November 3rd, 2025 - Agentic + docs, CAPE payload extraction, Code Insight code analysis endpoint, process your own OSINT and more
📢 Google TI Mondays. Tune in every Monday as we share quick, actionable practitioner tips and product adoption advice across our social platforms. These knowledge "pills" are designed to boost your efficiency, follow us to make sure you never miss the latest insights!
💪 Detection Highlights. The Google Threat Intelligence Group and FLARE team consistently update Google TI's YARA rules and malware configuration extractors. Over this period, we've released YARA rules covering 8 newly tracked malware families, and provided updates to YARA rules for 20 existing families and configuration extractors for 2 existing families. This update prioritizes malware families actively observed in Mandiant incident response engagements, SecOps customer environments, and top GTI search trends.
As we track new malware families found through our research, we build and release detection signatures. Some recent examples include:
- BADTILE: a .NET based file utility that connects to a remote server via HTTP-Dmtp. It can accept tasking to transfer a file, send a Dmtp handshake to ping a specified client, and perform a system survey. BADTILE also has the ability to use TCP-Dmtp. See its curated YARA detection rule.
- SYSTEMBC.PERL: a tunneler written in Perl that retrieves proxy-related commands from a command-and-control (C2 or C&C) server using a custom binary protocol over TCP. A C2 server directs SYSTEMBC.PERL to act as a proxy between the C2 server and a remote system. See its curated YARA detection rule.
- FARCRY: an XMPP chat backdoor that communicates over the GoogleTalk service. It is capable of encrypted file transfers and remote command execution. See its curated YARA detection rules.
- DAYSHROUD: a backdoor written in C++ built using Neutralinojs. This backdoor functions as a wrapper for JavaScript code, as well as other resources, contained within the other file extracted by Calendaromatic.exe. This backdoor disguises itself as a desktop calendar application called Calendaromatic, but utilizes stenography to covertly download and execute additional JavaScript code in hidden holiday data. See its curated YARA detection rules.
- OILPEN: a backdoor. It creates itself as a service to establish persistence. OILPEN has capabilities to include: reading and writing files, uninstalling itself, and updating its configuration file. See its curated YARA detection rule.
In addition to providing detection rules for new and emerging threats, we continue to update our detection systems for threats like CHUNKPILE, SQUIDGATE, and SQUIDSLEEP. These updates ensure you have the latest indicators for these evolving threats, leveraging both YARA rules and configuration extraction systems.
