December 8th, 2025 - NEW Saved Searches feature, Richer Intelligence Context, Artifact Download Capabilities and more
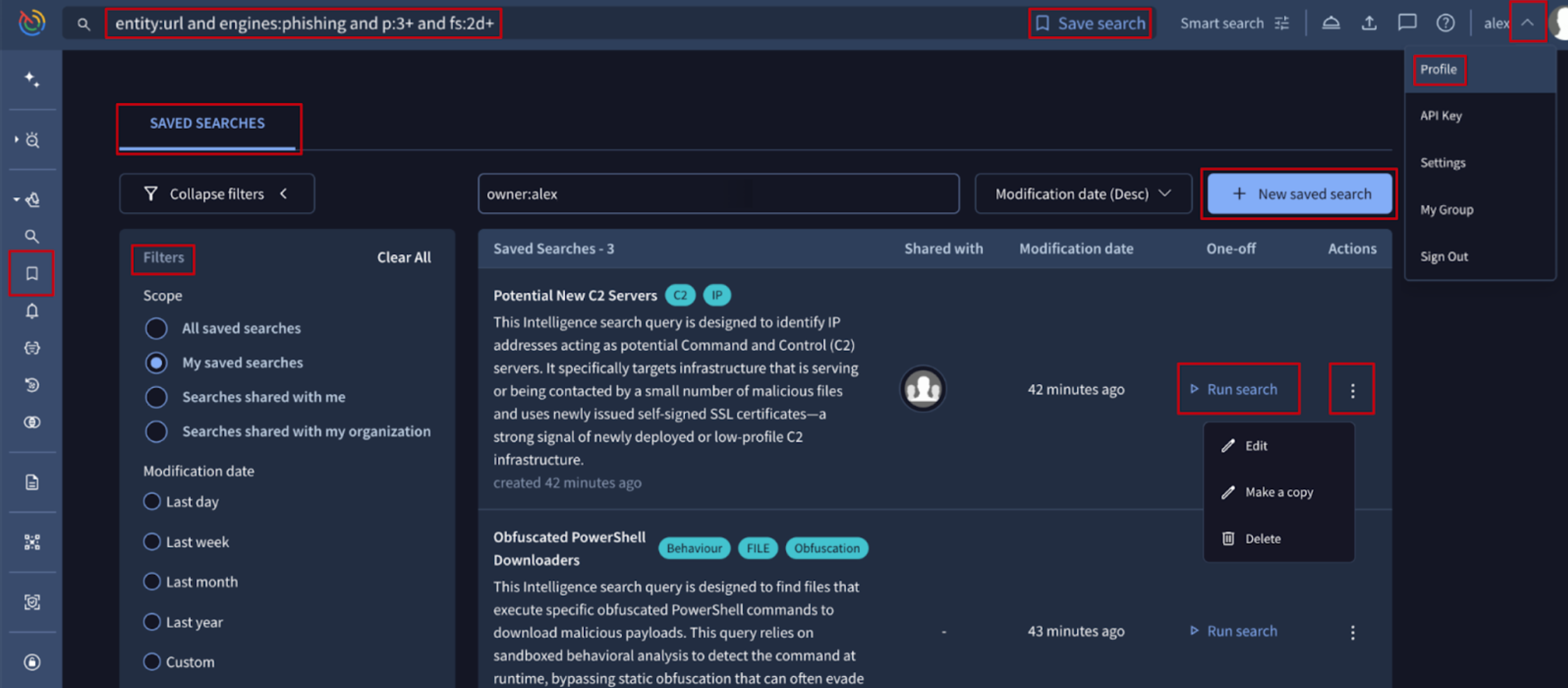
🆕 Saved Searches. The Intelligence Search feature allows users to execute complex and powerful queries against our expansive dataset of malicious indicators, enabling threat hunters to uncover infrastructure, track campaigns, and identify evolving threats. Instead of manually reassembling the required search modifiers for a specific use case every time a search has to be performed, now users can save queries by creating Saved Searches to efficiently reuse or frequently execute threat intelligence searches across our vast database of IoC analysis reports (files, URLs, domains, IP addresses).
