January 19th, 2026 - Agentic supports Bulk IoCs, IoC Stream integrated into Agentic, CAPE payload extraction in Private Scanning and more
📢 Google TI Mondays. Quick reminder to Follow the Google TI Mondays series across our social platforms every week for quick, actionable practitioner tips and product adoption advice designed to enhance your efficiency. These actionable tips are essential. #GoogleTIMondays
💪 Detection Highlights. The Google Threat Intelligence Group and FLARE team consistently update Google TI's YARA rules and malware configuration extractors. This week, we've released YARA rules covering 7 newly tracked malware families, and enhanced our detection capabilities for 26 existing families through updated YARA rules and configuration extractors. Our updates prioritize malware families actively observed in Mandiant incident response engagements, SecOps customer environments, and top GTI search trends.
As we track new malware families found through our research, we build and release detection signatures. Some recent examples include:
- POLLREGISTER: is a backdoor written in C++ that provides a persistent communication channel to its controller using WebSocket Secure (WSS) after an initial HTTPS connection to register the host with its controller. The backdoor is capable of executing arbitrary shell commands; loading arbitrary dynamic-link libraries (DLLs); and performing file manipulation, file uploading and downloading, process listing, process termination, and drive enumeration. See its curated YARA detection rule.
- SIDEFOX: is a specialized infostealer that harvests passwords, credit cards, and session tokens. By injecting code into browsers and targeting apps like Discord, Steam, and Telegram, it allows attackers to bypass user protections and hijack accounts almost instantly. See its curated YARA detection rule.
- DARKKEY.LOCKER: is a backdoor written in PowerShell and supports arbitrary PowerShell command execution. DARKKEY.LOCKER obtains its C2 address from the DNS TXT records of another domain and communicates with the C2 using JSON over a Secured WebSocket (WSS). DARKKEY.LOCKER establishes persistence via a registry run key, can perform keylogging, access clipboard data, screen monitor, and perform self deletion. See its curated YARA detection rules.
In addition to providing detection rules for new and emerging threats, we continue to update our detection systems for threats like EMOTET, SLIVER, and MIRAI. These updates ensure you have the latest indicators that were extracted by our configuration extraction systems and YARA rules.
See latest malware family profiles added to the knowledge base and the complete list of curated YARA rules in our database.
🔄 Unified Support: Google Threat Intelligence Joins the GCP Support Process. The Google TI Support Portal is the dedicated channel for technical assistance, troubleshooting, account queries and users feedback. It has now been fully integrated into the Google Cloud Platform (GCP) Support ecosystem to provide a unified experience across Google Cloud services.
🔄 Consolidation of vulnerability reporting. Google Threat Intelligence provides continuously updated, in-depth insights to help organizations navigate the evolving cyber threat landscape via curated Reports written by Google Threat Intelligence analysts. In order to reduce duplicative reporting, we are consolidating the following reports into the existing Weekly Vulnerability Exploitation Report (WVER):
- OT Vulnerability Exploitation Roundup
- Industrial Control Systems and Medical Vulnerability Advisories Reported by CISA
- Cloud Vulnerabilities
By adding new dedicated fields, such as Affects OT and Affects Cloud, to the WVER reports, we ensure you receive the same critical data with greater frequency and in a single, comprehensive view.
