November 17th, 2025 - Audit logging, Malware config ransom notes extractions, GTI Browser Extension and more
📢 Google TI Mondays & Month of UNLIMITED UI Searches. Quick reminder that for the entire month of November, all Google Threat Intelligence and VirusTotal customers will benefit from unlimited, uncapped searches when performing manual queries through the web interface (GUI) using the core VirusTotal / Search feature. Follow the Google TI Mondays and Month Of GoogleTI Search series across our social platforms every week for quick, actionable practitioner tips and product adoption advice designed to enhance your efficiency. These actionable tips are essential. Follow us to ensure you never miss the most current intelligence! #GoogleTIMondays, #MonthOfGoogleTISearch,
- Infrastructure, Brand and External Threats
- Hunting Trusted Domain Abuse
- Hunting LNK-triggered Powershell fetches
- Hunting Emerging C2 Infrastructure
💪 Detection Highlights. The Google Threat Intelligence Group and FLARE team consistently update Google TI's YARA rules and malware configuration extractors. Over this period, we’ve released YARA rules covering 9 newly tracked malware families, and enhanced our configuration extraction platform to cover 2 existing malware families. Additionally, we've updated YARA rules for 23 other known threats. This update prioritizes malware families actively observed in Mandiant incident response engagements, SecOps customer environments, and top GTI search trends.
As we track new malware families found through our research, we build and release detection signatures. Some recent examples include:
- TOXICDUST: a Windows launcher written in C/C++. TOXICDUST is capable of reading a payload file, decoding it by performing bitwise NOT operation and base64, and finally executing the resulting shellcode in memory. TOXICDUST uses SysWhispers2 to perform direct system calls. TOXICDUST is capable of evading AV and EDR software by patching BitDefender Hooking DLL and unhooking NTDLL.DLL. See its curated YARA detection rules.
- EGGJSE: a JScript Encoded dropper. It contains payloads, usually double Base64-encoded, which it decodes, drops, and runs. See its curated YARA detection rules.
- GLOWDISK: a dropper that contains an embedded decoy and executable that it drops to disk and runs. See its curated YARA detection rule .
- PIPEDOWN.DRIVE: a variant of the PIPEDOWN code family. It is a backdoor written in C++ that communicates using the Google Drive API to implement its functionality. Its capabilities include interacting with a hard-coded Google Drive resource to perform file upload, file download, file execution, and performing file listing. See its curated YARA detection rules.
In addition to providing detection rules for new and emerging threats, we continue to update our detection systems for threats like OXEEYE, BEAVERTAIL, and POISONPLUG.SHADOW. These updates ensure you have the latest indicators and YARA rules for evolving threats, some of which were extracted by our configuration extraction systems.
See latest malware family profiles added to the knowledge base and the complete list of curated YARA rules in our database.
💪 Enhanced PE and ELF Binary Behavior Detections. CAPA, a tool maintained by the FLARE team , provides human-readable explanations of suspicious behavior that a binary may exhibit when executed. Our platform runs CAPA on all PE and ELF binaries, displaying results in the BEHAVIOR tab of the UI. Lately CAPA has been updated with 22 new and 46 improved behavior detection rules, which have been fully integrated into our supported file analysis process. This enhancement adds new rules heavily focused on detecting defense evasion techniques observed in malware, including:
behavior_signature:"disable System Restore features via registry on Windows": modify the registry to disable system recovery.behavior_signature:"disable system features via registry on Windows": modify the registry to disable administrative tools like Task Manager, Windows Update, and UAC.behavior_signature:"disable Device Guard features via registry on Windows": modify the registry to disable virtualization-based security and code integrity policies.behavior_signature:"disable Windows Defender features via registry on Windows": modify the registry to disable Windows Defender.behavior_signature:"disable firewall features via registry on Windows": modify the registry to disable Windows Firewall.behavior_signature:"unload sysmon": unload sysmon minifilter driver to disable Windows System Monitor.behavior_signature:"unload minifilter driver": unload minifilter driver to disable kernel functionality.behavior_signature:"enter debug mode in .NET": enable debug privileges to manipulate processes.behavior_signature:"encrypt data using TripleDES in .NET": encrypt data using the TripleDES algorithm to conceal data.