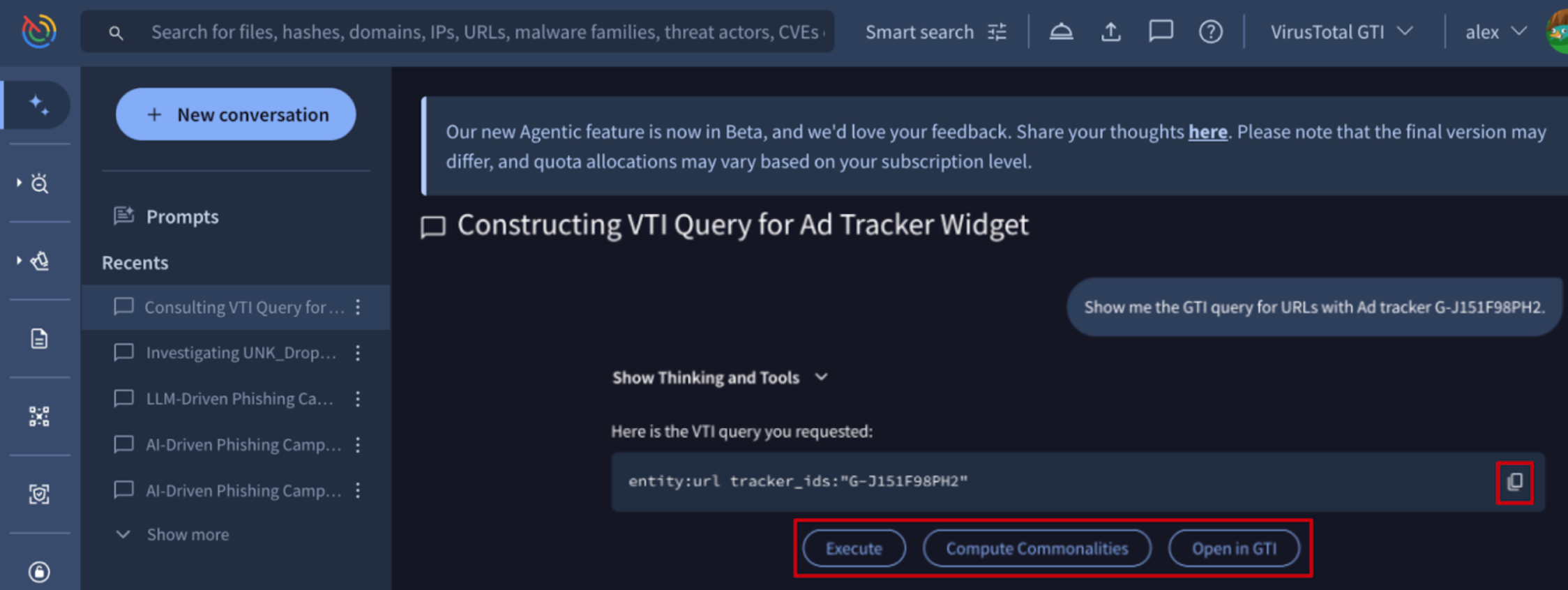
🆕 Agentic can now construct intelligence searches / queries. Agentic is the AI-powered assistant within GTI, designed to simplify and streamline complex threat intelligence tasks. Users can now leverage natural language to automatically generate complex intelligence searches / queries for IoCs (files, URLs, domains, IP addresses). This new capability eliminates the previous requirement for analysts to manually consult and apply a wide array of search modifiers, significantly speeding up IoC investigation and improving search accuracy. Additionally, the tool allows users to:
- Copy the resulting query
- Open it in the platform without running it to be able to modify it needed before running it
- Execute it
- Compute commonalities of the matched IoCs
📢Google TI Mondays. Quick reminder to Follow the Google TI Mondays series across our social platforms every week for quick, actionable practitioner tips and product adoption advice designed to enhance your efficiency. These actionable tips are essential. #GoogleTIMondays
💪 Detection highlights. The Google Threat Intelligence Group and FLARE team consistently update Google TI's detection content. This week, we focused on updating existing malware family coverage with both YARA and malware configuration extractors. The teams updated our detections for malware families like VIDAR, POISONPLUG.SHADOW, and PAPERPUCK. These updates ensure you have the latest indicators that were extracted by our configuration extraction systems.
💪 Enhanced PE and ELF Binary Behavior Detections. CAPA, a tool maintained by the FLARE team , provides human-readable explanations of suspicious behavior that a binary may exhibit when executed. Our platform runs CAPA on all PE and ELF binaries, displaying results in the BEHAVIOR tab of the UI. Lately CAPA has been updated with 21 new and 10 improved behavior detection rules, which have been fully integrated into our supported file analysis process. This enhancement adds new rules focused on defense evasion, anti-analysis, and system manipulation observed in malware, including:
- behavior_signature:"get .NET assembly entry point": resolve assembly entry point to dynamically execute code.
- behavior_signature:"patch Antimalware Scan Interface function": tamper with AMSI to evade detection.
- behavior_signature:"acquire load driver privileges": enable privileges to load kernel drivers.