See latest malware family profiles added to the knowledge base and the complete list of curated YARA rules in our database.
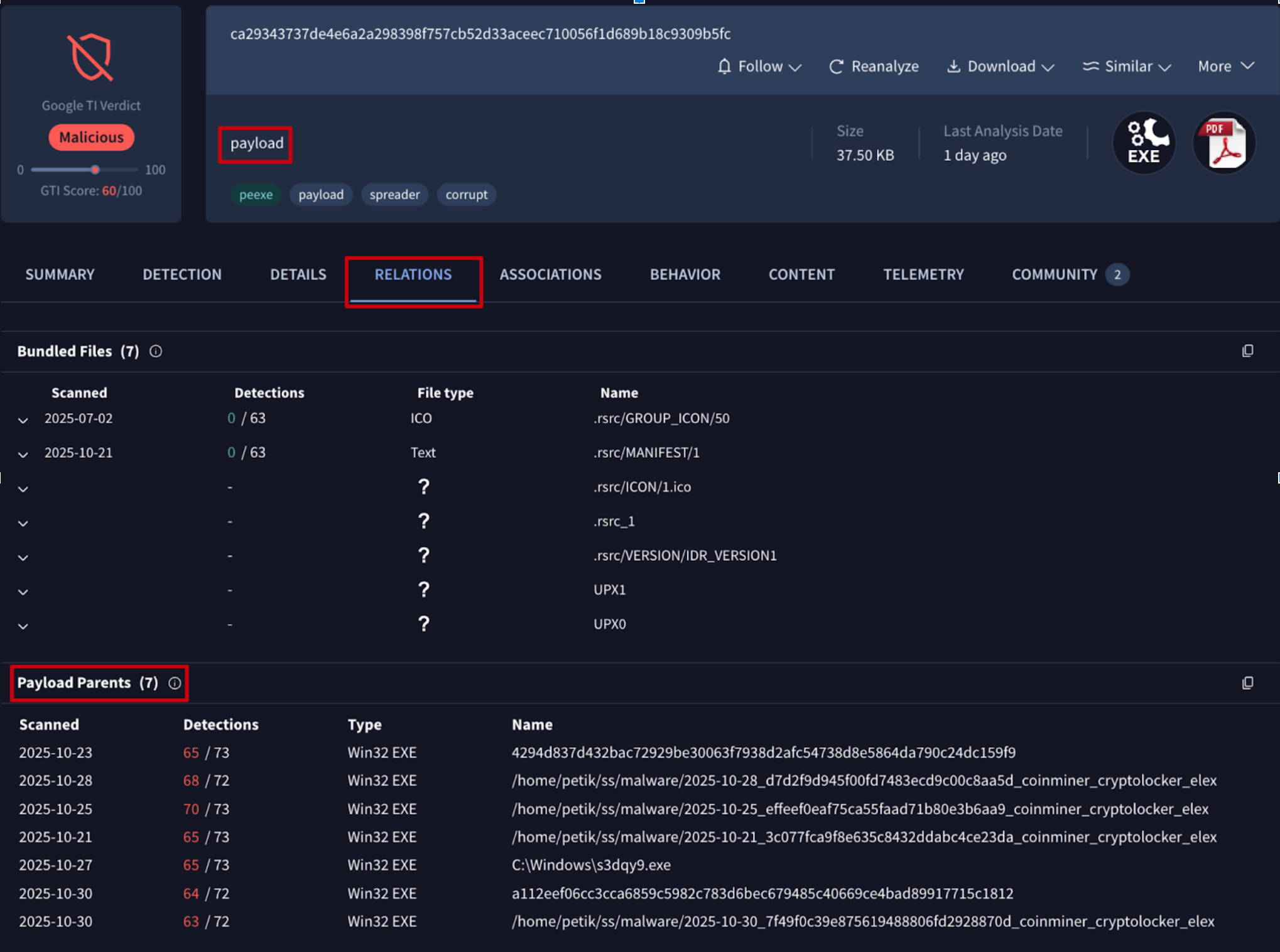
🆕 CAPE sandbox executable payload extraction and feedback loop. Google Threat Intelligence detonates files in multiple home-grown and 3P sandboxes. Our CAPE-derived sandboxes classify samples through automated dynamic malware unpacking and subsequent YARA-based classification of the captured, unpacked payloads. We now automatically extract and submit these unpacked payloads to the platform for separate detonation. This process creates explicit relationships between the parent file and the extracted payloads, and tags the payloads with payload tag for easy identification.
A new tag search modifier, tag:payload, is now available to help you efficiently manage and search for unpacked payloads.
The web interface also displays these relationships:
- When viewing a packed file (parent) analysis report, you will find the unpacked payloads listed under the RELATIONS tab -> Payload Files.
- When viewing an unpacked payload analysis report, you will find its packed parent under the RELATIONS tab -> Payload Parents.
This representation of new relationships is replicated in the API: use the payload_parents relationship to get parent files and payloads_extracted to get unpacked files.
See example.
Stay tuned, soon we will use this process to better characterize and provide more explainability on the parent/packed files.
💪 Agentic now answers documentation related questions. Agentic, our conversational AI platform powered by Google TI, instead of relying solely on static training data, employs Retrieval Augmented Generation (RAG). This technique allows the agent to dynamically retrieve the most relevant and up-to-date threat intelligence from all our sources (VirusTotal, Mandiant finished intelligence, industry/community reports, Safe Browsing, GTI-G threat actor knowledge base, etc). Agentic is constantly evolving. We've added our comprehensive documentation portal as a new data source for RAG. This ensures Agentic can now provide answers that are fully consistent with our latest product features and guidelines.
With this improvement you can now:
- Ask Agentic about the product and available features:
- “What are threat profiles? Why should I use them?”
- Discover API functionality:
- “How can I download feeds using Google Threat Intelligence API?”
- “What threat lists are available for consumption?”
- Ask Agentic to API generate scripts:
- “Can you help me generate a Python script to consume Threat Lists?”
- “Can you demonstrate how to fetch IoCs for a specific threat actor with a Python script?”
