November 24th, 2025 - Improved Agentic capabilities, new Integrations and more
📢 Google TI Mondays & Month of UNLIMITED UI Searches. Quick reminder that for the entire month of November, all Google Threat Intelligence and VirusTotal customers will benefit from unlimited, uncapped searches when performing manual queries through the web interface (GUI) using the core VirusTotal / GTI search feature. Follow the Google TI Mondays and Month Of GoogleTI Search series across our social platforms every week for quick, actionable practitioner tips and product adoption advice designed to enhance your efficiency. These actionable tips are essential. #GoogleTIMondays, #MonthOfGoogleTISearch.
- VT4Browsers + Google TI
- Hunting Malware with Valid Signatures
- Sigma Hunter: Find the Gaps
- Hunting Recently Registered DGA domains
- Hunting Stealers via PDB Metadata
💪 Detection highlights. The Google Threat Intelligence Group and FLARE team consistently update Google TI's YARA rules and malware configuration extractors. This week, we’ve released YARA rules for 9 newly tracked malware families and updated existing YARA rules for 31 families. We've also enhanced our configuration extraction platform with updates for 1 existing malware family. This update prioritizes malware families actively observed in Mandiant incident response engagements, SecOps customer environments, and top Google TI search trends.
As we track new malware families found through our research, we build and release detection signatures. Some recent examples include:
- RAINWIZARD: a Windows backdoor written in Rust. RAINWIZARD uses OneDrive Graph API for command and control. Backdoor capabilities include file download, upload, file listing, command execution using cmd.exe or PowerShell and Windows registry run key modification.
- SAGEWAVE: a launcher written in Java that acts as a servlet filter. SAGEWAVE registers a specific URL pattern to receive attacker traffic over HTTP to a compromised Java web server and expects to receive an encrypted Java class from an attacker in the HTTP request. The payload is decrypted using AES-128-CBC with a hard-coded key and IV and is parsed as a ZIP file. SAGEWAVE loads Java class files into memory from the decrypted ZIP archive, and then executes the "httpReq" method from a class with a filename ending in ".Cli". SAGEWAVE has been observed being dropped by SAGELEAF and is suspected to be used to deploy a payload similar to GOLDTOMB. See its curated YARA detection rules.
- CHARON: a ransomware written in C++ that uses multiple threads to partially encrypt files on the localhost as well as in network shares. Samples have been observed terminating services and processes related to endpoint-agents and backup services. The targeted services belong to software made by eastern and western companies. CHARON samples also include an embedded driver, Dark-Kill, to gain kernel privileges and terminate more tamper-resistant AV and EDR software. See its curated YARA detection rules.