- behavior_signature:"detect mouse movement via activity checks on Windows": detect mouse movement to evade sandboxes.
- behavior_signature:"enumerate minifilter drivers": list filesystem filter drivers.
- behavior_signature:"create routing table entry": modify network routing tables.
- behavior_signature:"communicate using FTP": transfer data via FTP.
- behavior_signature:"packed with DXPack": identify binaries packed with DXPack.
- behavior_signature:"decrypt data using AES via .NET": decrypt AES data using .NET APIs.
See example.
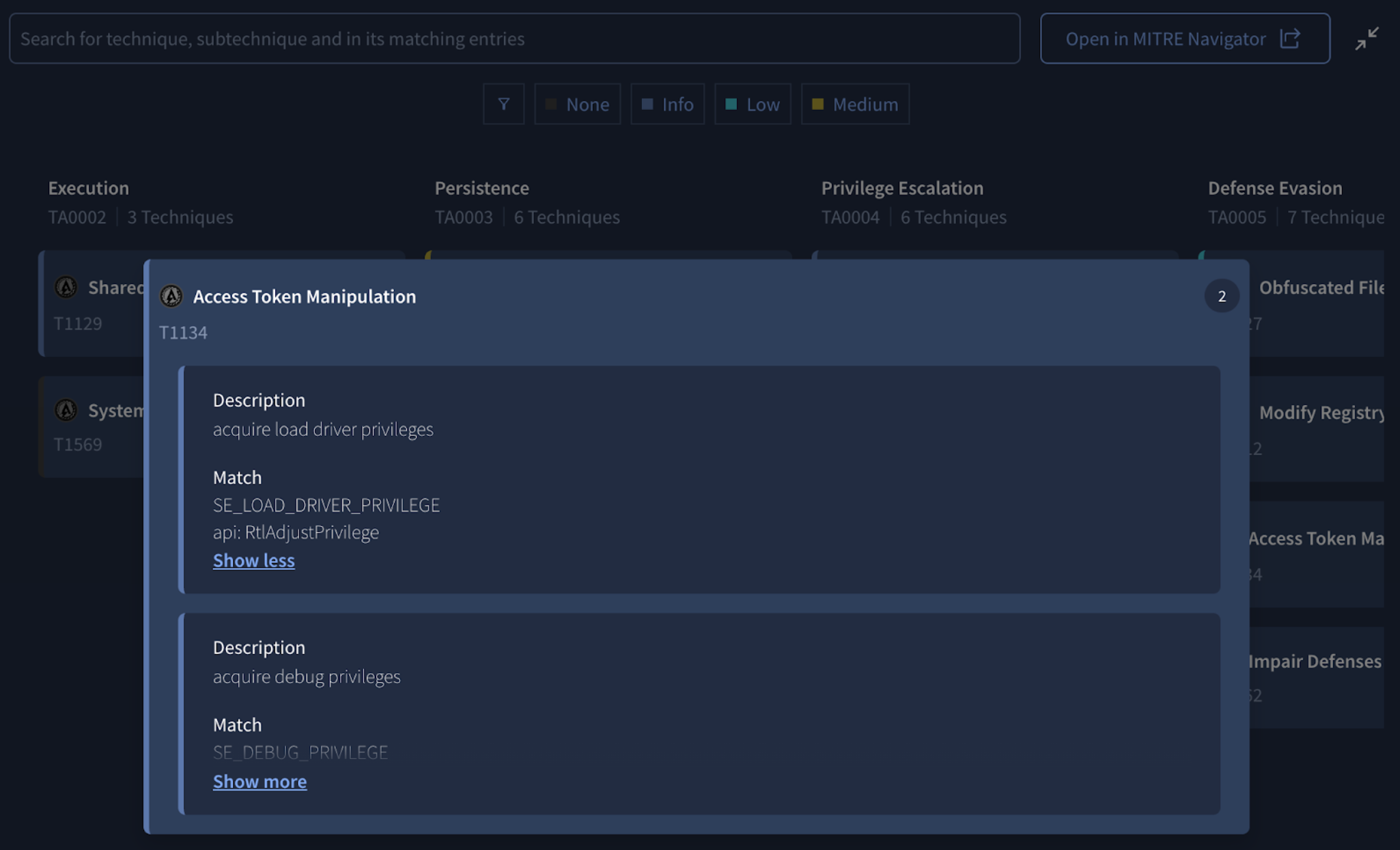
Check out CAPA’s full release notes for more details.