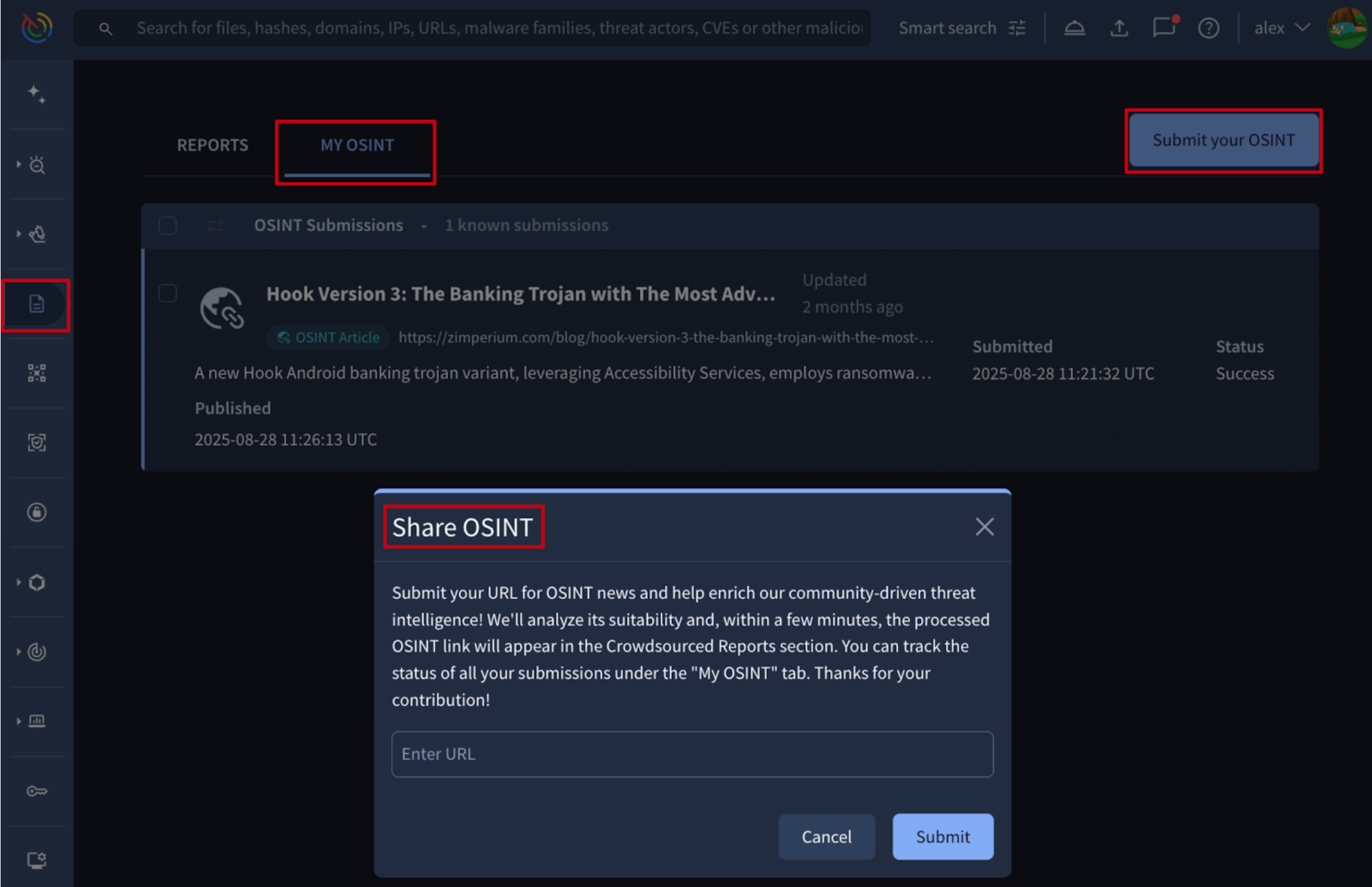
🆕 Submit Your Own OSINT Articles to be processed by Google TI. OSINT (community/industry) articles in Google TI are automatically ingested from a set of trusted sources. They act as a powerful source of Threat Intelligence, transforming vast amounts of public threat data into actionable, contextualized insights that security teams can use for proactive defense and strategic planning. Users can now use the Submit your OSINT button in the Reports & Analysis left navbar menu option to share the URL. Upon submission, the system automatically processes the article to:
- Extract categorization fields (e.g., associated threat actor, malware families, targeted region, and industry) for reports where this information can be confidently identified.
- Generate a summary of the content via Gemini.
- Extract all mentioned IoCs (files, URLs, domains, IPs).
- Generate relationships between the new report object and other Threat Intelligence objects.
Additionally, users can track the history and status of their submissions in the new MY OSINT tab.
🆕 New Code Insight code analysis endpoint for automation. We’ve launched a new Code Insight endpoint that significantly reduces reverse engineering workload by providing analysts with an AI assistant that instantly returns natural language descriptions of code functionality and supports analysis chaining to accelerate time-to-verdict. See example here and our dedicated post. This endpoint is used by our very own VIrusTotal IDA Pro plugin, powering summaries and descriptions of functions.