In addition to providing detection rules for new and emerging threats, we continue to update our detection systems for threats like OXEEYE, DONUT, and UPATRE. These updates ensure you have the latest indicators, including those extracted by our configuration extraction systems.
See latest malware family profiles added to the knowledge base and the complete list of curated YARA rules in our database.
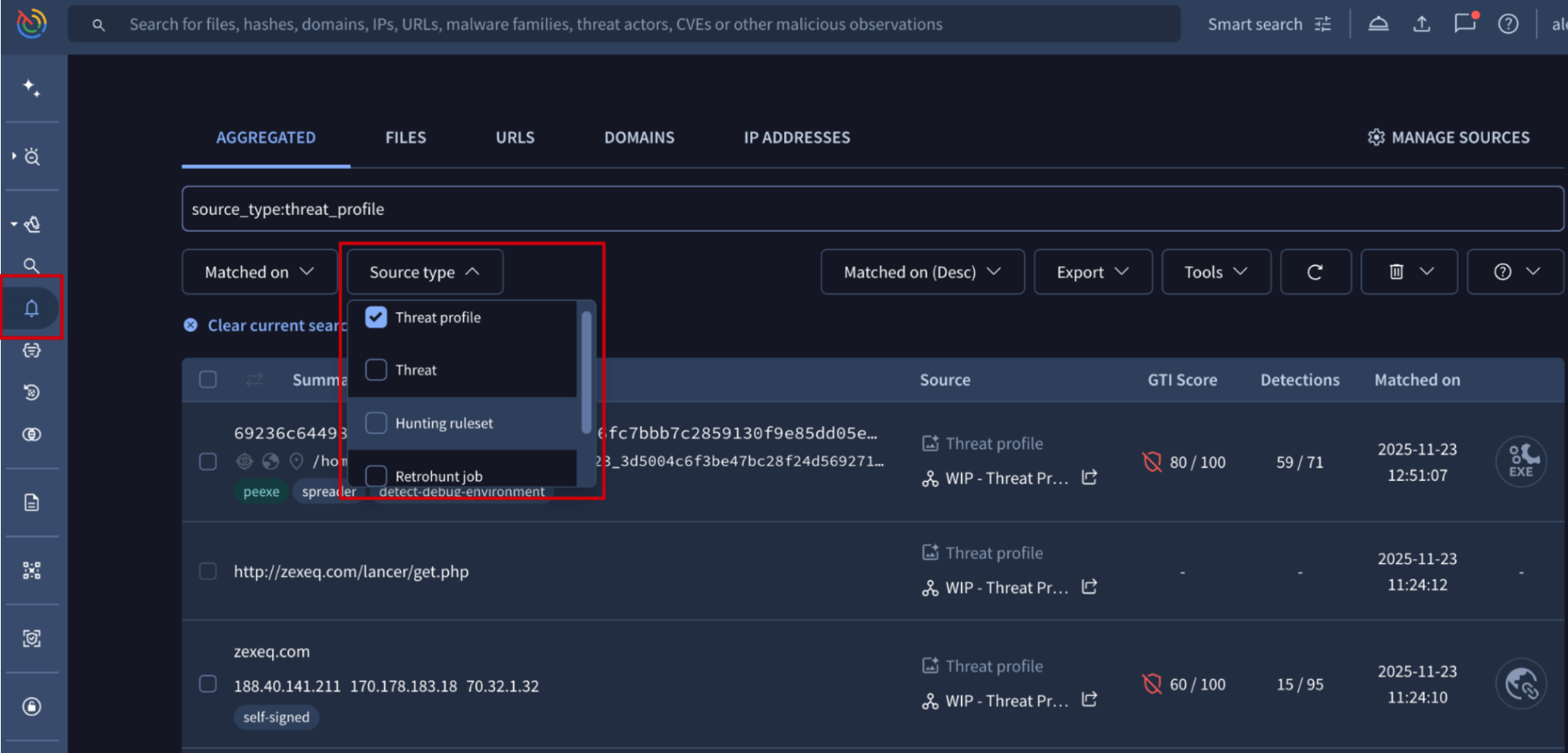
💡 Remember! Private Scanning + Code Insight. Private Scanning is a dedicated service that allows organizations to submit suspicious files and URLs for analysis while guaranteeing that IoCs, their execution data, and the resulting report remain completely confidential and are not shared publicly / with the community.
- Remember that you can choose between static analysis only or static and dynamic detonation via the "Try to detonate in dynamic analysis sandboxes" checkbox.
- Remember that the Code Insight analysis, which uses Gemini AI to assist malware analysts by generating natural language summaries of a file's functionality, is provided for private file analysis reports whenever possible.
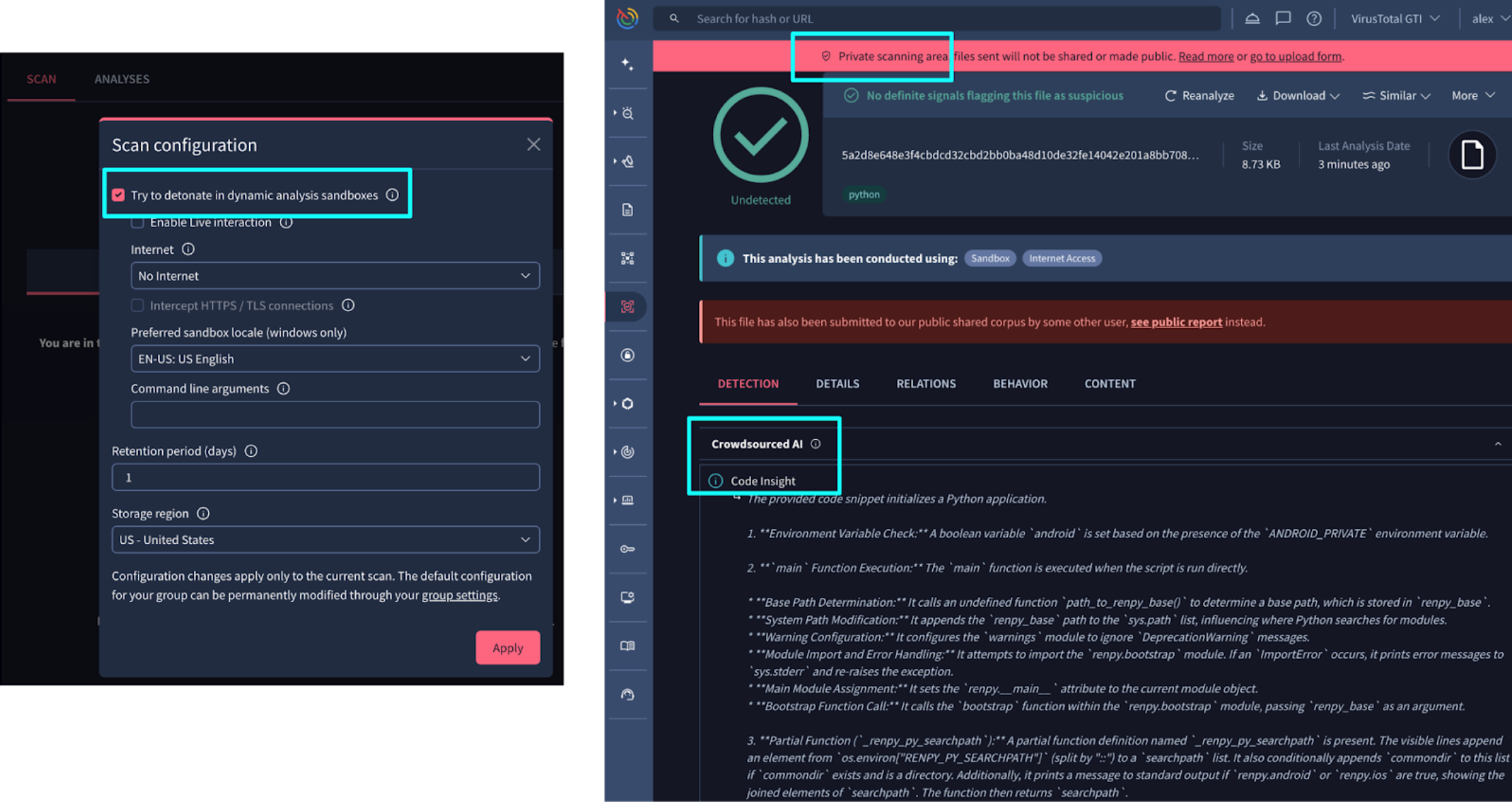
💪 Improved trends visibility via Agentic. Agentic, our nextgen autonomous threat intelligence foundation that delivers instant, contextual, and actionable threat intelligence by fielding complex, natural language queries about security topics, indicators, and entities, has been upgraded to provide immediate visibility into prevalent threat data by running advanced queries to identify top trends over specific periods of time. Examples of supported queries include:
- "Give me the mutexes most used by Emotet in the USA in the last 2 weeks."
- "Give me the vhash most used by APT44 in the last month in the USA."
- "Give me the countries where APT44 has used 035056655d155512e1z14z7dhz1020022fz most in the last month."
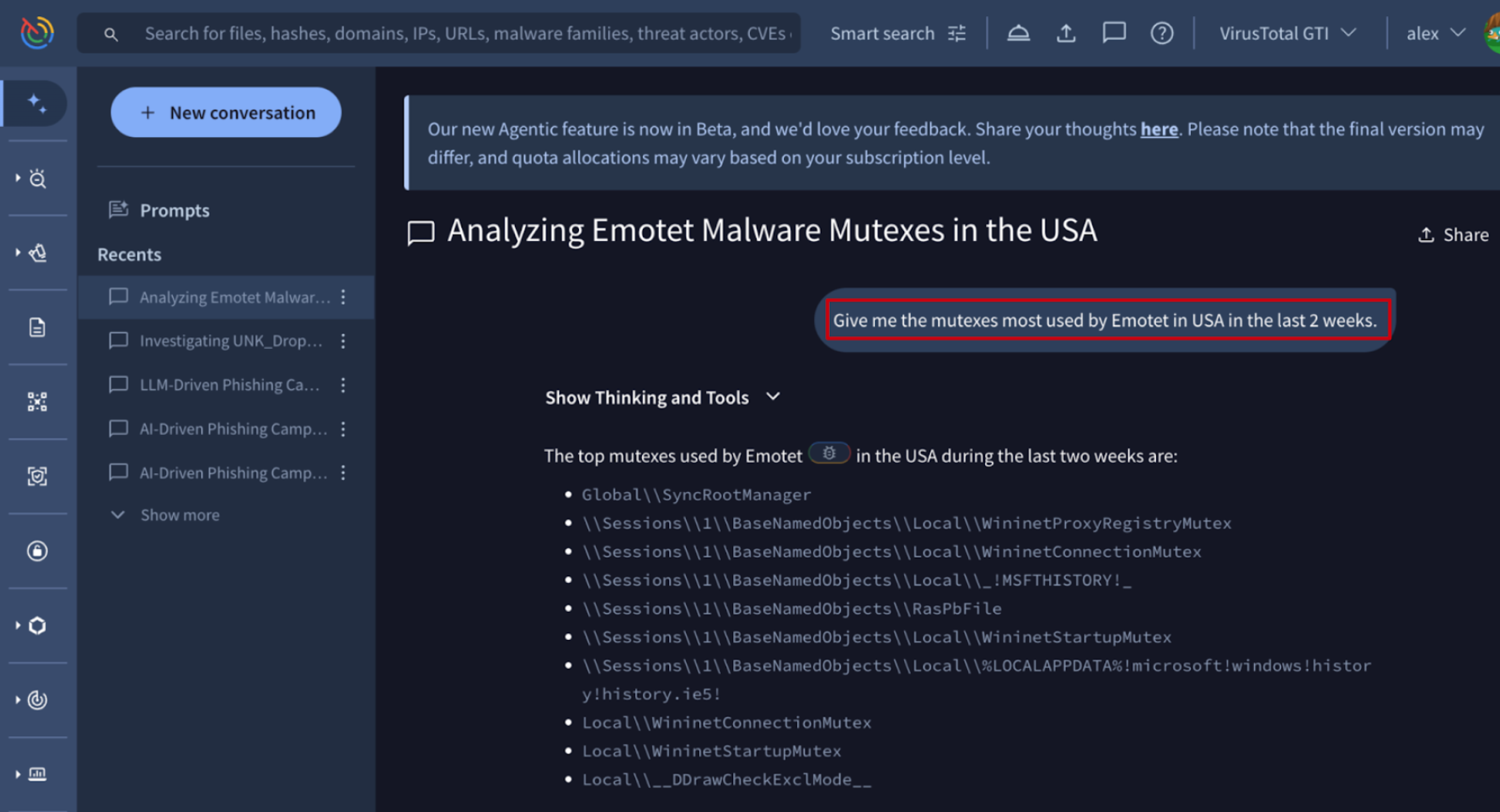
🆕 Providing clarity regarding Google TI objects + web citations vs artifact attachments in Agentic. We have improved the organization of contextual data within the Agentic conversations. Instead of a single source button, two new, distinct buttons are now displayed:
- Sources button, at the end of the conversation, dedicated to accessing the Threat Intelligence objects and external web citations used to formulate the conversation responses.
- An attachments button next to the Share one, is now your way to view files and other artifacts uploaded during the conversation.
Sources and artifacts are no longer separated into two tabs. Instead, each item is displayed and accessed via its own dedicated button.
🆕 New outbound 3rd-party integrations. Integrations are vital to operationalizing Google Threat Intelligence (GTI), converting raw security insights into immediate, effective defensive action. These crucial integrations help organizations eliminate siloed data and dramatically enhance their security ecosystem, boosting efficiency and accelerating Mean Time to Resolution (MTTR).