🆕 Intelligence at Speed - Instant Executive Briefs Powered by Agentic. We have integrated the Agentic Conversational AI platform across all major Threat Intelligence object list views (such as Threat Actors, Malware & Tools, Campaigns, IoC Collections, Reports, and Vulnerabilities). This new capability is accessed via a single Brief button. After selecting a set of objects, clicking the Brief button automatically initiates a conversation within the Agentic interface, allowing the AI to produce an executive summary focused specifically on the selected entities' recent activity.
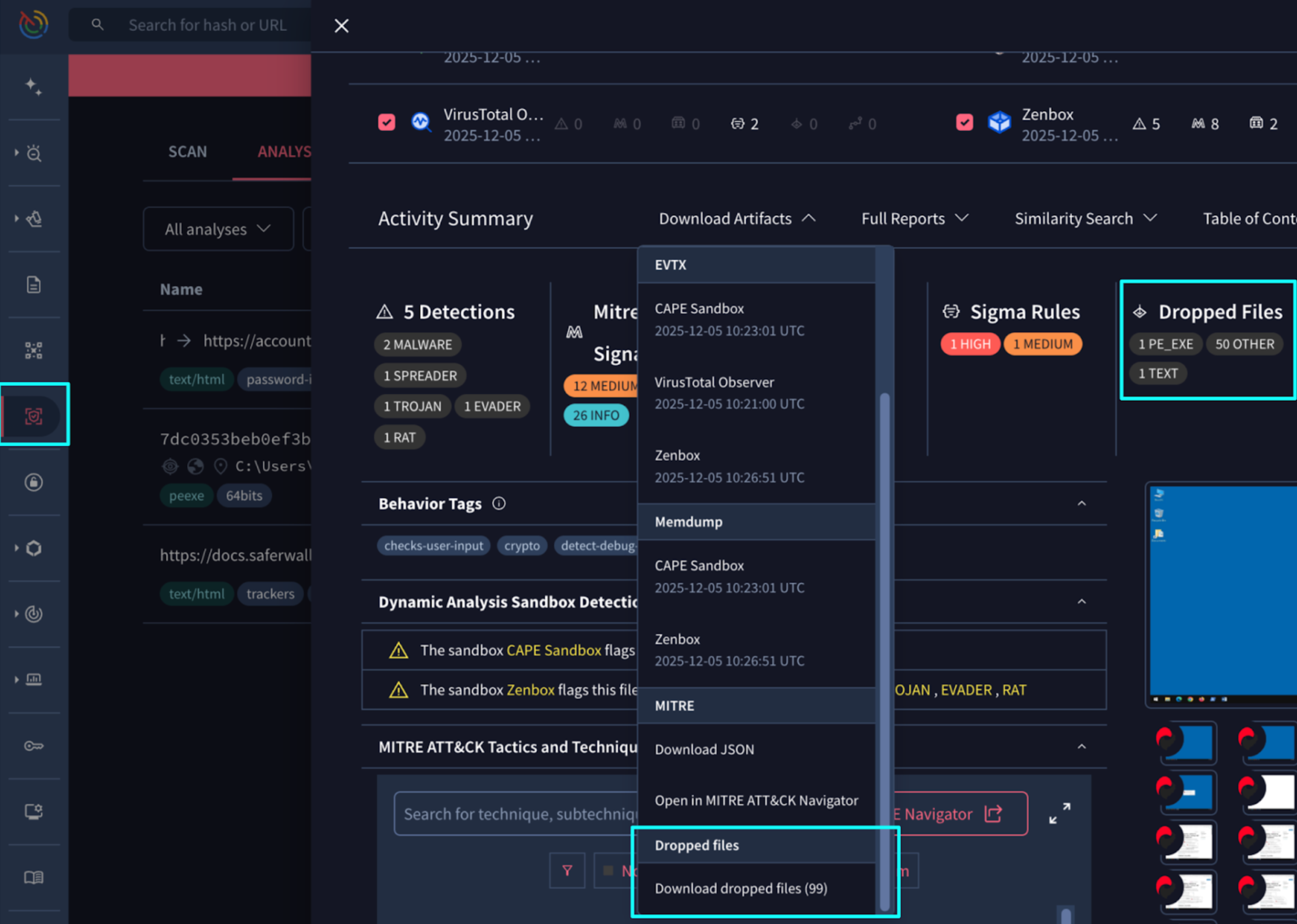
🆕 Download Dropped Files from Private Sandboxes. Our Private Scanning service captures the complete runtime profile of analyzed files. By executing samples in multiple private sandboxes, we record all dropped files, network traffic, and system modifications, which are detailed in the BEHAVIOUR tab of each file analysis report. You can now download a single, aggregated ZIP file containing all dropped files generated during a private dynamic analysis execution. This new functionality simplifies the transition from our platform to a local, isolated environment for deeper, hands-on forensic investigation of related artifacts.