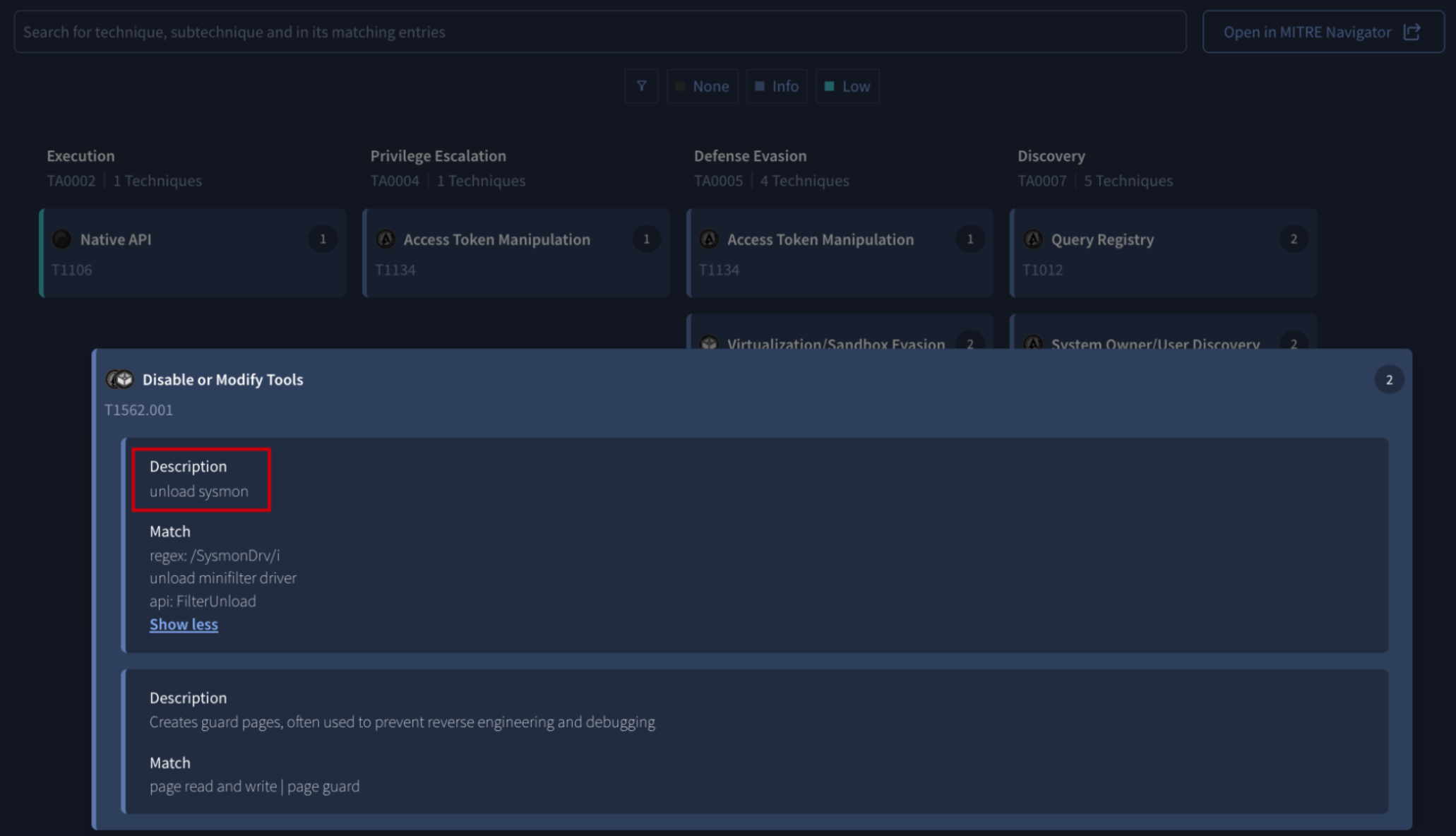
Check out CAPA’s full release notes for more details.