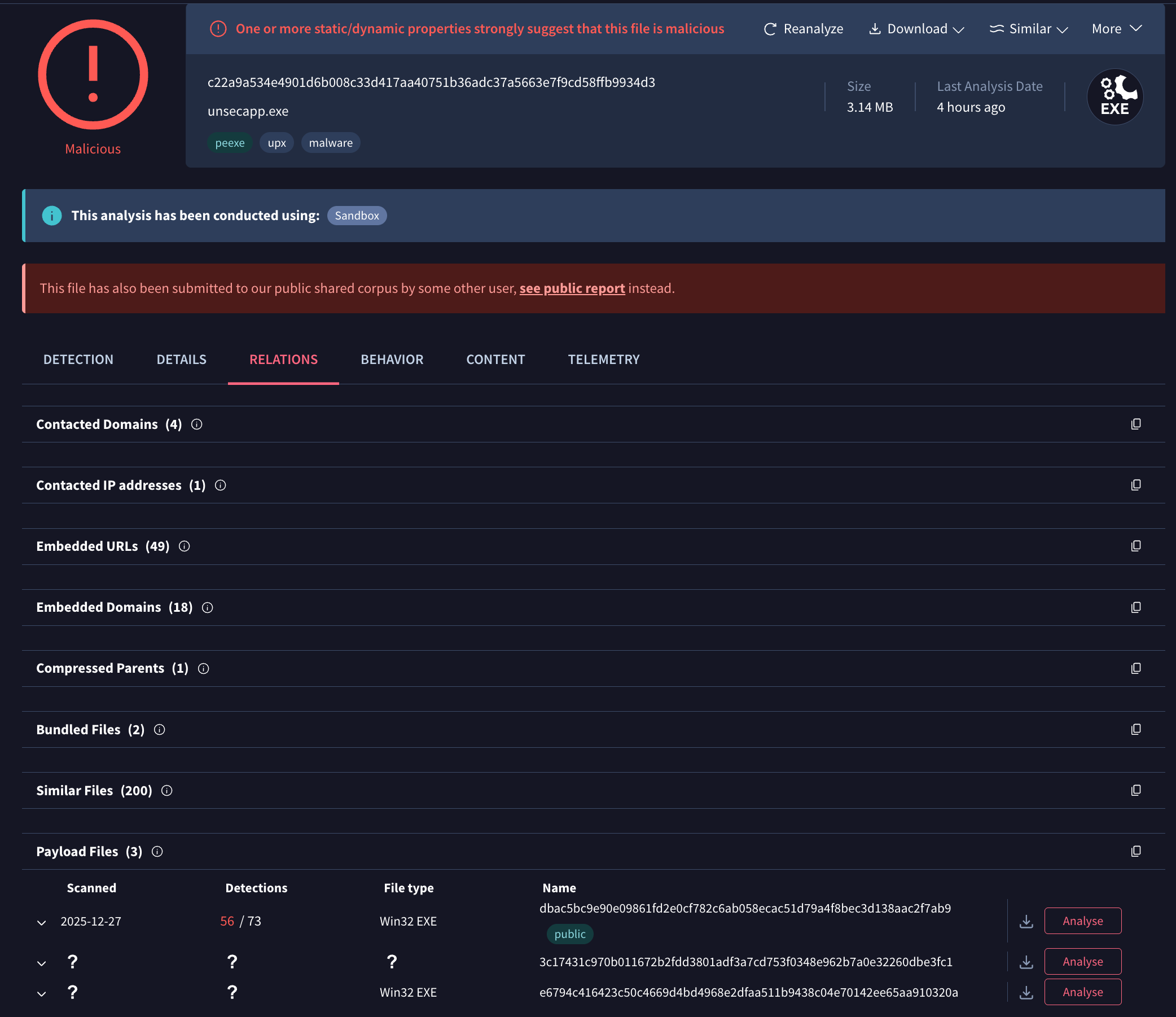
🆕 CAPE sandbox executable payload extraction now in Private Scanning. Leveraging CAPE-based sandboxing, our platform automates dynamic malware unpacking and YARA classification of captured payloads. This capability has been expanded to Private Scanning, where unpacked payloads now feature an Analysis button for independent detonation. This workflow defines parent-child relationships within the Payload Files section of the RELATIONS tab using their SHA256 hashes.