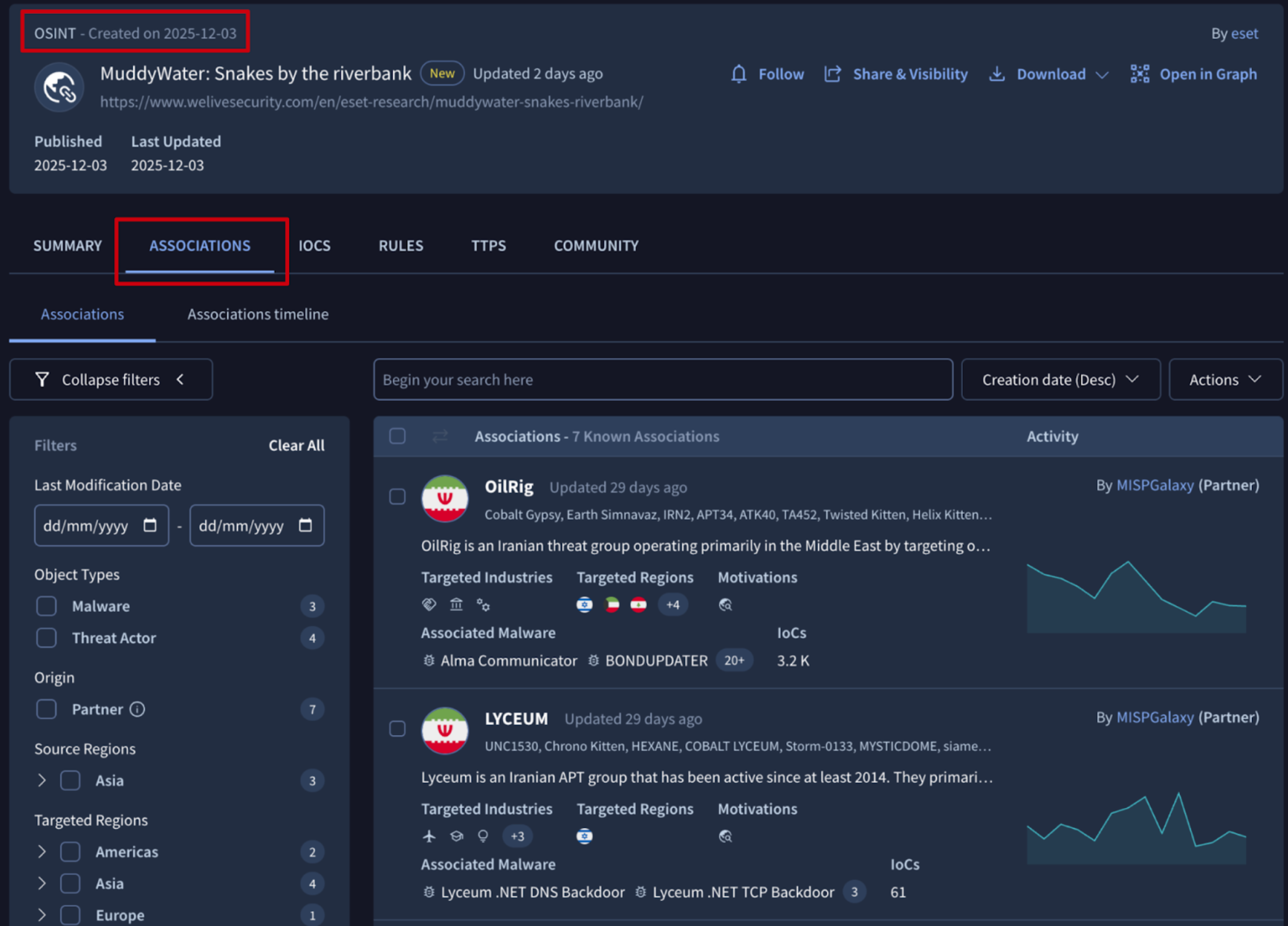
💪 Improved OSINT articles context. OSINT threat intelligence articles are sourced and integrated automatically from a collection of pre-vetted, reliable publishers, or ingested by users. These articles serve as an invaluable asset for threat intelligence, converting a massive volume of publicly available threat information into contextual, high-value, and immediately usable insights. This enables security teams to engage in proactive defense measures and inform their strategic security planning. Now the OSINT articles are associated with Threat Actors and Malware Families as curated reports are, significantly enhancing their utility by providing direct links to relevant entities within the threat landscape, making it easier for analysts to track and understand campaigns, tooling, and adversaries.
See example.