🆕 Google Threat Intelligence Browser Extension. We evolved the popular VT4Browsers Extension to include the power of Google Threat Intelligence to provide actionable Threat Intelligence directly in your Browser. It empowers analysts with immediate threat context & triage, investigate in-depth without context switching and seamless collaboration & tracking to stay on top of threats, scan downloads all by providing actionable Threat Intelligence directly within your browser.
Now users with a valid Google Threat Intelligence API key can activate a new, integrated investigation experience.
- New Interface: the extension adopts the visual style of the official Google Threat Intelligence interface.
- Live Investigation: IoCs are automatically highlighted/enriched on the page as you navigate, providing a Quick Summary (Hover) and Deep Dive (Click) into the GTI Widget side-panel powered by Google Threat intelligence.
- View Summary of all IoCs: a new feature to automatically collect all the detected IoCs on a webpage and open a new investigation window in the Google TI platform. You can add specific IoCs in this window directly into a new IoC collection to unlock powerful use-cases, to stay on top of the threats.
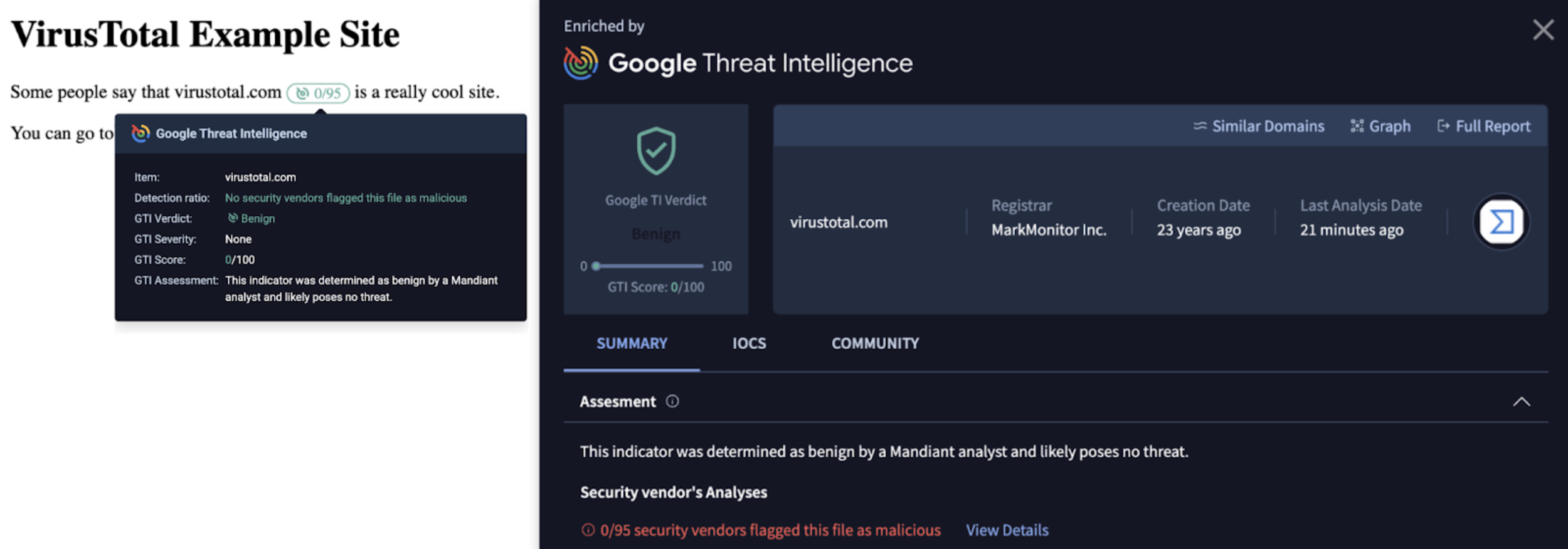
Want to try the enhanced investigation experience? Download or update the extension now:
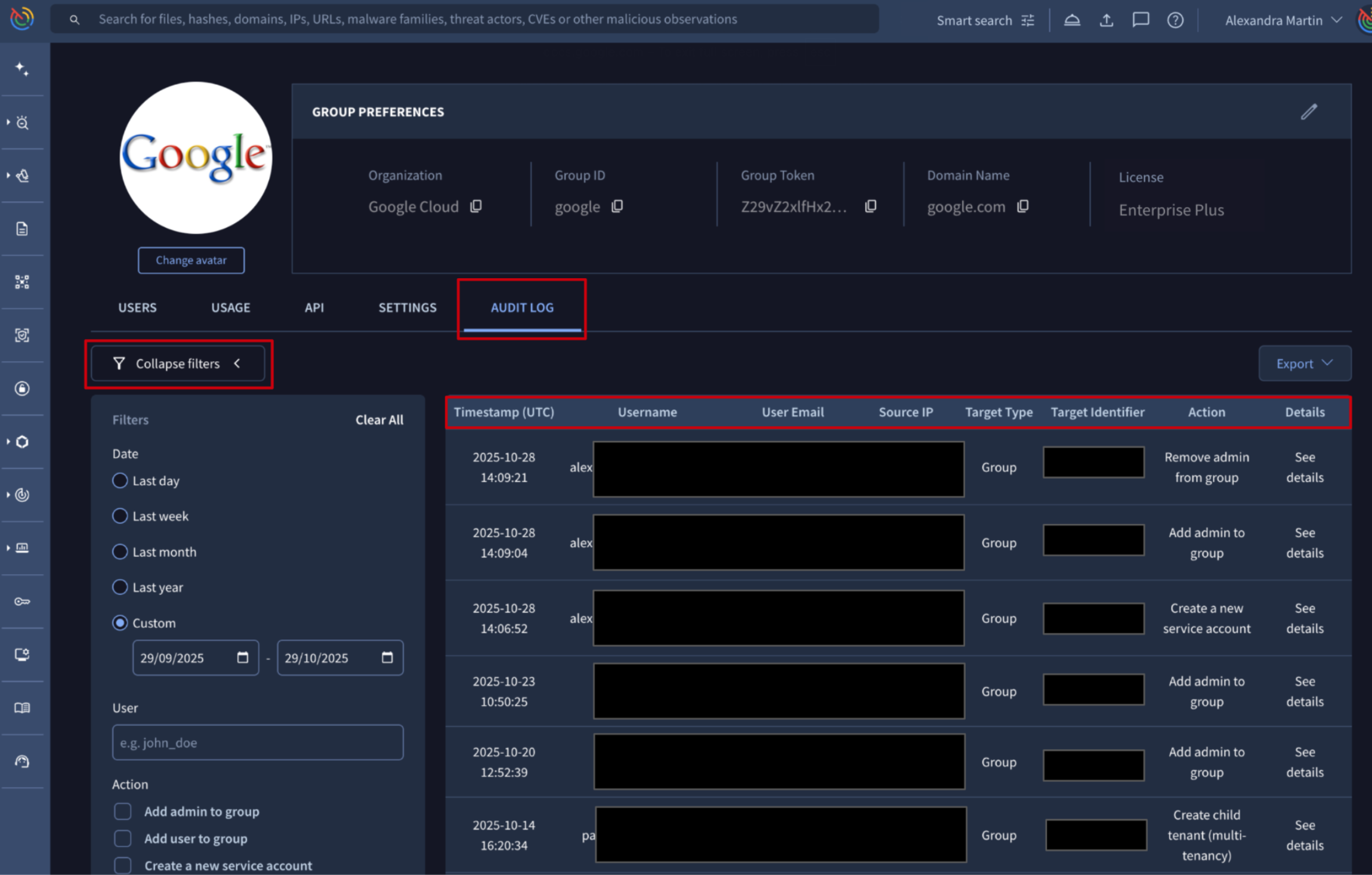
🆕 Audit Logging. The new Audit Log is an essential security and administrative tool within Google Threat Intelligence, exclusively accessible to Group Administrators. Its primary function is to track, record, and preserve a time-stamped history of all sensitive administrative actions taken across your organization’s Google TI group, covering activities performed via both the web UI and the API.
