December 1st, 2025 - Agentic Prompt Tagging + Searches, and new Curated Detection Rules
📢 Google TI Mondays & Month of UNLIMITED UI Searches. Quick reminder that for the entire month of November, all Google Threat Intelligence and VirusTotal customers will benefit from unlimited, uncapped searches when performing manual queries through the web interface (GUI) using the core VirusTotal / GTI search feature. Follow the Google TI Mondays and Month Of GoogleTI Search series across our social platforms every week for quick, actionable practitioner tips and product adoption advice designed to enhance your efficiency. These actionable tips are essential. #GoogleTIMondays, #MonthOfGoogleTISearch.
- Hunting LockBit 3.0 ELF Payload
- Tracking Gamaredon Infrastructure
- Geopolitical Hunting: Government Phishing
- Hunting AI Evasion & Prompt Injection
- Hunting Cobalt Strike C2 by User-Agent
- Malware Using Email Channels
- Submit Your Own OSINT to Google TI
💪 Detection highlights. This week, the Google Threat Intelligence Group and FLARE team consistently update Google TI's YARA rules. We’ve released YARA rules covering 3 newly tracked malware families and updated YARA rules for 6 existing families. This update prioritizes malware families actively observed in Mandiant incident response engagements, SecOps customer environments, and top GTI search trends.
As we track new malware families found through our research, we build and release detection signatures. Some recent examples include:
- HELLCAT.GO: a HELLCAT ransomware variant written in Go that is capable of encrypting files on local and network drives using the RSA and ChaCha20 algorithms. The extension .HC is appended to the file name for each encrypted file. HELLCAT.GO is also capable of spreading to other networked machines, using spot encryption for file types associated with virtual machines, killing specified processes and services, skipping specified files and directories, wiping event logs, and deleting volume shadow copies. It drops a ransom note titled README_HELLCAT.txt after the encryption process is complete.
- SHINYSPIDER: ransomware written in Go that uses RSA and ChaCha20 for encryption. An 8-character extension is generated for each encrypted file, and depending on the file size, files are either partially or fully encrypted. SHINYSPIDER is also capable of encrypting files on local and network drives, spreading to other networked systems, killing specified processes and services, wiping event logs, disabling hooks added by security tools and deleting volume shadow copies.
- ASHCLOUD: a disruption wiper utility and dataminer disguised as a security scan application that scans all connected drives for particular file-types, AES encrypts the file's content using a single AES session key and prepends the AES IV to the encrypted file, RSA encrypts the AES session key with an embedded public key, and exfiltrates the encrypted AES session key as well as the encrypted files to an attacker-controlled Dropbox. Once the data theft routine is complete, or immediately upon receiving a "skip_backup" command from the Telegram C2, ASHCLOUD uses secure deletion algorithms to irreversibly wipe the local files. Additionally, ASHCLOUD provides the ability to execute a command on the victim's system, allowing the attacker to maintain persistence and execute arbitrary system commands via a Telegram bot.
In addition to providing detection rules for new and emerging threats, we continue to update our detection systems for threats like LOCKBIT, MISTPEN, and SUO5. These updates ensure you have the latest indicators.
See latest malware family profiles added to the knowledge base and the complete list of curated YARA rules in our database.
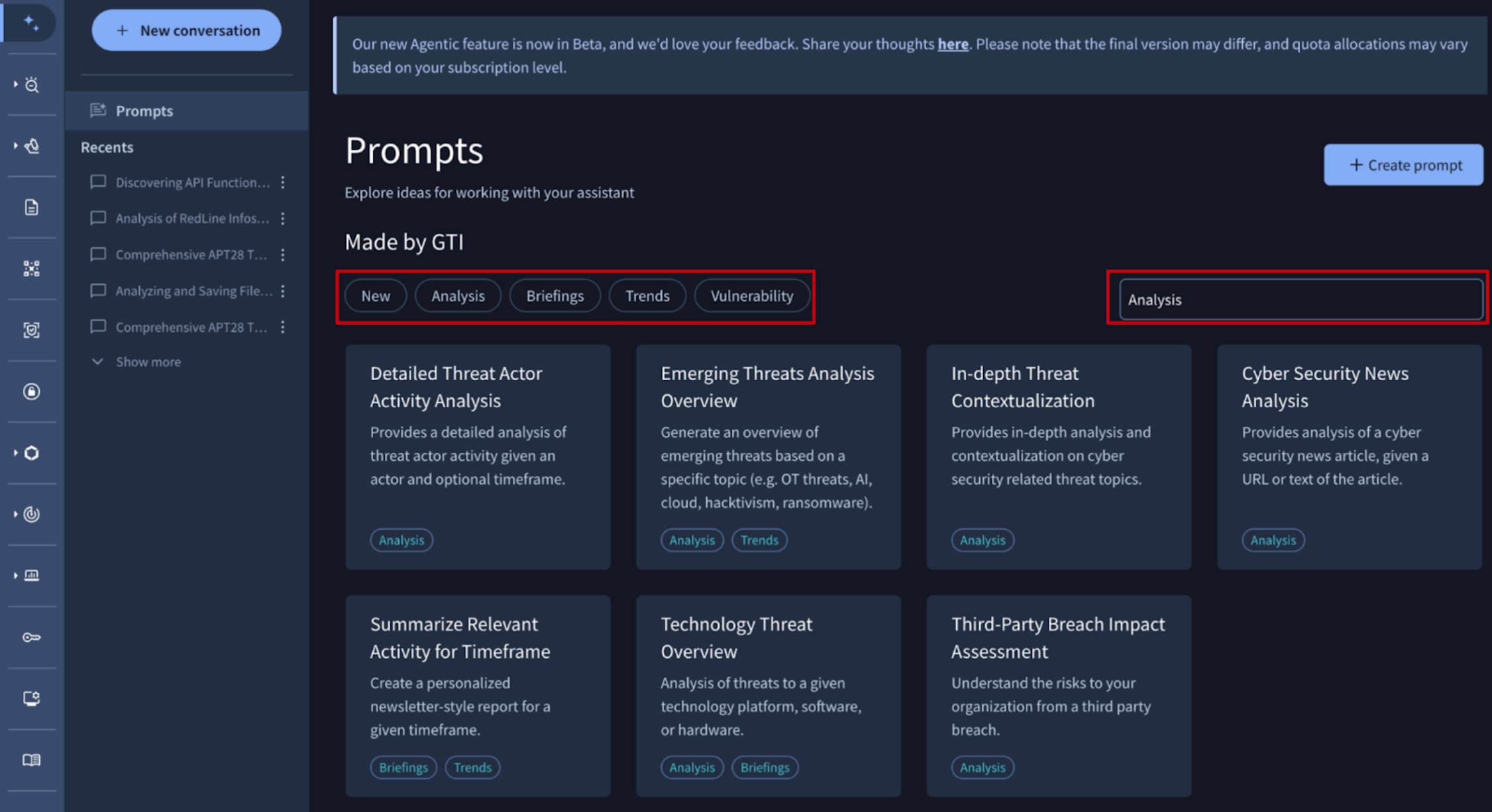
🆕 Tagging and Search for Agentic Prompts. Agentic Prompts are reusable query templates within the Agentic conversational AI platform. They allow security analysts to create standardized, structured instructions for the AI agents to automate and accelerate recurring threat investigation, malware analysis, and reporting workflows in Google TI. Users can now assign custom tags when creating or modifying an Agentic prompt. This feature introduces a new, powerful search and filtering capability in the prompt library, allowing analysts to quickly locate prompts based on criteria like Analysis, Briefings, Trends, Vulnerability and New prompts, or any other word from the prompt description.