February 2nd, 2026 - Agentic General Availability (GA), now accessible from Private Scanning reports, and new Practitioner-Oriented Content
📢 Google TI Mondays. Quick reminder to Follow the Google TI Mondays series across our social platforms every week for quick, actionable practitioner tips and product adoption advice designed to enhance your efficiency. These actionable tips are essential. #GoogleTIMondays
💪 Detection Highlights. The Google Threat Intelligence Group and FLARE team continuously enhance Google TI's detection capabilities. This week, we've released YARA rules for 6 newly tracked malware families and updated YARA rules for 10 existing families. Our configuration extraction platform also received an update for 1 malware family. Our content prioritization focuses on threats actively observed in Mandiant incident response engagements, Google SecOps customer environments, and top Google TI search trends.
As part of our ongoing research into emerging threats, we've added detection signatures for several new malware families. Some recent examples include:
- VOIDLINK: a modular Linux command and control (C2) framework written in the Zig programming language. It is optimized for cloud and containerized environments, utilizing eBPF and LKM-based rootkits for persistence and stealth. The framework features an extensive plugin API and adaptive evasion strategies that adjust behavior based on the detected security products and cloud provider (AWS, GCP, Azure, Alibaba, and Tencent). See its curated YARA detection rules.
- CORESTING: a file infector written in C++ designed to modify the Windows termsrv.dll file, which is responsible for Remote Desktop Services. Its primary function is to enable multiple concurrent Remote Desktop sessions or bypass licensing restrictions by patching specific byte patterns within the dynamic-link library (DLL). See its curated YARA detection rule.
- ECHONOISE: a Linux backdoor written in Rust. ECHONOISE can communicate with its command and control server using multiple protocols including TCP, KCP, WebSocket and QUIC. ECHONOISE capabilities include command execution, socks proxying, port forwarding, file upload, download, deletion and execution. See its curated YARA detection rule.
Beyond tracking new threats, we also continuously update our detection content for known and prevalent malware families. This week's updates include enhanced YARA rules and configuration extraction capabilities for threats such as: VIDAR, PALEBEAM, DOGCALL
These updates ensure you have the most current indicators and insights derived from our analysis.
See latest malware family profiles added to the knowledge base and the complete list of curated YARA rules in our database.
📢 Mastering the Hunt: New Practitioner-Oriented Content. Threat hunting is only as good as the intelligence backing it. To help you put that intelligence into action, we’ve released two new practitioner-focused blog posts that walk you through hunting specific threats on our platform. We dive deep into real-world scenarios, ranging from tracking a widespread Infostealer campaign to dissecting a malicious "Electronic Invoice" EPUB file.
📢Agentic is now GA. We are thrilled to announce that Agentic, our multi-language AI-powered conversational platform, has moved from public preview to General Availability (GA) for all Google Threat Intelligence Enterprise and Enterprise + customers. This milestone marks a significant step in democratizing high-level threat research by putting an expert AI assistant at the fingertips of every security analyst.
Read more: Transforming Defense Workflows with Agentic
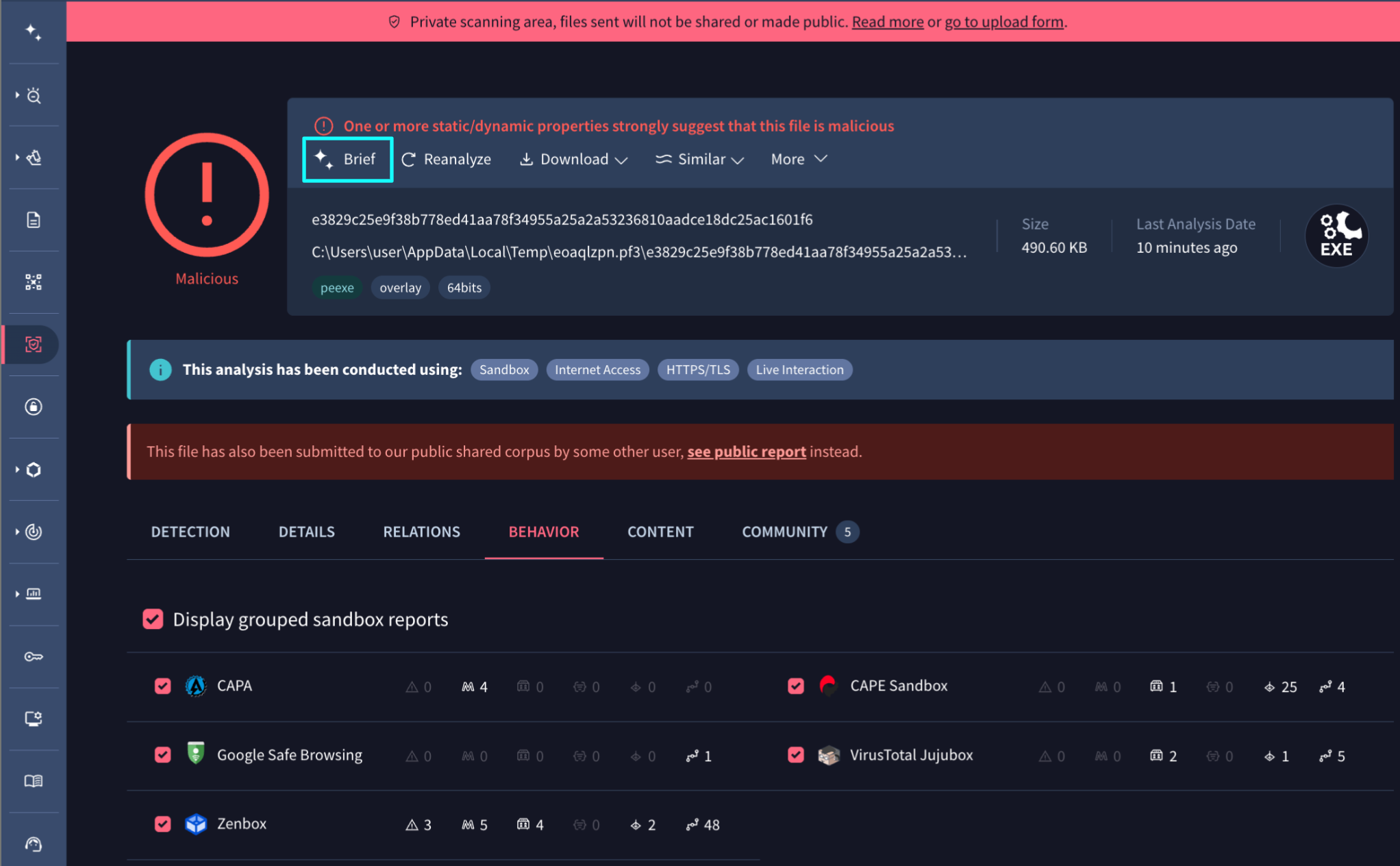
💪 Intelligence at Speed - Instant Executive Briefs Powered by Agentic. Agentic conversational AI platform was integrated across all public IoC analysis reports (files, URLs, domains, IP addresses) and now we have extended this functionality to Private Scanning as well. This capability is accessed via a single 'Brief' button at the top of private files and URLs reports, which automatically initiates a conversation within the Agentic interface, allowing the AI to produce an executive summary focused specifically on the selected IoC.