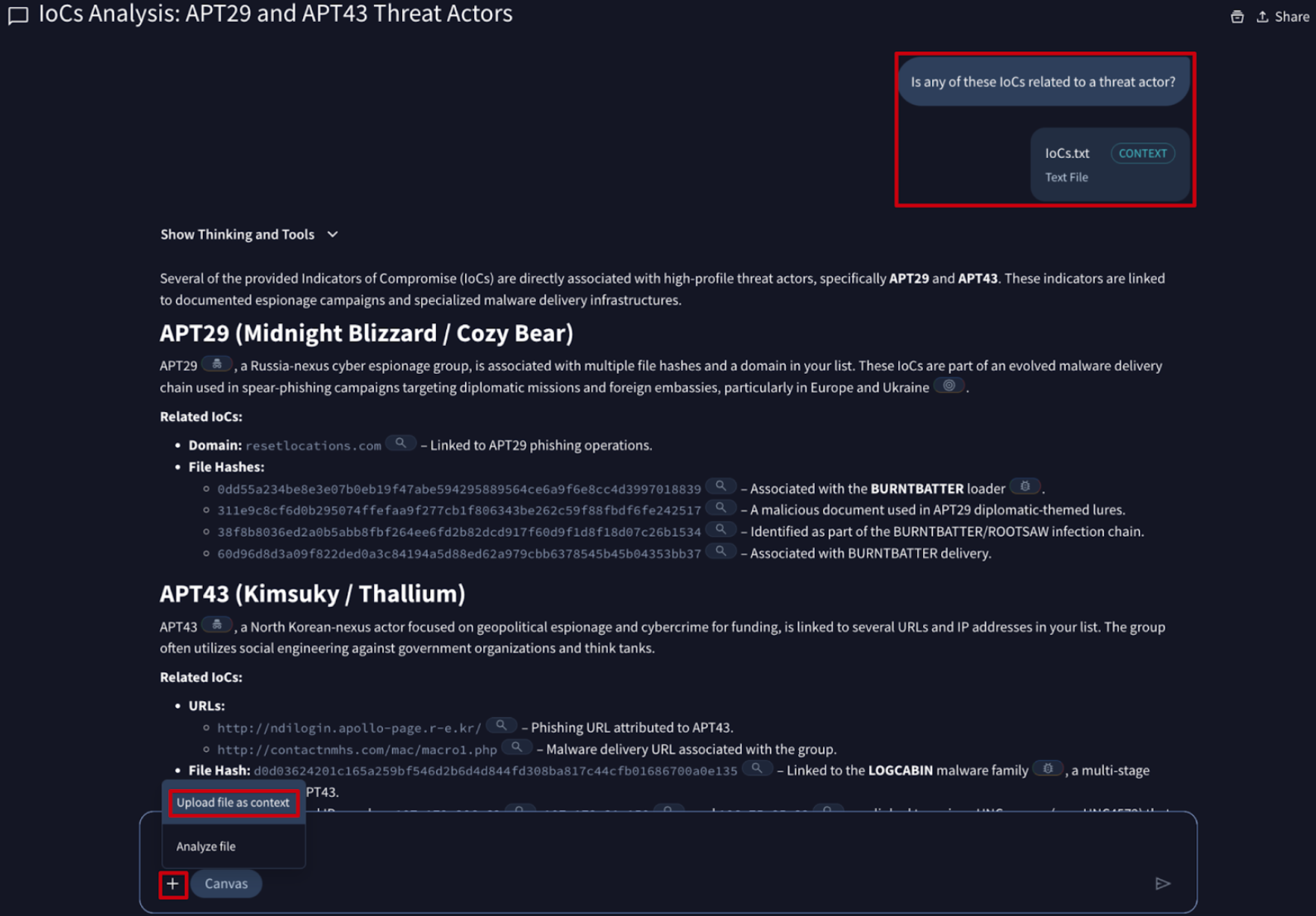
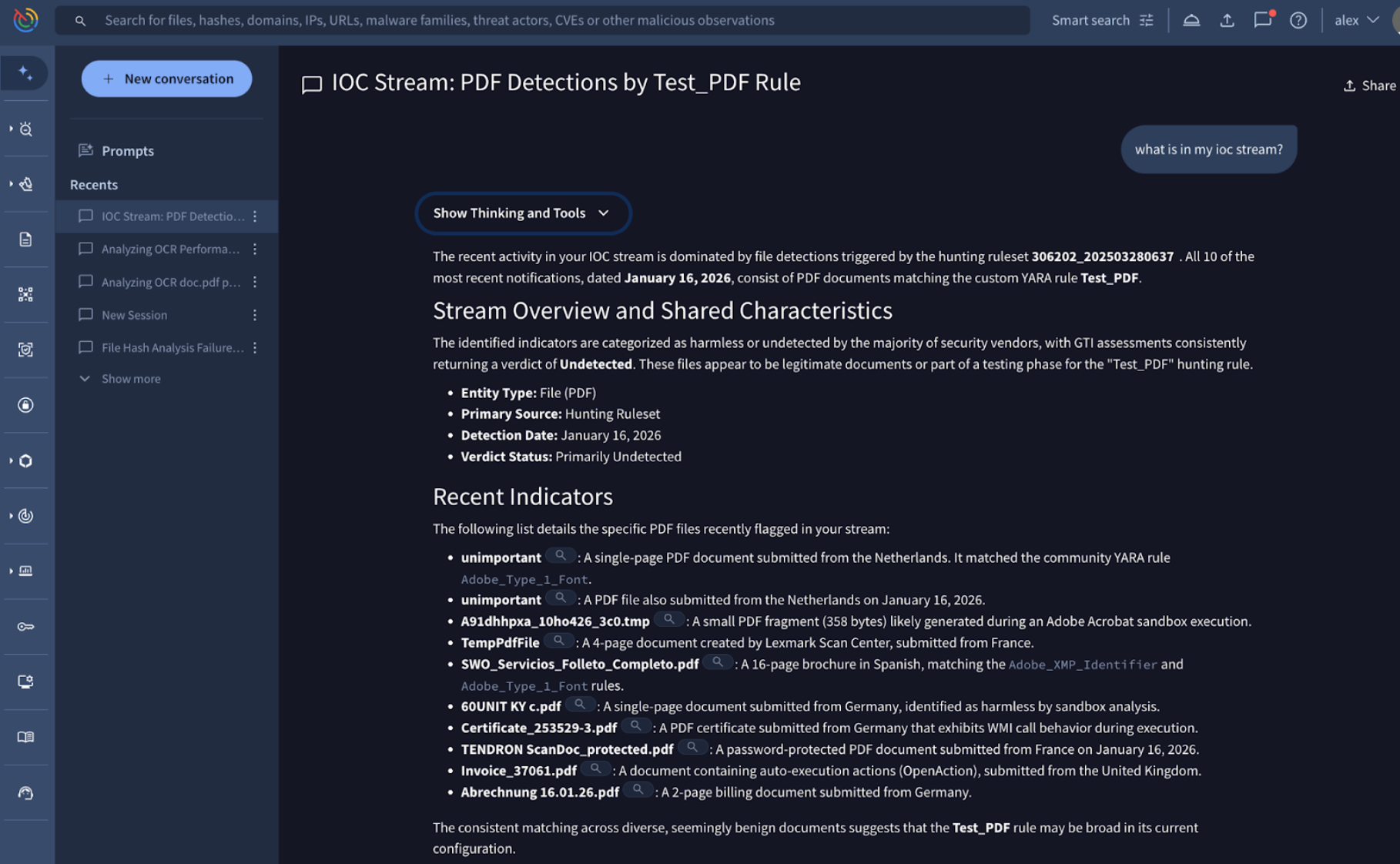
💪 Agentic AI Now Integrates with IoC Stream. Agentic is the AI-powered assistant within Google Threat Intelligence, designed to streamline complex security workflows. Acting as a force multiplier, Agentic enables security teams to leverage natural language to query expansive datasets, automate investigations, and synthesize technical reports. Agentic is now integrated with the IoC Stream, your centralized IoCs notification hub. This connection allows you to investigate notification statuses and extract immediate insights directly through the Agentic interface.
💪 Bulk IoC Investigations in Agentic Google TI. Agentic, our AI-powered assistant, now supports Bulk IoCs, enabling users to search for multiple indicators of compromise simultaneously. By uploading a context file containing your IoC list, you can now trigger a comprehensive batch investigation, significantly reducing response times and accelerating the identification of relevant threats.