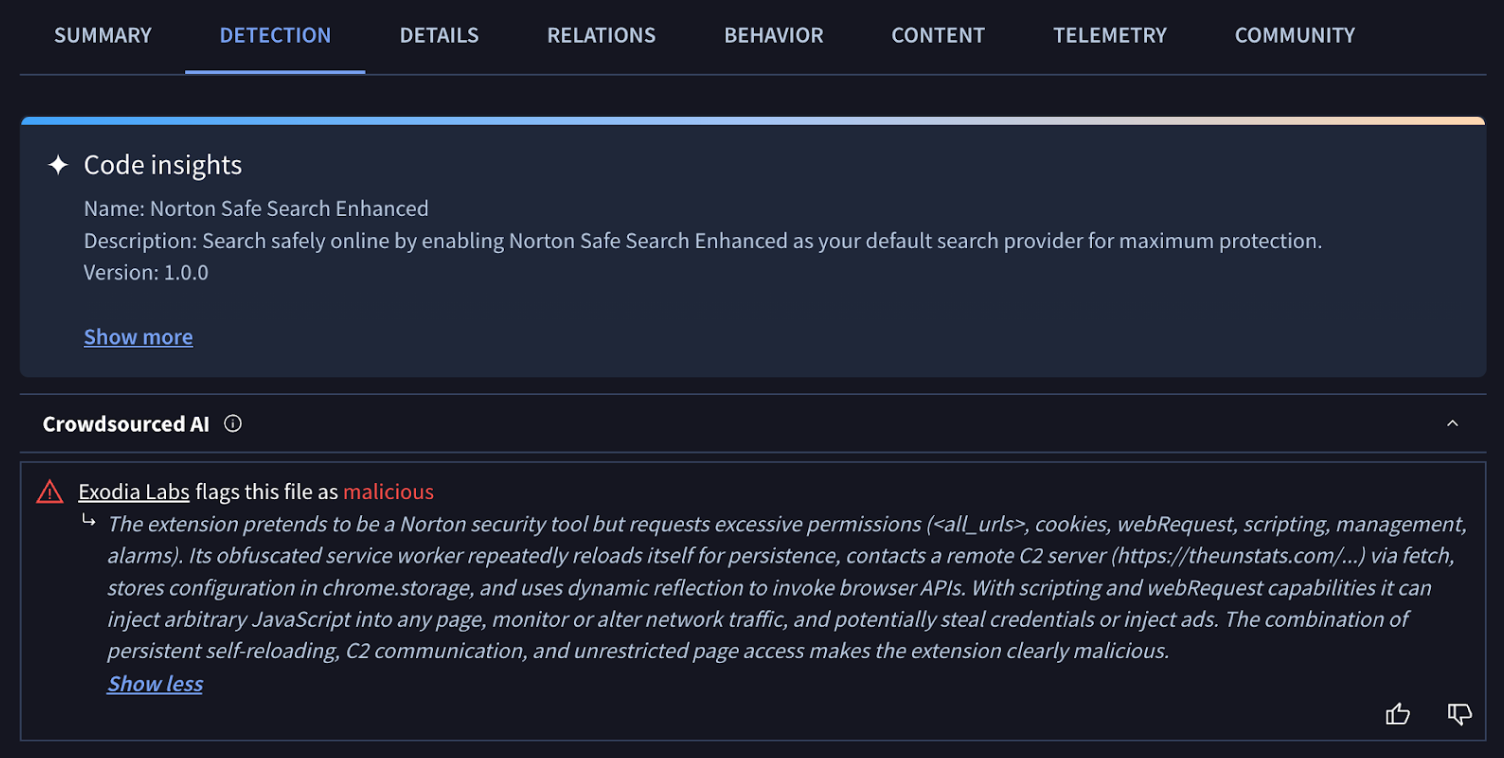
New Crowdsourced AI Contributor: Exodia Labs. The new Exodia Labs integration adds an independent AI analysis stream for Chrome extension (.CRX) files, complementing Code Insight by providing a clear security verdict and detailed reports that outline suspicious actions (like credential theft), with all results fully searchable via new platform operators. Results from Exodia Labs are fully searchable by using the exodialabs_ai_verdict:malicious | suspicious | benign or exodialabs_ai_analysis:<keywords> search modifiers, allowing users to pivot across and find large campaigns of malicious Chrome extensions. See example report. See example search.
Private collection sharing across organizations. Private collections allows users to create a "container" for artifacts like indicators that then inherit automated associations, analytics, telemetry and additional actions. We have extended the functionality so that customers may now share threat information like indicators across trusted circles – i.e. users that are not part of their current organization. Note, you will need to identify and add either the Google TI organization name or username directly in order to share with others outside of your organization.