💪Extended malware configuration extraction with displayed messages. Google Threat Intelligence processes all files submitted to VirusTotal, as well as some other Mandiant/Google sources, and identifies popular malware families, invoking malware configuration extractors where applicable. We’ve updated our extractors to also include any messages displayed back to users, such as ransom notes. See example.
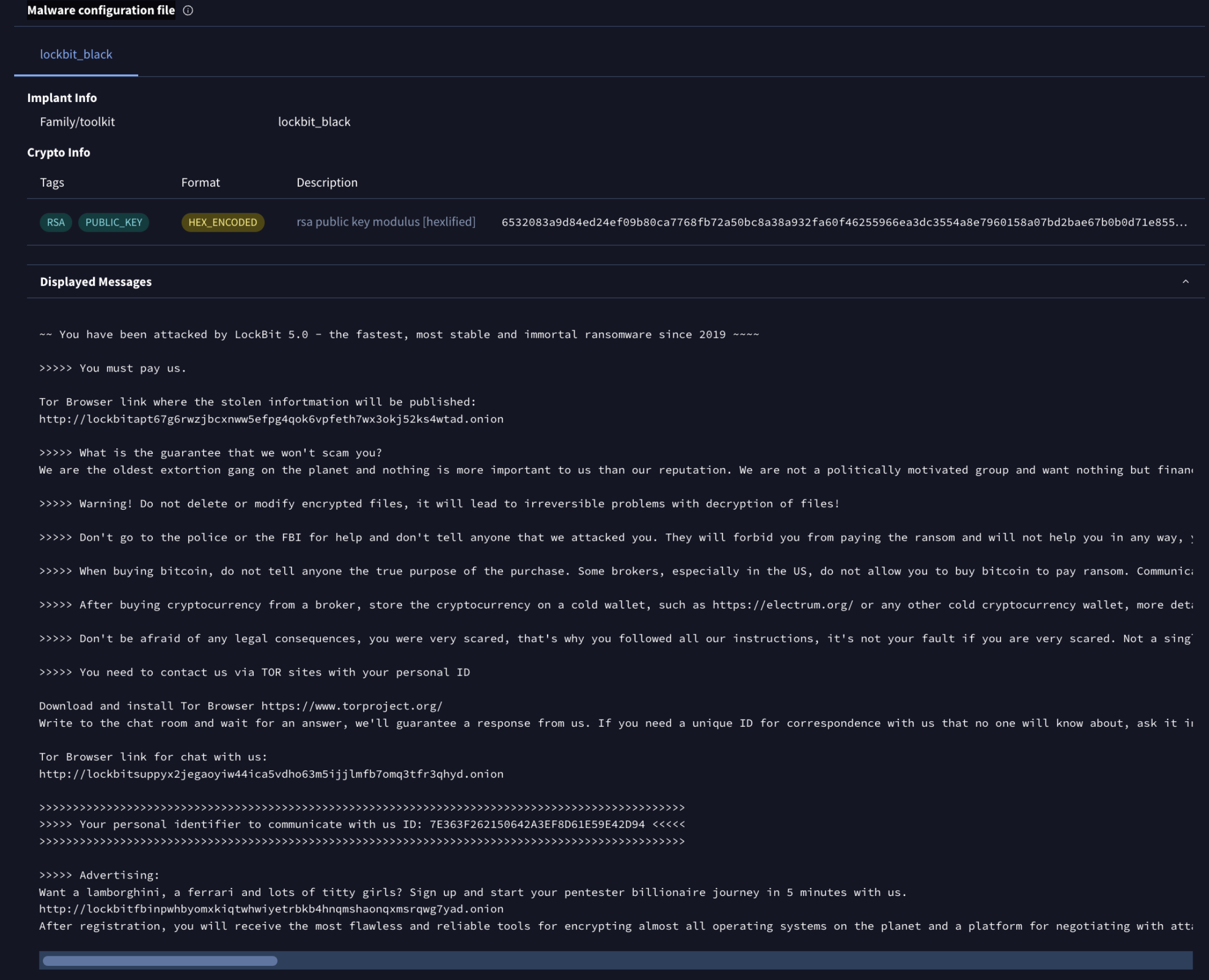
This field has also been indexed and allows you to hunt for specific malware families, for example: malware_config:"guarantee that we won't scam you".
