December 15th, 2025 - NEW Ransomware Data Leaks endpoint exposed, last modification date URL search modifiers and more
📢 Google TI Mondays. Quick reminder to Follow the Google TI Mondays series across our social platforms every week for quick, actionable practitioner tips and product adoption advice designed to enhance your efficiency. These actionable tips are essential. #GoogleTIMondays
💪 Detection highlights. The Google Threat Intelligence Group and FLARE team consistently update Google TI's YARA rules and malware configuration extractors. This week, we focused on improving coverage for existing malware families. We updated 11 YARA rules and 2 configuration extractors. A few examples of families we updated our coverage for are: VIDAR, POISONPLUG.SHADOW, and GLUPTEBA.
These updates ensure you have the latest indicators that were extracted by our configuration extraction systems and YARA rules.
See latest malware family profiles added to the knowledge base and the complete list of curated YARA rules in our database.
🆕 Ransomware Data Leaks endpoint exposed. The Ransomware Data Leaks dashboard is our threat intelligence tool focused on aggregating data from numerous leak sites (DLS) to track extortion trends, victim volume, and active threat actor brands that serves as a strategic "command center" for cybersecurity teams. Now the new endpoint allows customers to programmatically retrieve the raw data powering the dashboard, enabling the seamless integration of ransomware intelligence into automated security workflows, custom reporting, and internal SOAR platforms. Our documentation provides practical examples to help you get started with this endpoint.
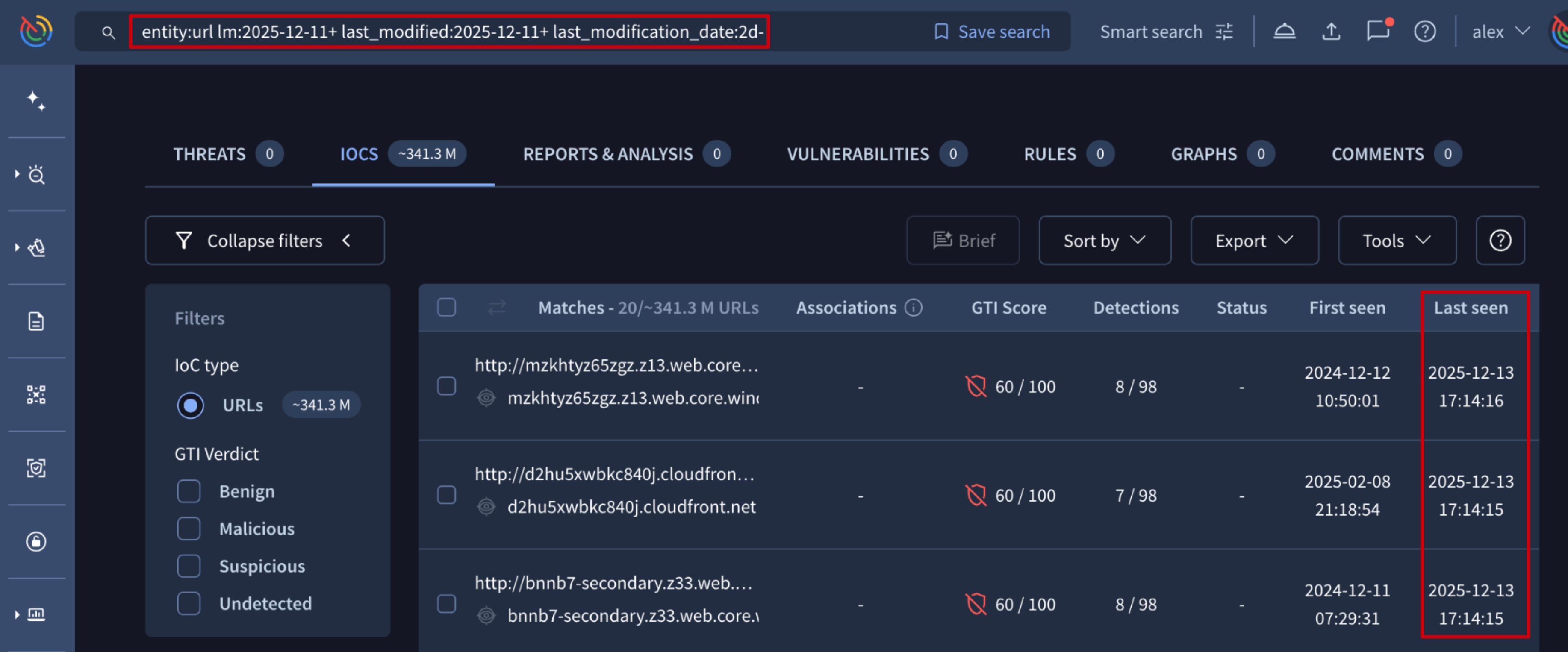
🆕 New URL search modifiers. The Intelligence Search feature allows users to execute complex and powerful queries against our expansive dataset of malicious indicators, enabling threat hunters to uncover infrastructure, track campaigns, and identify evolving threats. We have introduced three new search modifiers for URL entities: last_modified, last_modification_date, and lm. These modifiers allow analysts to filter URL indicators based on the exact time they were last updated in our database.
See example.