Multi-CVE search. Google TI's CVE cards offer crucial information on individual vulnerabilities such as severity, risk rating, exploitation state, and exploit availability. This data helps organizations prioritize patching and mitigation efforts by providing empirical risk scoring. The new multi-search functionality significantly improves workflow efficiency by allowing users to quickly gather and compare intelligence on several CVEs in parallel, streamlining the process of tracking widespread threats by allowing users to add multiple vulnerabilities to a threat profile for consolidated tracking. Similarly, multi-CVE search allows security analysts to prioritize a list of vulnerabilities that may have been identified by 3P tools based on in-the-wild exploitation and thus impact likelihood. See example.
New curated GTI-G/Mandiant authored hunting YARA rules. YARA Rules are a powerful, pattern-matching tool used by security professionals to identify and classify malware and suspicious files. We are now including a new set of Hunting YARA Rules within our published Google Threat Intelligence threat Reports, that are easily recognized by their naming convention, which always starts with "G_Hunting_". These rules are designed to help your team uncover activity potentially related to a specific attack technique or malware, providing initial detections that require further verification to confirm malicious intent. Think of them as an extra tool for deeper searching, helping you find more subtle signs of a threat in your environment and stay ahead of emerging risks. See example.
Enhanced dynamic analysis / sandbox capabilities. Files uploaded to Google Threat Intelligence are executed across multiple sandboxes to generate detailed behavioral insights in the analysis report's Behavior tab of the UI. On this front we have many announcements:
- New file type supported. Added support for ELF shared objects with an entrypoint detonation.
- Enhanced detonations. Improved analysis and reporting for the following filetypes:
- VBA (Visual Basic for Applications)
- SVG (Scalable Vector Graphics)
- MSC (Microsoft Management Console Snap-ins)
- MSHTA, HTA (Microsoft HTML Applications)
- New OS versions deployed in the Zenbox sandbox. Windows 11 and Android 13.
- We've expanded our file detonation capabilities by adding the Google Safe Browsing sandbox to our dynamic analysis systems. See example.
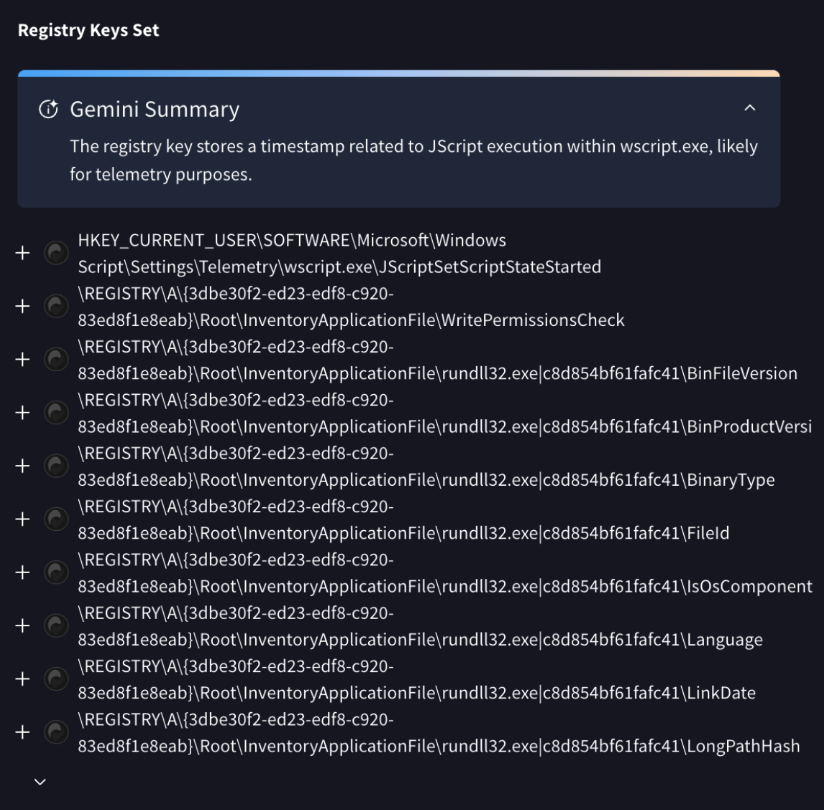
- AI registry key summary. We've incorporated an AI-powered explanation to help users quickly understand the impact, intent and significance of the reported registry-related actions. See example.
New integrations and implementation/dev kits. Integrations are absolutely crucial for operationalizing Google Threat Intelligence and transforming raw insights into immediate defensive action. We are fully committed to breaking down these silos and significantly improving our integration ecosystem to drive efficiency and speed up your Mean Time to Resolution (MTTR).
- New integrations released:
- Integration updates:
- Adoption, implementation and customer enablement:
- Detailed MISP install and usage guide to ensure faster and smoother deployments improving time-to-value.
- Google TI Integration Dev Kit Released. Provides example scripts and guidance for custom workflows. This is designed to accelerate your technical discussions and streamline the process of solution design.