New integrations released:
- Cyware - See demo here
- Sumologic
- CrowdStrike
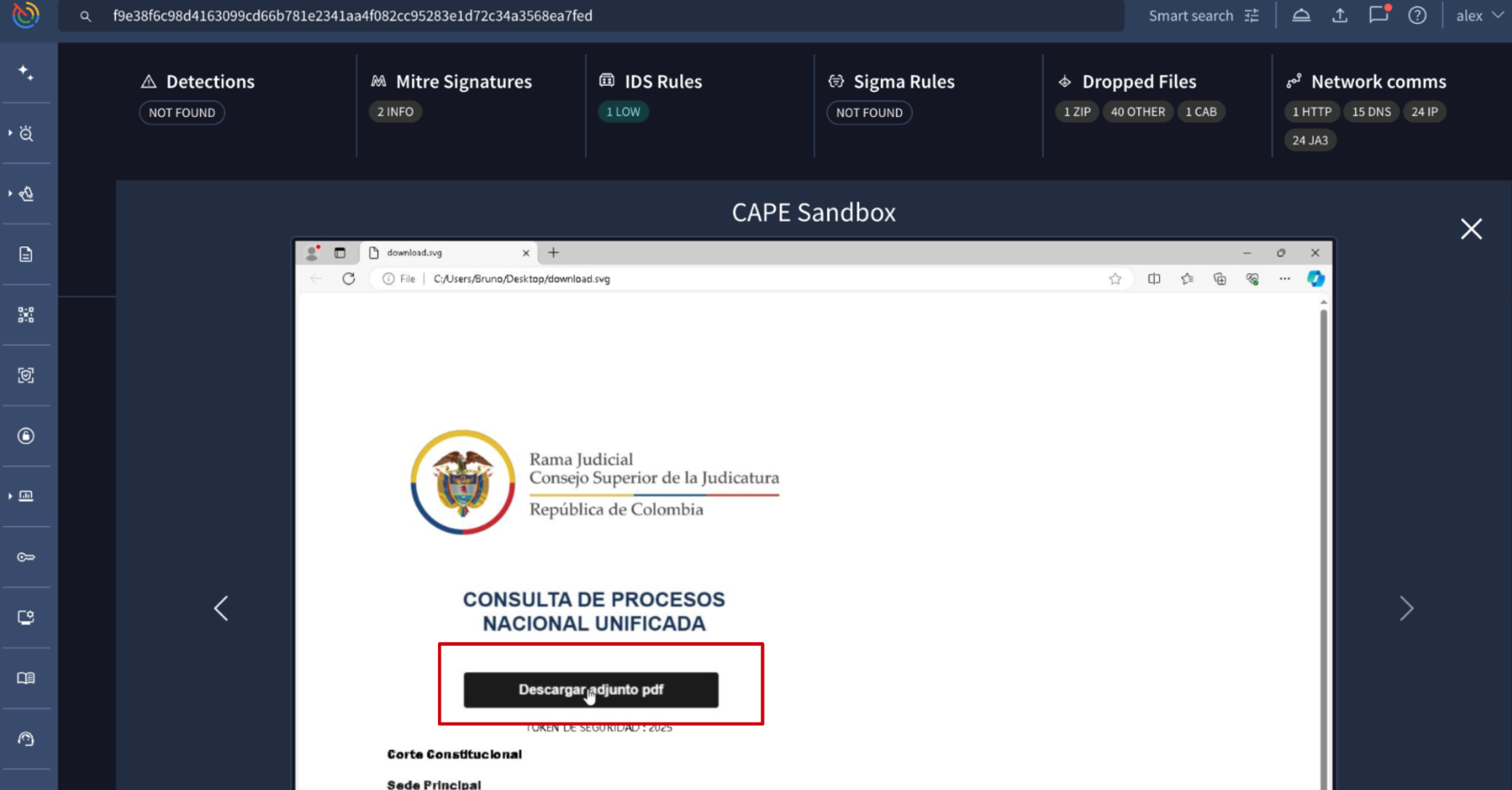
💪 AI-enhanced sandbox detonation for deeper behavioral analysis. The Behavior tab within a file's analysis report showcases detailed behavioral insights, which are generated by executing the uploaded file across Google Threat Intelligence's multi-environment sandboxes. We've introduced AI-driven interaction capabilities to our detonation engine. This enhancement allows the sandbox to autonomously click and interact with samples, ensuring they fully execute and reveal their hidden behaviors, resulting in more complete and in-depth behavioral reports. File types affected by this improvement are:
- SVG (Scalable Vector Graphics)
- MSC (Microsoft Management Console Snap-ins)
- HTA (Microsoft HTML Applications)
- Emails
See example
💪 IoC Stream Notification Retention Extended to 30 Days. IoC Stream is our IoC centralized notification hub that aggregates all IoCs coming from Livehunt or Retrohunt matches, Threat Profile and Followed Threat Intelligence Objects (Threat Actor, Campaigns, Malware & Software, IoC Collections, Reports, Vulnerabilities) that were updated with new IoCs. The retention period for IoC notifications in the IoC Stream has been significantly increased from 1 week (7 days) to 30 days. This update provides users with a substantially longer historical buffer, offering greater flexibility for data synchronization, analysis, and comprehensive retrospective threat hunting.