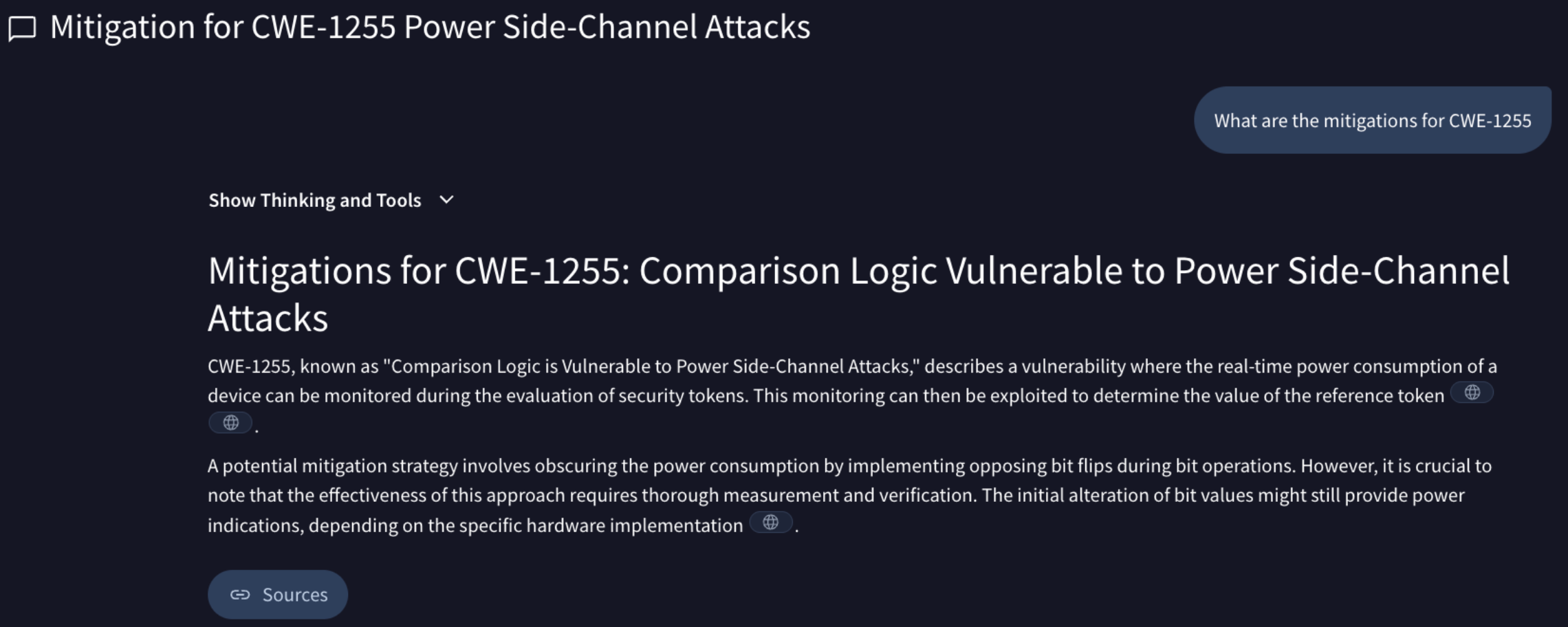
💪 Agentic now has the capability to provide mitigation advice. Our Agentic conversational assistant designed to provide instant, contextual, and actionable threat intelligence by answering complex, natural language queries about security topics, indicators, and entities has been improved to answer specific mitigation strategies and defensive controls related to a given MITRE ATT&CK TTP, CAPEC ID, or CWE ID. This enhancement allows for faster pivoting from threat identification to defense planning by providing immediate, actionable guidance on how to prevent or limit the impact of specific attacker behaviors and vulnerabilities.